Marcher malware on Android devices has been on the radar of security researchers for some time. Marcher malware is a powerful banking infection that steals online banking credentials and credit card info. Banking malware is nothing new, but Marcher has been employed in numerous creative ways in an attempt to cause infection, from faking mobile game downloads to pretending to be the Google Play Store.
The next variation of attack has surfaced in the form of a false Adobe Flash Player update. As explained in a detailed report from security researchers at Zscaler:
“We are seeing the malware payloads disguised as Adobe Flash player. Upon opening the dropper URL, the user will be prompted by a message saying the device’s Flash Player is out of date, and the malware “Adobe_Flash_2016.apk” will be dropped on the user’s device. The malware will also guide the user to disable security and allow third-party apps to install”
The download prompt looks fairly convincing as seen in the image below:
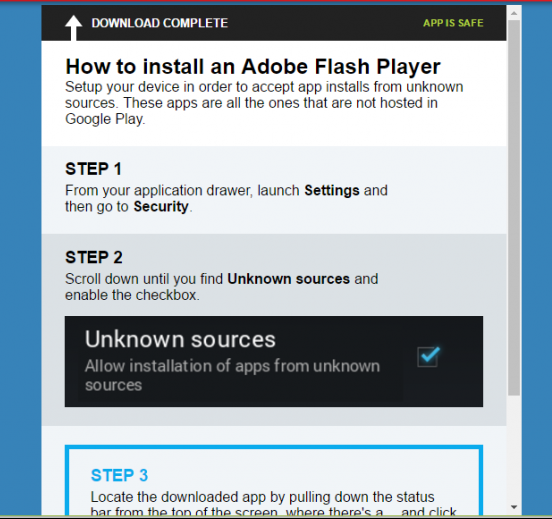
Upon infection, the malware begins communication with the Command and Control (C&C) server and silently hides in the device until one of the 40 possible financial applications (such as PayPal and Citibank) it detects are opened. Once this happens, it is able to create an overlay page that looks like the actual login page of the app. Examples of these overlays can be seen below:
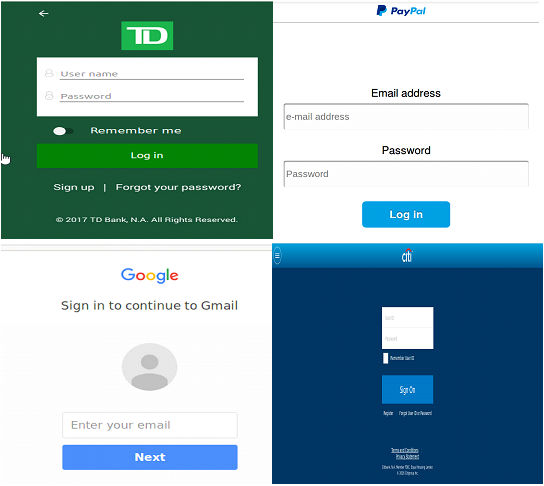
Further complicating matters is that, unlike previous variants of Marcher, this version is much harder for antivirus programs to detect. As such, it really is in the hands of the user to prevent their Android device from this banking malware. You should be suspicious of any download prompts that you run across, especially those that claim to be major products like the Adobe Flash Player, which are often fake. Only download such updates directly from the official websites rather than third-party redirects. Additionally, try to avoid downloading anything from third-party sources unless it has been rigorously verified by security researchers.
Photo credit: Pixabay



