Placement
The first thing to consider when implementing an anti-spam package is where to place your anti-spam service. It can be installed as a mail relay (or on your mail relay if you already have one) on a dedicated server or as part of the Firewall services. It can also be installed on your Exchange server.
Catching spam mail before it reaches your Exchange server seems like a good idea at first because it reduces the load on your servers in terms of CPU and database size. However, you would need to train your help desk personnel to fetch quarantined items from the anti-spam server. No anti-spam package can guarantee no false positives, that is e-mails you want to receive that are quarantined by the anti-spam server.
This means that every time someone will not be receiving a promised e-mail from he or she will have grounds for calling up your help desk people asking for them to look for mail items that the anti-spam package stopped.
For small and medium businesses this might not be an option. Their typically overworked IT staff will not want to be dealing with quarantined e-mails. Sometimes IT services are outsourced, further complicating this. So this leaves installing the anti-spam mechanisms on the Exchange server itself. This enables some anti-spam applications to deliver mail tagged as spam to a specified Outlook folder instead of the Inbox. This enables the users should they choose to do so to examine by themselves their e-mail in case they suspect it was wrongly tagged.
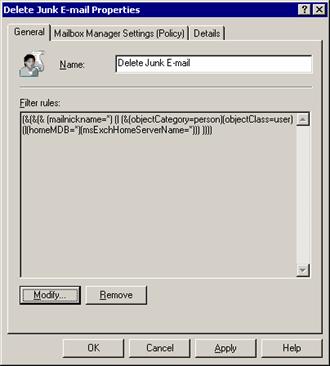
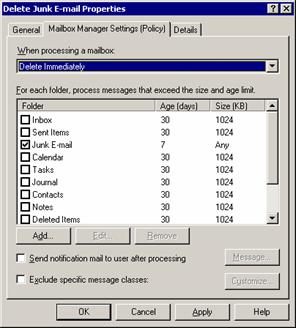
To complete this kind of solution I usually create a policy using Exchange System Manager that automatically deletes e-mail from the Junk E-mail folders of the users after seven days so that spam will not crowd the users’ mailboxes forever.
Whitelists
Whitelists are lists of valid senders. These can be created manually or automatically. Whitelists are useful to decrease the number of false positives and reduce the load on the CPU that is required for analyzing e-mails.
One way of automatically creating a whitelist is examining all outgoing mail. Recipients of mail sent from internal users are considered “safe” senders. This can be problematic if an internal machine starts sending e-mails because of a virus. Use this option only if you have anti-viruses deployed internally (as you should) and latest service packs are installed on the Outlook clients.
Another more sophisticated way examines the contacts folder of each mailbox to create the whitelist and requires read access to all mailboxes.
Blacklists
The Internet has servers hosting lists of known spammers. The use of these servers is essentially free. They are sometimes called Real-time Blackhole Lists or RBLs. I don’t want to disparage the good work of those involved in maintaining these servers but as time goes by their effectiveness declines. Myself, I do not use these in my installations of anti-spam applications.
Why is that? Today’s spammers spoof their e-mail so that they appear to come from a valid IP address and domain. Other spammers send each mail from a different random IP or e-mail address. This means that most servers listed today in RBLs are companies hit with viruses or Trojans, and those, being automated beings rarely send e-mails to my companies. Most target the most obvious sitting ducks such as Yahoo, Hotmail, AOL and the other big names in the online e-mail business. So using RBLs for me means that my customers cannot receive mail from companies IPs listed in the RBLs. It might take from 15 minutes to a week to get yourself off a RBL after you solved the problem, so basically this usually means that it takes longer for regular Joes who need the e-mail connectivity to resume it.
Header Checking
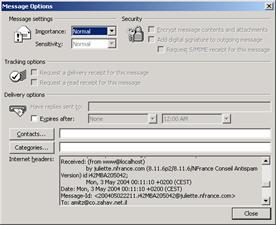
Headers contain information about the e-mail and its origin. To view an e-mail header in Outlook open an e-mail and choose from the menu Viewà Options. Under “Internet Headers” you can see the history for an e-mail delivery path.
E-mail sent from spammers can sometime be detected by determining characteristics common to spam mail. For example you can find out if the e-mail is coming from the server that is responsible for the domain of the sender and if the e-mail contains remote images, that is images not sent with the e-mail itself.
Even a simple rule such as determining how many digits are in the sender’s e-mail address can filter out a lot of junk e-mail. This considers that real people might sometimes include a year (four digits) in their e-mail address but spammers might include more since they rely on constantly changing e-mail addresses to a avoid simpler junk mail filters that rely solely on black lists.
Keyword Checking
This method is supposed to be very effective but a lot of sophisticated spammers constantly find ways to circumvent it, for example by replacing the letter “o” with the digit zero, or by deliberately misspelling words.
Yet, this feature is handy when you want to filter spam in languages other than English, and better control spam.
Some anti-spam packages have built-in keyword list. I would go over this list and delete words that might be relevant to your business related communications. For example, most lists contain the words “casino”, but you might not want to delete this if you provide services to a real casino.
Algorithms
Some anti-spam packages have special algorithms to determine whether a certain e-mail is to be considered spam. What these algorithms do is analyze and compare incoming and outgoing mail with a database of know e-mail spammers. These algorithms usually require a certain amount of valid e-mail traffic (also called HAM) to create its database. This database is compared with known SPAM attributes found in unsolicited bulk e-mails to decide whether an e-mail is valid or not.
The name Bayesian filter is now a catch-all phrase for all companies using statistical analysis to determine whether mail is SPAM. The algorithms used are based on the work of Reverend Thomas Bayes (1702-1761), a mathematician who first used probability a means of calculating, from the number of times an event has not occurred, the probability that it will occur in future trials. You can read all about this algorithm in the following link:
http://www.paulgraham.com/spam.html
GFI (known for their Exchange Spam Filter GFI MailEssentials) also has a nice article about Bayesian anti-spam filters:
http://www.gfi.com/whitepapers/why-bayesian-filtering.pdf
IMF
Microsoft now provides its own free Anti-spam package for Exchange 2003 named Intelligent Mail Filter (IMF) downloadable here:
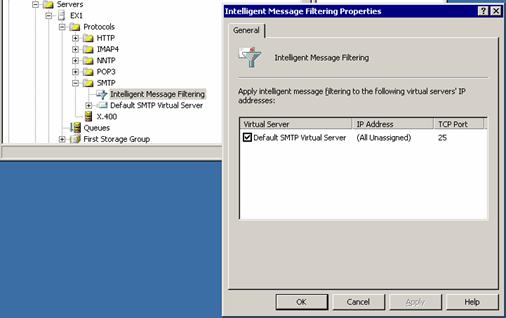
It seems like the easiest spam package to configure. With just the following dialog box in the Exchange System Manager to enable it:
A single dialog box in Exchange System Manager configures IMF:
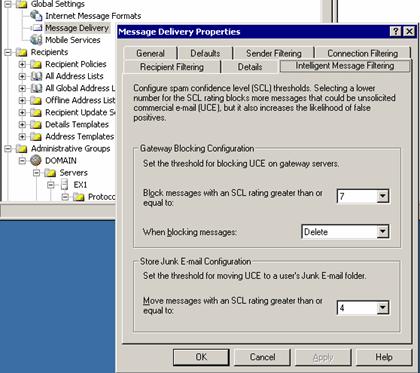
The settings provided here are the best we could come up with but they may vary. I’ve test IMF on a couple of Exchange servers and it works well. However, it does not really work for companies with a high rate of spam mail seeing that it lacks some of the options that more sophisticated ant-spam programs do.
Conclusion
Configuring anti-spam packages needs to be tailored to your needs and requires some knowledge of mail. Enabling all the features will simply not cut it since it might provide more false positives than necessary. You can’t block all the spam mail as you cannot totally prevent false positives but understanding how anti-spam works can help you manage spam enough to make your life easier and you’re the company employee’s happy.