
Source: Pexels
The Lake Charles Memorial Health System (LCMHS) in Louisiana was hit with a ransomware attack in October, compromising almost 270,000 patient records, the hospital sources confirmed on Dec. 22. Hive ransomware group has claimed responsibility. However, the files leaked couldn’t be fully verified.
“We reviewed these files and determined that some patient information was contained within them, which may have included patient names, addresses, dates of birth, medical record or patient identification numbers, health insurance information, payment information and/or limited clinical information regarding care received at LCMH,” read the official update from the hospital.
The hospital started sending notices on Dec. 23 to those affected by the breach detected on October 21. The update also informed that some social security numbers were leaked, offering the affectees complimentary credit monitoring and identity theft protection. Barring all that, the Hive group couldn’t access the Electronic Medical Records.
Joint Advisory’s Findings about Hive Ransomware
Source: CISA
Hive reported that it encrypted the hospital data on Oct. 25, four days after the initial detection. Hive then posted a link to the LCMH data on its site on Nov. 15 after ransom negotiations broke down.
According to a joint Cybersecurity Advisory (CSA) issued by the FBI, CISA, and HHS, Hive has extorted over $100 million in ransomware payments from over 1,300 organizations. The advisory details that Hive uses a ransomware-as-a-service (RaaS) model for attacks.
From June 2021 to November 2022, Hive targeted commercial and critical infrastructure services, such as government facilities, manufacturing, communications, IT, and especially healthcare and public health services.
When infiltrating networks, the group uses single-factor logins via Remote Desktop Protocol (RDP) and virtual private networks (VPNs). In some instances, they’ve also gained access through multi-factor authentication by exploiting common vulnerabilities and exposures, such as CVE-2020-12812.
The cybercrime group also uses phishing emails to get hold of personal information. Moreover, the group exploits Microsoft Exchange vulnerabilities, such as CVE-2021-31207 (Server Security Feature Bypass Vulnerability), CVE-2021-34473 (Server Remote Code Execution Vulnerability), and CVE-2021-34523 (Server Privilege Escalation Vulnerability).
Defending against Hive Ransomware
Source: CISA
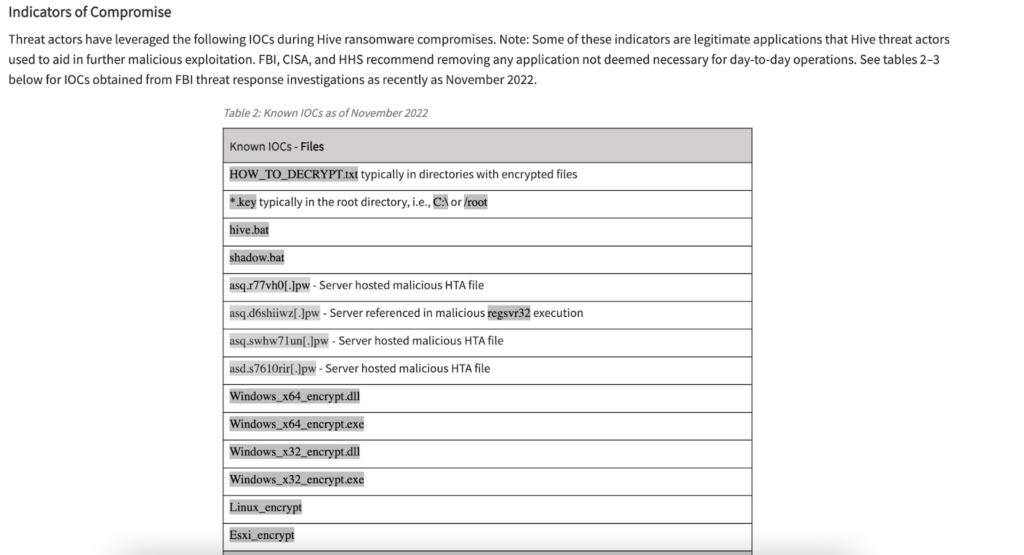
The advisory further lays down a list of known indicators of compromise (IOCs) that Hive leverages in its operations. Besides these, the advisory highlighted several suspected IP addresses, attack methods, and security mitigation procedures.
Regarding security strategies, the advisory recommends phishing-resistant MFA, frequent updates and patching, the securitization of RDP, and multiple pointers on password management. It also recommends businesses remove any applications that are not essential for daily operations. Hive typically targets Windows systems but can also target Linux, VMware ESXi, and FreeBSD systems.
For more comprehensive security, administrators should segment networks to prevent the spread of ransomware. Since the advisory goes into a lot of detail about these measures, administrators will do well by poring over them in depth to ensure the safety of their networks against Hive ransomware.
Here’s a quick recap of the mitigation measures from the advisory for network administrators:
- Maintain offline backups of data
- Ensure all backup data is encrypted, immutable, and covers the entire data infrastructure
- Monitor cyber threat reporting regarding the publication of compromised VPN login credentials
- Install and regularly update antivirus or anti-malware software on all hosts
- Enable PowerShell Logging including module logging, script block logging, and transcription
- Install an enhanced monitoring tool, such as Sysmon from Microsoft
Cybercriminals Continue to Find Healthcare a Soft Target
Source: OCR
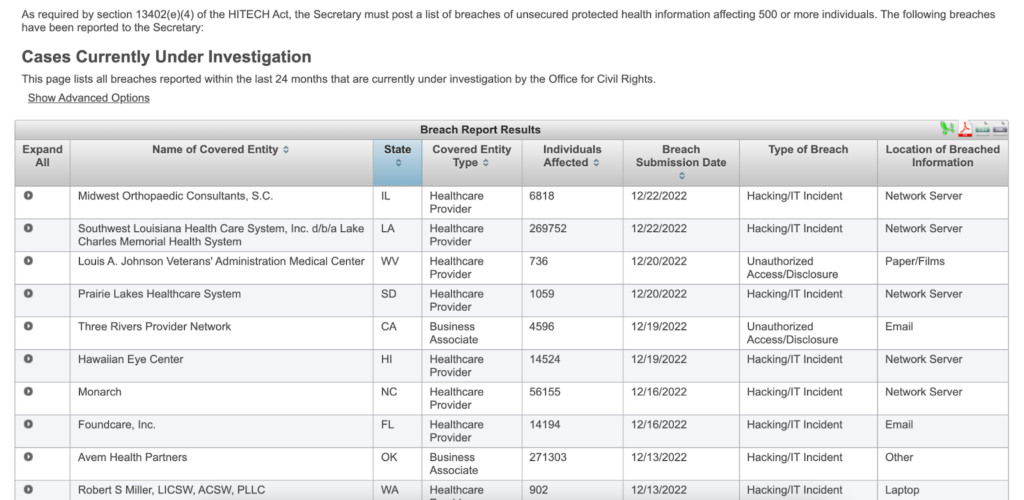
LCMH becomes one of many healthcare centers that have experienced a relentless onslaught from Hive. Under 13402(e)(4) of the HITECH Act, the US Department of Health and Human Services maintains a registry of all medical breaches that affect more than 500 people.
Barely a week goes by without the HHS reporting a breach affecting tens of thousands of patients. Among the looted information are the breached entities’ names, states, entity type, number of affected individuals, submission date, breach type, and location.
Hive is notorious for targeting healthcare. In 2021, the group attacked four healthcare facilities in the US. In the aftermath of an attack on a Missouri-based medical center, they stole and posted information that also included social security numbers.
Later, in March, Hive ransomware stole 850,000 personally identifiable information records from California’s Partnership HealthPlan (PHP). In Aug. 2021, Hive attacked the Memorial Health System in Ohio, forcing the staff to work from paper charts and disrupting surgeries.
Healthcare facilities accede to ransom demands more quickly than other sectors because of the valuable and extensive data they hold. Unfortunately, at times, these attacks have more than merely economic consequences. In 2019, a ransomware attack on Springhill Medical Center compromised a heart-rate monitor, resulting in the death of a baby.
The Aftermath of a Ransomware Attack
In many instances, the aftermath of ransomware is worse than the initial attack. Malware traces could continue existing in the system, requiring complete reconfiguration to eliminate previous security vulnerabilities. Once cybercriminals infiltrate a network, it needs an overhaul. This results in huge costs, to say nothing of the public relations disaster the fallout usually brings, leading to loss of customers.
In cases of ransomware, it’s best to adopt preventive practices than to put out fires amid an attack. Most forms of ransomware occur from attachments opened through email phishing. Businesses need a robust email policy alongside powerful antivirus software to prevent phishing attacks. As the advisory recommended, MFA also provides an added security blanket across your services.
The FBI discourages giving in to ransom demands, but at the end of the day, the business hit will decide if they pay or not. Groups like Hive are extortion rackets that offer no guarantees for the safe return of your data even if you pay the ransom. Besides the downtime costs such attacks cause, cybercriminals can get emboldened to ask for more if their victims just give in to their demands.
It’s sometimes possible to decrypt the files without paying the ransom if the group has made errors. But with veteran cybercriminals like Hive ransomware, this is unlikely. Still, you could ask for a cryptography specialist to help decrypt files.



