
Source: Pexels
Google has released a report, Perspectives on Security, in response to the rising number of software supply chain attacks. The report outlines the latest security vulnerabilities in the open-source software supply chain, and how governments and companies can address them.
Google released the report on the second anniversary of the SolarWinds attack that had targeted government and private business entities in the US. Clearing up the malicious code from that attack cost nine federal agencies and over 100 private companies USD 100 billion.
Because vulnerabilities in the software supply chain can affect everyone across the board, the report calls for contributions from both federal agencies and commercial entities. A recommendation in the report also urged governments to “consider additional investment in initiatives to improve the security of the ecosystem as a whole.”
What Are Software Supply Chain Attacks?
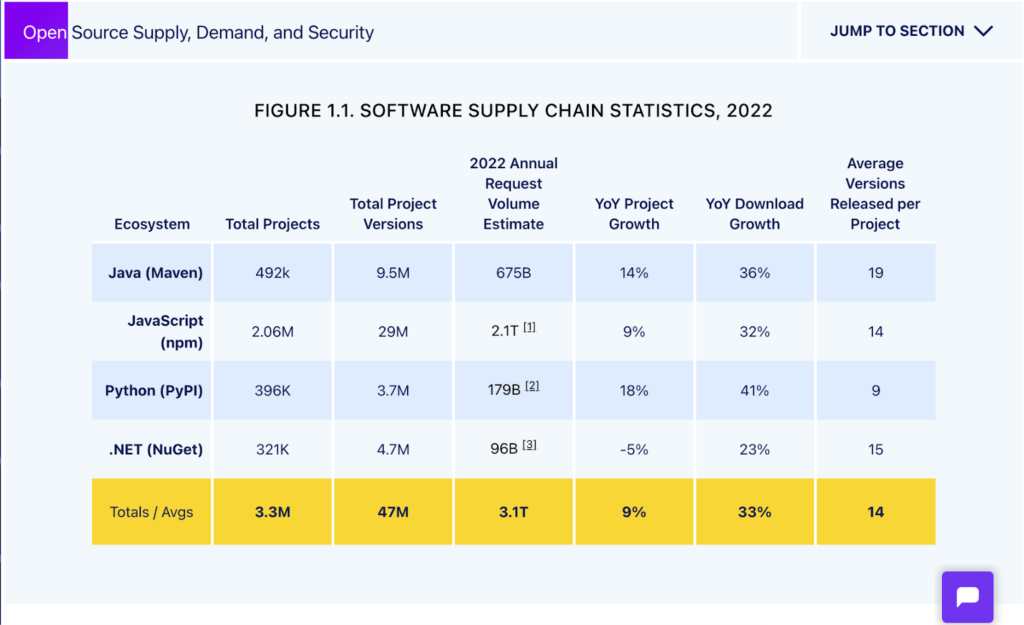
Source: Sonatype
Software supply chain attacks occur when threat actors compromise software during its production cycle by infiltrating any number of providers with access to it. Supply chain attacks are so worrying because they infect entire ecosystems. The recent vulnerabilities in AMI BMC components relate to hardware, but they’re a good example of how any vulnerability in the supply chain affects a large percentage of customers.
With access to a third-party vendor, cybercriminals can exfiltrate hundreds of thousands of customer records. But with open-source software attacks, cybercriminals can do much worse than that. They can create dependency confusion by spoofing an open-source development package with a higher version number. In 2021, open-source dependencies in software grew by 71% and have grown by 33% in 2022.
Cybercriminals may also compromise supply chains by typosquatting. Under this technique, a cybercriminal uses a well-known provider’s name to trick developers into using a slightly misspelled malicious software package. This creates an upstream dependency error, meaning the compromised software package affects every entity down the stream.
Alongside SolarWinds, Log4j is another security exploit cited in Google’s report. One of the most severe security vulnerabilities ever found, Log4j was simple to execute, public, and remotely accessible. As an open-source Java logging library developed by the Apache Foundation, Log4j was used by enterprise applications and multiple cloud providers. Attackers behind the Log4j attacks targeted over 44% of corporations worldwide.
Software Supply Chain Attacks Threaten All Sectors
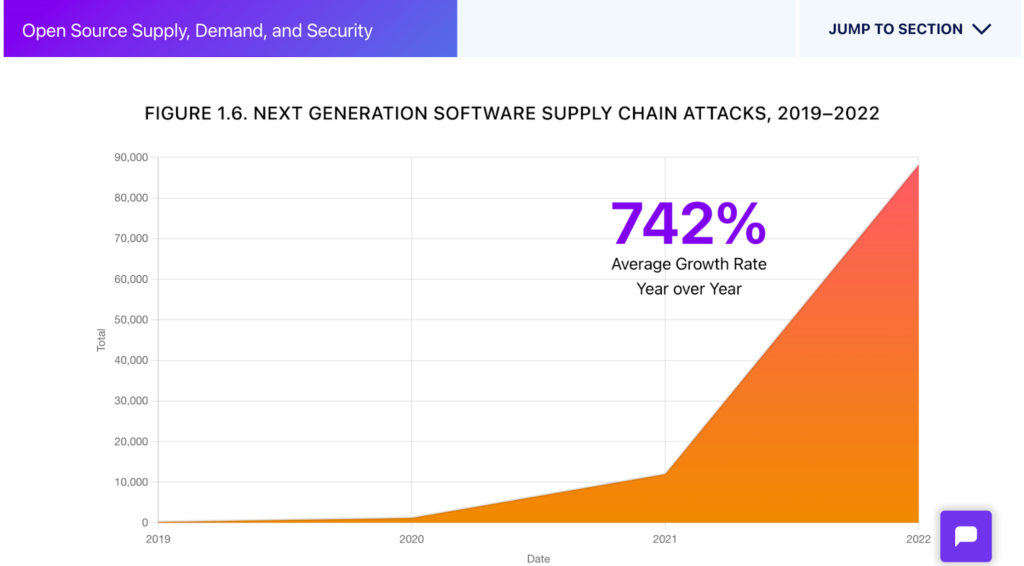
Source: Sonatype
Sonatype reported a 742% increase in software supply chain attacks over the past 3 years, establishing it as a huge cybersecurity risk. That’s why it’s important to form collective defenses. The software development process is complex and vulnerable, with “internal or external dependencies, open source elements, and…different products, services, people and organizations…” Given all that, it’s no surprise these “…dependencies are several levels deep.”
Due to this multi-layered dependency, a security vulnerability in one area can expose numerous other systems. Therefore, scanning and patching security vulnerabilities is key to securing any network. And, it’s even better to automate vulnerability scanning and patch management.
Apart from these security protocols, the Google report is calling for wider collaboration between open-source contributors, industry, and government. Through collective effort, they can holistically tackle the supply chain vulnerabilities
Google Releases More Tools for Protecting Software Supply Chains

Source: Pexels
Supply chain attacks require different security protocols than the ones used for simple code exploitations and user privilege escalations. In the report, Google recommends the Supply-Chain Levels for Software Artifacts (SLSA) framework as the main defense mechanism against software supply chain attacks. SLSA is an open-source framework that has a standardized series of controls to protect the software supply chain.
Google has been using SLSAs in its production environment for over a decade now, with forums like VMware and RedHat also using the framework to secure their software supply chains. Google has also launched its Software Delivery Shield, which provides Google Cloud with end-to-end supply chain security. And complementing the SLSAs in protecting the supply chain, Google launched its Graph for Understanding Artifact Composition (GUAC).
Shortly after the software supply chain report, Google released its Go-Based Open Source Vulnerabilities Scanner (OSV-Scanner) tool, supporting over 16 ecosystems, including Linux, Android, and Debian. This tool will allow for easy cross-referencing between known software vulnerability databases with software development libraries. In doing so, engineering teams will be able to easily identify such vulnerabilities beforehand.
A Unified Front Needed
Given the interconnectedness of modern software, Google’s call to governments and industries to collaborate in protecting the supply chain makes sense. Software supply chains need unified standards and protocols to protect them.
With a single compromise, at any stage in the software supply chain cycle, cybercriminals can tamper with software packages and run coordinated attacks down the stream. The attacks could then compromise customer records and data stored on cloud providers. Even worse, they can gain remote access through admin tools.
Therefore, these standards are a necessity. And that’s especially true with the Internet of Things and machine-integrated economy on their way to greater adoption. Open source agencies, working alongside government policy-makers and companies, must implement these protocols without any delays to secure the software supply chain. After all, an organization is only as strong as its weakest link.



