Researchers at TrendMicro and FireEye have identified a new ransomware strain that is a derivative of previous successful ransomware campaigns. Dubbed Magniber, the ransomware, which targets systems running Windows, is a descendant of the Cerber ransomware and is distributed via the same Magnitude exploit kit (EK) used in Cerber attacks (hence the name “Magniber”). As researchers note in their blog post, many forms of EK attacks have been on the decline since, but attacks with the Magnitude EK have been observed on a fairly consistent basis “particularly in the APAC region,” most notably South Korea.
See the below graph from the company to see the most affected regions:
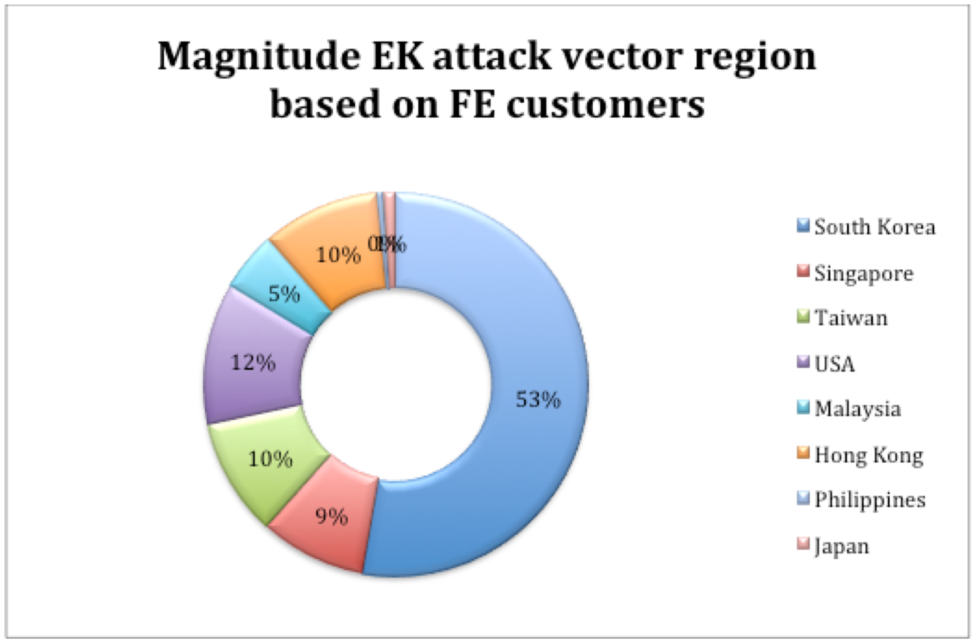
It is through the constant monitoring that, following a short drop-off in activity, FireEye recognized the new Magniber ransomware engaging in attacks around October 15. The EK attacks were more aggressive toward South Korea than they had ever been before, and a TrendMicro analysis of how Magniber attacks its targets revealed why. Per the report:
RANSOM_MAGNIBER.A and TROJ.Win32.TRX.XXPE002FF019), which we found targeting South Korea via malvertisements on attacker-owned domains/sites… appears to have become an exploit kit expressly targeting South Korean end users… Magniber will only fully execute if the installed language matches the locale identifier string 0x0412, which is the identifier for Korean.
Why the authors of Magniber have chosen to target the South Korea is unknown at this time. There is little information currently that indicate who the threat actors are. The ransomware, however, is a strong threat thanks to its AES128 encryption of files once the payload is deployed. Further analysis by FireEye researchers has shown that Magniber functions as follows:
The malware contains a binary payload in its resource section encrypted in reverse using RC4. It starts unpacking it from the end of the buffer to its start. Reverse RC4 decryption keys are 30 bytes long and also contain non-ASCII characters… After unpacking in memory, the malware starts executing the unpacked payload.
FireEye recommends updating all software as soon as patches are available, and making especially certain that network nodes are patched to help counter this EK attack.
Photo credit: Wikimedia



