If you read this excellent tutorial by Mitch Tulloch when it was first published back in January, you would have been better prepared for what happened when the world changed just a few weeks later. In this article, Mitch and tech consultant Richard Hicks take a deep dive into Windows 10 Always On VPN. As COVID-19 began to upend lives in March, businesses frantically searched for ways of securing their newly remote workforces — and VPNs topped the list of must-have solutions. This step-by-step guide is even more relevant now than it was in January, which is why it is on our list of the 20 Best of 2020.
As I’ve mentioned in many previous articles, my work in our content development business frequently requires that I remotely access secure corporate networks of various partners and vendors as I write whitepapers for them or develop documentation, courseware, or other technical collateral they need. The most common method I’ve used for doing such remote work is to use virtual private networking (VPN) solutions business partners operate or recommend, and the Windows solution in this area called Always On VPN is becoming a favorite for many of these companies since support for the client-side of these technologies is included in the Windows 10 operating system. Well-known enterprise infrastructure and security expert Richard Hicks has previously walked us through how to deploy and configure Always On VPN in Windows 10 here at TechGenix.
But deploying a VPN solution by itself isn’t the be-all and end-all of making sure your remote employees or contractors can securely access your corporate network. Fortunately, multifactor authentication or MFA can help strengthen the security of your VPN solution by making it more difficult for malicious actors to impersonate legitimate users. For companies that use the Microsoft Azure cloud platform, there is Azure MFA, which Anderson Patricio, one of our TechGenix team of authors, has previously walked us through using to set up MFA for accessing the Azure portal. Another of our TechGenix authors, Lavanya Rathnam, has also written this step-by-step guide for us about using MFA for Office 365, which is a subset of Azure MFA, but it comes at no additional cost, and you can manage it right from Office 365 portal.
To ensure that remote work can be performed securely when accessing corporate resources over a VPN, I asked Richard to build upon his previous walkthrough by showing us step-by-step how Azure MFA can be integrated with Always On VPN in Windows 10. Richard is the founder and principal consultant of Richard M. Hicks Consulting and focuses on helping organizations implement edge security, remote access, and PKI solutions on Microsoft and third-party platforms. He is a Microsoft Most Valuable Professional in the Cloud & Datacenter and Enterprise Security award categories and can be found on Twitter at @richardhicks.
‘Crucial security risk’
Richard started by saying that there is a “crucial security risk” associated with remote access technologies because of the potential of lost or stolen credentials. “If an attacker can obtain valid credentials with authorization to connect remotely, they can easily gain network access to steal data or further comprise the network. Additional controls must be put in place to address this risk,” he said. I asked him to expand on this and describe the issues involved in integrating Azure MFA with Windows 10 Always On VPN, and he replied with a short bullet level list as follows:
- Certificate authentication: Digital certificates are recommended to authenticate remote users instead of usernames and passwords. This mitigates the risk of lost or stolen credentials being used to access the network surreptitiously. Using certificates for authentication, an attacker will not be able to connect to the VPN remotely even if they have obtained valid credentials.
- Lost or stolen devices: While using client certificate authentication mitigates the risk of an attacker using lost or stolen credentials to gain access to the network, it does not help if a portable device (laptop or tablet) is lost or stolen. In this scenario, the attacker owns the physical device that includes the certificate, allowing them to gain remote network access.
- Multifactor authentication: For the highest level of assurance, a multifactor authentication (MFA) solution should be deployed to address the risk of compromised user credentials (stolen certificates) and lost or stolen devices. With MFA configured, an attacker with valid credentials and even the physical device, including certificate, will still not be able to gain access without additionally gaining access to the MFA token assigned to the user (typically their mobile phone).
- Azure MFA: Microsoft Azure MFA is an excellent choice for adding MFA to an Always On VPN deployment. Azure MFA integrates with existing on-premises network policy server (NPS) servers and provides strong user authentication for remote workers. In addition, Azure MFA has the added benefit of supporting MFA when using EAP and client certificate authentication.
- Requirements: To use Azure MFA, you must have a valid Azure subscription and be using Azure AD Premium. Also, Azure AD Connect must be configured to synchronize on-premises Active Directory users to Azure AD, and users must have an authenticator application provisioned.
NPS integration a key
Richard said next that NPS integration was the key step in getting Azure MFA set up with Windows 10 Always On VPN. “Azure MFA integrates easily with Always On VPN deployments, by installing an extension on existing NPS servers,” he said. He then described the following to install and configure the NPS extension for Azure MFA. First, you must download and install the NPS Extension like this:
- Download the NPS extension for Azure MFA here.
- Double-click NpsExtnForAzureMfaInstaller.exe.
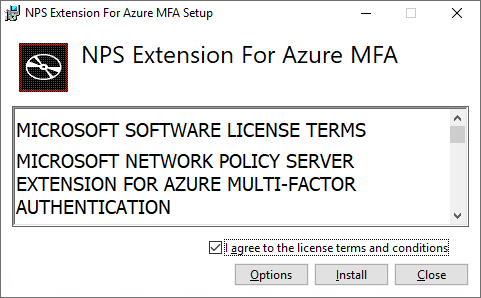
- Agree to the license terms and click Install:
Once the installation is complete, click Close:
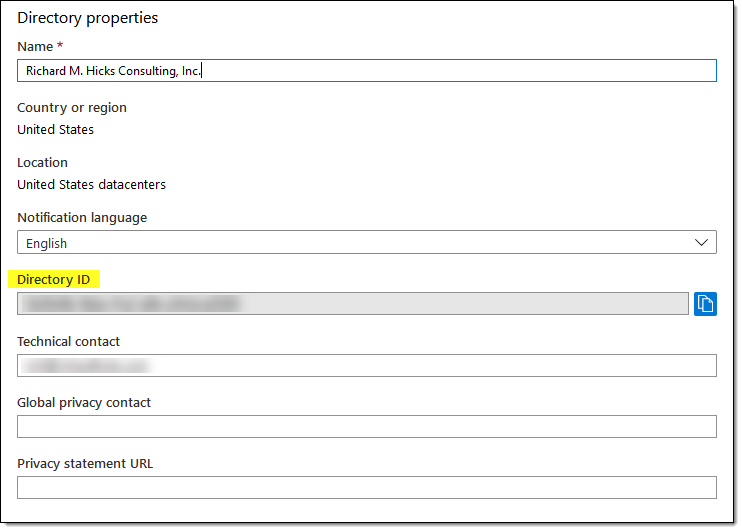
Next, you must configure NPS Extension Certificates. The NPS Extension for Azure MFA uses certificates to secure communication between the NPS server and Azure. Before you begin, copy your Azure Active Directory tenant ID as it will be needed later. You can find the tenant ID by opening the Azure AD management console and clicking Properties:
Once complete, return to the NPS server and follow the steps below to complete the configuration.
- Open Server Manager and click Local Server in the navigation pane.
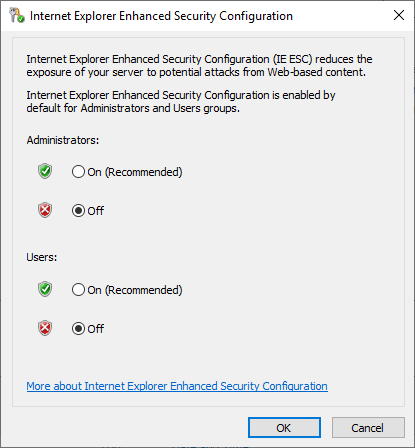
- Click the On link next to IE Enhanced Security Configuration.
- Select Off for both Administrators and Users.
- Click OK:
- Open an elevated PowerShell command window and navigate to C:\Program Files\Microsoft\AzureMfa\Config\.
- Enter .\AzureMfaNpsExtnConfigSetup.ps1 and press Enter.
- Enter Y to install the NuGet provider.
- Sign in with your Azure AD administrator credentials.
- Enter your Azure tenant ID.
- Press Enter to complete the configuration.
To ensure everything will work properly, Richard recommends that you perform validation testing at this point in the process. “With the NPS Extension for Azure MFA installed,” says Richard, “VPN client connections will now require the user to accept the MFA prompt on their Authenticator application.”
Integrating Azure MFA with Always On VPN: Final thoughts
Richard finished off our time together by providing some additional information that is important to keep in mind when integrating Azure MFA with Always On VPN.
- Be sure to install the NPS Extension for Azure MFA on all NPS servers authenticating VPN client requests.
- Once the NPS Extension for Azure MFA is installed on the NPS server, all authentication requests processed by the NPS server will require MFA. It is recommended that separate NPS servers with the extension be configured and dedicated to VPN client authentication requests to avoid conflict with other services.
- MFA only works with the Windows 10 Always On VPN user tunnel. Enforcing MFA for the device tunnel is not supported.
- After installing the NPS Extension for Azure MFA, the administrator may encounter failed VPN connection attempts. This can be caused by disabled Azure Multi-Factor Auth Client and Azure Multi-Factor Auth Connector enterprise applications. Click here for more details.
Featured image: Vector by Freepik