Industry experts anticipate cybercrime will cost businesses worldwide $10.5 trillion by 2025. That’s an average of $3.86 million per business! Sounds scary right! Besides financial loss, cyberattacks also lead to reputation loss. That, on average, can stay with your business for three years after the initial breach. You wouldn’t want that to happen either! In this article, we’ll look at how to stop cyberattacks with Intrusion Prevention Systems (IPS). These are systems every cybersecurity team and business owner should know about.
You’ll learn all about IPS and how it works. You’ll also find a list of the different types of IPS available to add to your business. That way, you can make an informed decision on which one is the best fit for your company.
Before we get to that, let’s consider why cyberattacks happen.
The Root Cause of Cyberattacks
The main cause for cyberattacks is often network security vulnerabilities. Cybervillains can leverage these weaknesses or flaws to sneak into your system. That enables them to achieve many exploits, like ransomware, malware, data breaches, and injection-based attacks. That means they arrange to launch attacks from within a target network’s safe zone.
A good way to secure your network and stop such attacks is to have an IPS. Its goal is to detect malicious traffic and prevent it from entering a network. That way, cyberattackers don’t stand a chance to exploit you.
Let’s now take a look at what IPS is and what it can do for your company!
What Is an Intrusion Prevention System?
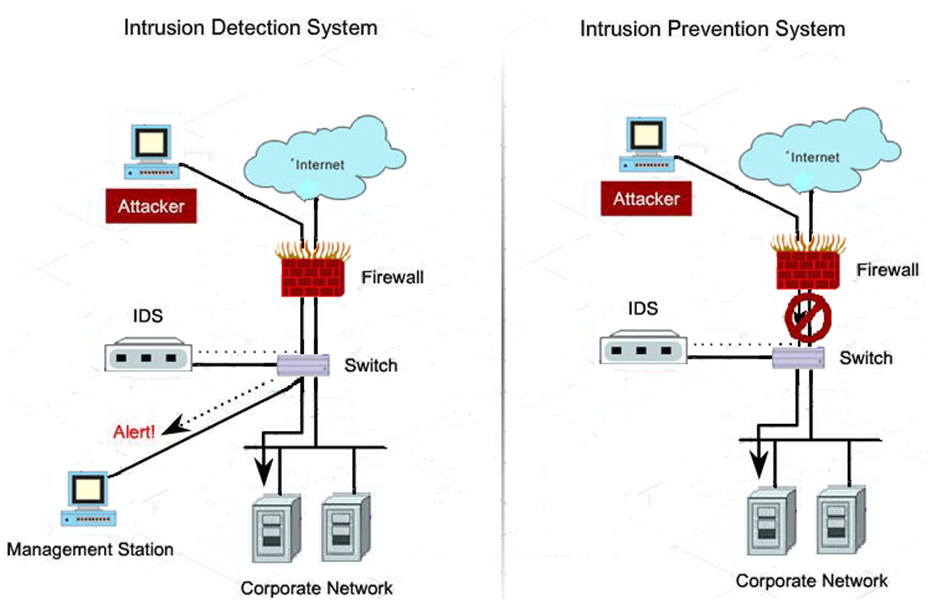
IPS is a network security solution that detects threats and unauthorized access. It sends alerts to your security team to help them prevent attacks. An IPS can also trigger actions like closing access points and changing firewall configuration.
IPS works like a combination of an intrusion detection system (IDS) and a firewall. Sometimes, IPS and IDS may be part of a network security solution that resembles a firewall. They compare the incoming network packets to a database of cyberattack patterns. If they find matches, both systems flag the packet.
Where did the database come from? Vendors often compile and update a database with the latest security threats. Some IPS vendors even include internet and Internet of Things (IoT) technology vulnerabilities in their lists.
You might say: so far, both IPS and IDS sound like firewall software. The only difference is its list of exploits added to a database.
It might seem that way; but first, let’s define how IPS functions. Then you can decide if it’s worth your time and attention.
IPS, IDS, and Firewalls
IPS is a data control system while IDS is a security monitoring solution. That means, if IDS finds an exploit match, it will flag the packet. To that end, it sends a notification to the security team.
IPS acts as a firewall, preventing a flagged packet from reaching the network. It also can automatically reject a packet based on a ruleset. In this sense, an IPS is proactive while an IDS reacts to threats only.
Since IDS and a standard firewall are similar, many software vendors integrate IDS into their systems. These go by Unified Threat Management solutions.
Now, let’s delve deeper into the workings of IPS.
How Do Intrusion Prevention Systems Work?
IPS is an active solution so you need to understand it to use it successfully. In this section, we’ll look at how these systems interact with data packets and what an IPS system offers as protection. Here is a step-by-step explanation of how it works.
Step 1: Analyze a Packet’s Contents
When a packet reaches the network, the IPS starts analyzing it. It looks at the packet information, like IP addresses and port numbers. Then it takes this information and compares it to the cybersecurity database. It’ll also check it against the company’s policies and rulesets. The database or policy contains the information about malicious ports and IP addresses. This step is like that of a firewall.
Step 2: Compare the Contents
Here’s where things start to differ. At this step, IPS checks if any database entry or ruleset matches the information in the packet to flag it as a concern. Here, a firewall would only examine the header, compare it against a ruleset, and flag it.
An IPS, though, compares the packet’s contents and its header. This enables it to spot cyberattacks.
Many cyberattacks, like Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks and viruses, have clean headers. It isn’t until you get to the content that you get hit with malware. That’s why an IPS is better to thwart various types of exploits than a firewall.
Step 3: Block the Malicious Packets
This is the final and distinctive step of an IPS. Once an it detects a malicious packet, it’ll block it or even the entire traffic to a port, depending on its setup. An IDS or firewall solution can’t block packets. This is what makes an IPS more effective in thwarting cybercrime.
IPS Isn’t Just for IT-Based Businesses
IPS solutions aren’t for IT-based businesses only. They also benefit companies in engineering. That’s not all, they integrate well into fully automated infrastructure. As for IT, IoT, and operations technology (OT) over multiple production sites, IPS integrates well with these systems. This is the case with ‘manufacturing 4.0’ enterprises.
IPS is also available for product lifecycle management (PLM) based business solutions. To top it, Oracle database-centric business solutions also exist and harness IPS to get better security.
It’s great to know that these types of IPS offerings are available. They make a company, with IoT and OT-integrated solution, more secure against cyberattacks.
Now that you know how the ins and outs of an IPS and its flexibility, let’s talk about the different types of IPS out there.
4 Types of Prevention
A handful of different IPS solutions exist in the marketplace. You’ll come across them when searching for the perfect IPS solution. Here we’ll tell you what they are and discuss what each has to offer.
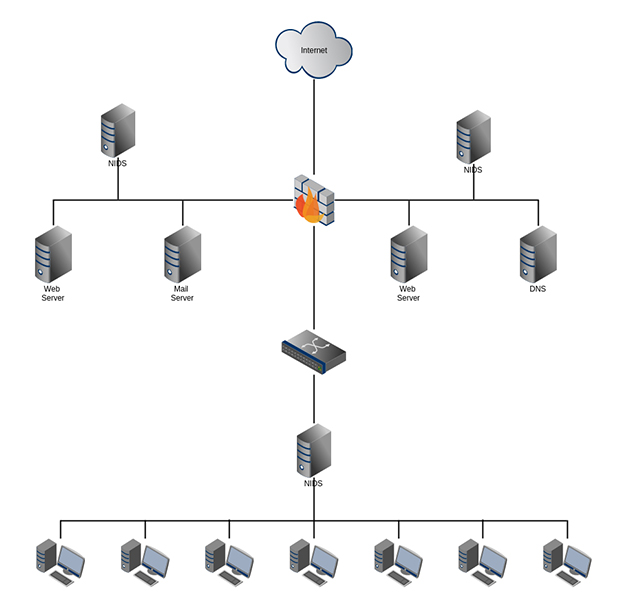
1. Network Intrusion Prevention System (NIPS)
A NIPS is a solution that has IPS software hosted on a discrete device. That way, you can install these devices at strategic network points. This allows them to scan all the network packets.
Larger companies, where departments need to be kept secular, can benefit from NIPS. This can include research-based engineering companies, defense manufacturers, or security-minded enterprises.
NIPS hardware includes Application-Specific Integrated Circuits (ASICs) and network processors. That allows these devices to deal with large traffic volumes. They can handle data throughput in real-time, as well.
2. Host Intrusion Prevention System (HIPS)
HIPS is best used to protect a network and its devices from malicious software. It’s comprehensive as it starts at the third layer of the Open Systems Interconnection Model (OSI model). The first layer of this model is the physical layer, and the last is the application layer.
This means a HIPS is great at assessing all packeted data. The comprehensive nature of HIPS makes it the last line of defense against an attack. It can detect even those packets that have managed to slip by an NIPS. This is why it’s typically installed at endpoints, like PCs, to examine traffic.
3. Network Behavior Analysis (NBA)
When you hear NBA, you directly think basketball; I get you.
NBA, here though, is a program that collects and analyzes network traffic. It uses the data to identify any malicious activity or data within the network. NBA gathers information from many sources and analyzes them using machine learning algorithms. These are typical of DDoS attacks and present one of their main use-cases.
The analysis doesn’t occur in real-time. Instead, the continuous use of an NBA helps to establish security benchmarks over time. This means the system identifies anomalies and escalates them based on historical data. That said, they don’t help prevent cyberattacks in real-time and are often used along with other types of IPS.
4. Wireless Intrusion Prevention Systems (WIPS)
WIPS monitors a company’s wireless network and radio spectrum. That way, it can identify unauthorized devices and access points. It then automatically prevents devices from accessing the network.
WIPS works slightly differently when compared to a wired IPS. A WIPS device relies on its antennas to scan data packets. This means they suffer the same setbacks as wireless technology like the inability to assess dead spots.
Now that you know your options, how can you select the best one for you?
Selection Considerations
Most companies prefer to use two or more of these IPS solutions to enhance their security. Here are some helpful tips for choosing the one that fits your company:
- Decide on the types of IPS and their adequate configuration
- Conduct a risk analysis to justify the implementation cost (note that some IPS software is freeware and open-source)
- Decide if you need pre-built detection rules (note that some IPS solutions come with these rules and can make your life easier during implementation)
- Choose the tools you need to generate reports for analysis, reporting, auditing, and compliance
Now you know the different types of IPS that can protect your network, how they work, and how you can integrate them into your networks.
Final Thoughts
IPS protects your network from cyberattacks and unauthorized access. It offers value-added inspection and prevention unlike firewalls and IDS solutions.
For one, they examine the header and contents of every incoming and outgoing packet. This differs from firewalls that only look at the header! If any data matches an existing rule set for an attack the IPS prevents the packet from entering the network. That compares to an IDS that stops at notifying the administrator or security team.
IPS is more advanced than both IDS and firewalls as it works to identify and deal with threats. This can include blocking some or all traffic going through a port or between different groups in the network.
Many types of IPS are available to help you secure different areas of a network. You can install these in various combinations based on your organization’s security requirements. Adding IPS to your network will help reduce cyberattack threats and counter rising cybercrime.
FAQs
Can an IPS protect your company from malware?
Yes, an IPS can protect you from malware. This happens when it examines the header and contents of every packet before allowing it into the network. That said, make sure you update your database or rulesets regularly to include the latest threats.
Are IDS and IPS the same?
An IPS is an advanced version of an IDS since it comes with extra capabilities to stop malicious packets. In this sense, an IDS is a diagnostic tool while an IPS is a control system.
Where can I place an IPS?
An IPS’ location should be at strategic entry and exit points in the network. This helps it prevent the entry or existence of malicious data packets in the system. That way, you can achieve internal protection between groups, depending on how you add the IPS.
What can an IPS do when it detects an attack?
Besides sending an alert, an IPS can drop packets and block the entire traffic for a port. For some cyberattacks, IPS can also reset connections to prevent service blockages.
What are the different types of IPS?
An IPS can be NIPS, HIPS, NBA, or WIPS. You can use any to protect a network or combine more than one for added protection.
Resources
TechGenix’s Cybersecurity Evolution Article
Read this article to understand how cybersecurity evolved to handle new attacks.
TechGenix’s Antivirus Software Article
Want to know the dependable antivirus software available today? Click here.
TechGenix’s Cybersecurity for an SMB Article
Are you an SMB looking to protect yourself from cyberthreats? Here is a must-read article for you.
TechGenix’s 2021 Security Breaches Article
Check out this article to get information on some of the biggest 2021 security breaches.



