Sponsored by Specops Software
One of the most important things that organizations can do to protect their user accounts is to require multifactor authentication. But what is multifactor authentication and how does it work?
As you are no doubt aware, the vast majority of computer systems are secured with usernames and passwords. Although passwords have been the go-to mechanism for authentication control for over half a century, there are inherent weaknesses tied to password use. We’ve probably all heard stories, for example, of users writing passwords down, or worse yet, sending a password by email. Similarly, passwords can be stolen through shoulder surfing (looking over someone’s shoulder as a type the password), keyloggers and other malware, and by countless other means.
Password theft: Bad — and getting worse
Although password theft has always been an issue, it has become far more problematic in recent years because server criminals have begun compiling massive dark web databases of stolen passwords. The problem has become so pervasive that Specops maintains a master list of billions of leaked passwords sourced from thousands of stolen password databases.
All of this is to say that passwords simply do not offer the same level of protection that they once did. It has simply become too easy for stolen passwords to be shared among cybercriminals and used for nefarious purposes. Even so, the concept of passwords is so heavily ingrained in modern computing that passwords simply are not going to go away anytime soon. That’s where two-factor authentication comes into play.
Two-factor authentication is based on the idea that passwords alone do not prove a user’s identity. If someone were to log into a system using a username and password, there is no way of knowing whether those credentials were entered by the authorized user or by a cybercriminal who somehow managed to steal those credentials. As such, a second means of authentication (the second factor in the phrase multifactor authentication) is used to help prove that the user who is logging in is who they claim to be.
Multifactor authentication exists in a variety of different forms. At a high level, it works by requiring a user to use two completely different methods to prove their identity. These factors of authentication are usually based on something that the user knows (such as a PIN or password), something that the user has in their possession (like a smartphone or other electronic device), and something unique to the user’s body (like the user’s fingerprints or face).
If this concept seems somewhat abstract, then consider the various ways that Microsoft allows users to log into Windows. As you can see in the screen capture below, users can sign in using facial recognition or fingerprints (which are unique to each user). Users can also log in using a PIN, password, or picture password. These are all examples of something that the user knows. Additionally, users can sign in with a physical security key (something that the user has in their possession).
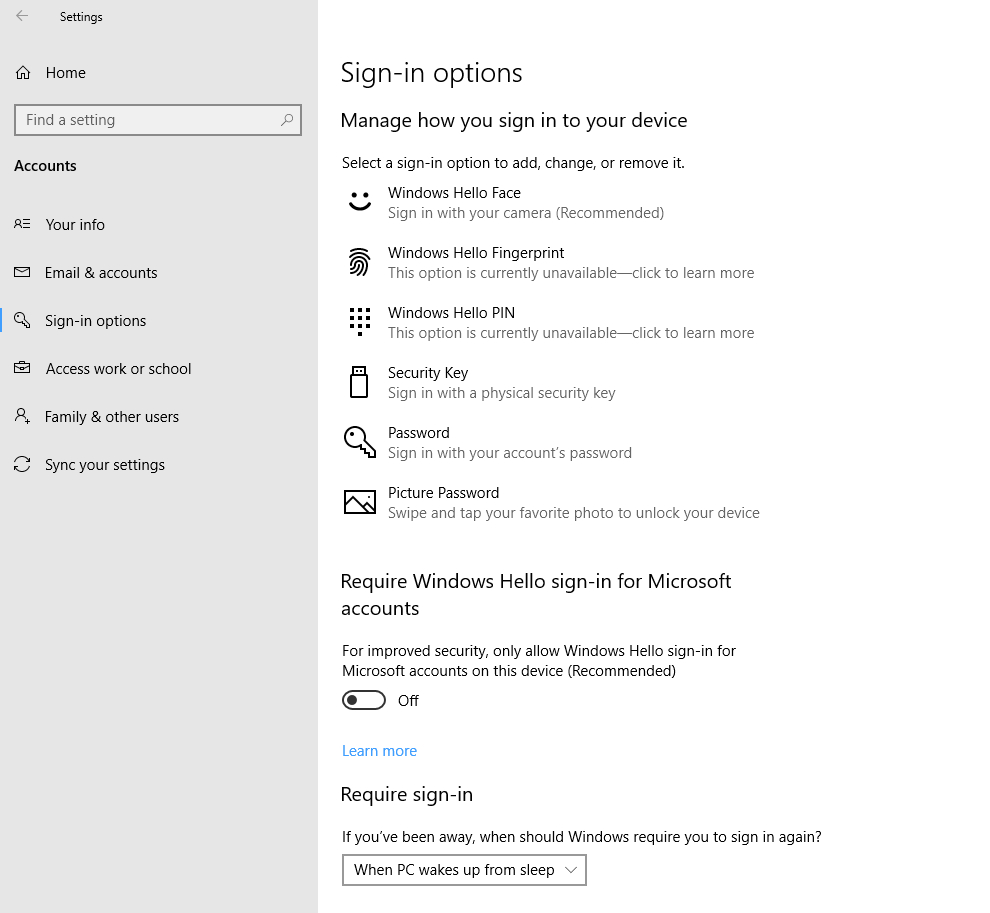
Windows supports a wide variety of authentication mechanisms
It is worth noting that none of these authentication mechanisms represent multifactor authentication by themselves. For an authentication process to be considered multifactor, it must involve two or more authentication methods. Even so, the sign-in options that are shown in the screen capture above are commonly used in multifactor authentication solutions.
There are countless examples of ways that multifactor authentication is used in the real world. When you go to a store and pay for a purchase using a debit card, for example, you are using multifactor authentication. Remember, multifactor authentication requires at least two forms of identity, based on something you know, something you have, or something you are. Your debit card is something you have, and the PIN you must enter to complete the purchase is something that you know. If you could complete the purchase simply by inserting your debit card, it would be difficult for the bank to figure out if you were making the purchase or if the purchase was being made by a criminal with a stolen card. Even if your card was stolen, however, it is unlikely that the criminal will also know your PIN, which is why the PIN makes for a good second factor of authentication.
Multifactor authentication is also sometimes used when you log into a website. After entering your username and password, the site may send a code to your smartphone, which you must then enter into the Website. This proves that you not only know your password but are also in possession of your smartphone. Hence the authentication process is based on something that you know (your password) and something that you have (your phone).
Multifactor authentication and password resets
It’s easy to think of multifactor authentication as being one of those things that is exclusive to the login process. However, multifactor authentication also needs to be incorporated into password resets. Otherwise, it might be possible for a cybercriminal to exploit the password reset process to gain access to the account. Specops uReset integrates an extensive multifactor identity verification process into the password reset workflow. It supports a huge range of identity providers and allows users to securely prove their identity in the way that makes the most sense in a given situation.
As previously mentioned, multifactor authentication solutions are often based on sending a code to a user’s smartphone. The problem with this is that not everyone has a phone. Similarly, a user might not have their phone with them at a given moment. In these types of situations, Specops uReset allows the user to choose from various other means of proving their identity (the software also supports using a smartphone as an authentication factor). That way, the user’s identity can be positively established in a way that adheres to the organization’s guidelines.
Featured image: Shutterstock



