For many, 2016 was a year of insanity, a fact not missed by those who work in InfoSec. We have seen over the past year a spike in powerful DDoS attacks, new types of ransomware encryption (namely against the hard drive), and many shady cyberattacks aimed at the infrastructure of numerous nation-states. DDoS attacks in particular made waves with unprecedented attacks coming from IoT botnets. While the most significant of these was the Mirai botnet, a recent DDoS attack proved that 2016 went out with a bang for black hats.
In a recent post, Imperva Incapsula researchers detailed the cause of a DDoS attack that occurred on December 10. The culprit was identified as the Leet botnet (for the “1337 leet speak” used by script kiddies) because of the “1337” message left in the TCP header. The DDoS attack was carried out in two separate bursts, the first of which lasted 20 minutes and generated a peak level of 400 Gbps. Following this, as the Imperva post states, “failing to make a dent, the offender regrouped and came back for a second round.” The second wave had “enough botnet ‘muscle’ to generate a 650 Gbps DDoS flood of more than 150 million packets per second (Mpps).”
Below is the reading in graph form of the DDoS attack as recorded by Imperva Incapsula:
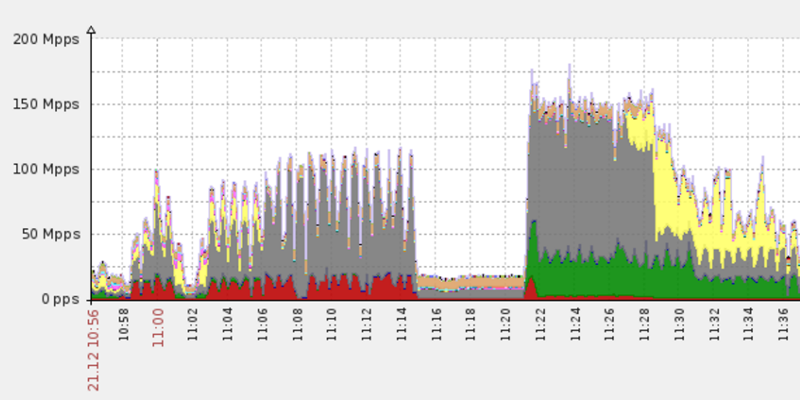
This attack also proved unsuccessful because of Imperva’s defenses, and the attacker ceased the DDoS soon after. What is significant here is the 650 Gbps flood, as this number is astronomical. It is not near the levels of the Mirai botnet, but since further analysis revealed that Leet is not a Mirai derivative, it is proof that IoT botnets are gaining in quantity while still increasing in power.
The source of the attack could not be determined due to IP spoofing, but in many ways this does not matter. What is far more significant is the observations that were able to be made by analyzing the packets, which showed that Leet is an entirely new botnet. What should be taken away from this is that 2017 will likely be host to countless brutal DDoS attacks, giving black hats a prime opportunity to breach their target of choice.
The Imperva report echoes this sentiment as they state that someone using a botnet like Leet “can circumvent signature-based security systems that mitigate attacks by identifying similarities in the content of network packets.” Of the many items on the 2017 to-do list for InfoSec professionals, bolstering defenses against powerful botnets must be one of them.
We cannot afford another Mirai incident.
Photo credit: Glutnix




The question is, why do they perform these kinds of attacks and how can we stop them? When I say “stop them” I don’t mean by blocking the attacks, but by finding the root of the problem, there must be a reason as to why people perform these kinds of attacks, if we understand why they do so then we might be able to solve their problem and stop them from performing these attacks once and for all.
It’s certainly a noble goal George. The thing is, speaking from experience, there are so many different reasons that pinpointing the root issue is difficult. Some black hats are after monetary gain, some want information, some want anarchy, some are just trolls having fun, and some are simply into hacking for the sake of hacking. It is definitely a discussion to be had though.