Introduction
Microsoft released Forefront Endpoint Protection (FEP) 2010 in December 2010. This is Microsoft’s sophomore offering in the anti-virus space, but the first to be seriously considered by enterprise customers. Is Microsoft serious about the anti-virus business? Should you consider FEP in your organization or does it still need more time ‘in the oven’ before it’s ready for prime time?
Microsoft and Security
Microsoft has made great strides in the security space for its core products in the last several years. They have invested a fair amount of money in the Security Development Lifecycle (SDL), beefed up the security of Windows desktops and servers, SQL is more secure , as well as Office out of the box. However, the ‘best of breed’ security approach always dictates caution in putting too many eggs in any one basket. Many consider that by balancing your risk between Microsoft (OS) and another vendor (e.g.: Symantec, McAfee, Trend Micro) for endpoint security, you’re diversifying your protection capabilities.
Microsoft jumped into the anti-virus space with a bang with the release of Security Essentials in November, 2008. They’d had some previous offerings (Windows Defender), but Security Essentials was the first to offer a complete anti-virus and anti-spyware solution that was free (Windows Live OneCare was a short-lived subscription-based precursor to Security Essentials). Advertising itself as lightweight, efficient and accurate anti-malware solution that ‘stays out of the way’, Security Essentials rapidly took share in the consumer anti-virus space. Microsoft claims that Security Essentials does not compete with other “for-pay” anti-virus software, but is insteaded towards the 50-60% of PC users who don’t have (or won’t pay for) anti-virus and anti-malware protection, according to Amy Barzdukas, Senior Director of Online Services and Windows Division at Microsoft. It’s clear that Microsoft is doing something right; in February 2010, a rogue anti-virus package calling itself ‘Security Essentials 2010’ with a nearly identical look and feel to Microsoft Security Essentials hit the Internet and infected numerous devices worldwide by masquerading as the popular Microsoft anti-virus product. The legitimate product can be obtained here.
Forefront Endpoint Protection Builds on Security Essentials
Microsoft has built on the success of Security Essentials in the enterprise with the new Forefront Endpoint Protection 2010 package. The Security Essentials interface can be seen in Figure 1. Microsoft’s philosophy was to invest in the development of a common client between Security Essentials and Forefront Endpoint Protection. That way innovation and development between the consumer and the enterprise clients can be shared and common features can be integrated seamlessly. Security Essentials and FEP also share the same Microsoft Anti-Malware engine.
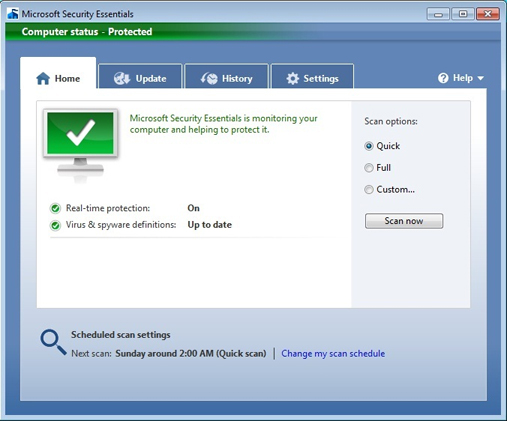
Figure 1: Microsoft Security Essentials client.
As more organizations evaluate their contracts with different vendors, security products are coming under more scrutiny. Purchasing folks and finance teams are asking ‘hey, if I can have free anti-virus on my home PC, why are we paying so much for it for our enterprise desktops?’ With FEP, Microsoft is promising a low-cost and integrated anti-virus solution that will save money and increase efficiency. Does this offer really stack up?
The Structure of FEP… Along with SCCM
Let’s dig into the guts of FEP: Forefront Endpoint Protection is tightly integrated into System Center Configuration Manager (SCCM) 2007. The FEP interface is shown in Figure 2. This is great news if you’re a SCCM customer. You now have an integrated anti-virus solution that leverages the SCCM agent you have already deployed onto your desktops or servers. If you are not using SCCM, this introduces a bigger learning curve and more infrastructure to deploy. Make sure to check your Microsoft licensing agreement; you may own System Center Configuration Manager Client Access Licenses (CALs) and just not be using them. This should factor into the cost savings for anti-virus.

Figure 2: SCCM Console with FEP integrated in
So, what does using SCCM get you with anti-virus? Microsoft’s approach is to integrate management and security into a single environment. By viewing anti-virus as another workload (along with patch management, application distribution, configuration management, etc.), companies can now use a single console to manage anti-virus while integrating their infrastructure for management and security. The idea of deploying an anti-virus solution with no additional infrastructure required can be very appealing, especially on the client side. FEP uses the SCCM client for updates and client-server communication. The existing SCCM distribution points are used for distributing engine updates, definition updates and updates to the client itself. SCCM synchronizes the definition updates from the Microsoft Update catalog, so if your client is off the corporate network you have the option of configuring it to check for definition updates directly from Microsoft Update. This allows clients to stay up to date and protected as long as they are connected to the Internet.
The FEP agent itself is fairly lightweight; when an IT Pro is deploying FEP, it’s even possible to use the wizard-driven SCCM interface to automatically remove competitive anti-virus solutions (e.g.: Symantec and McAfee) prior to pushing down the FEP agent. This provides for a fairly seamless migration, especially when using the SCCM targeting groups that have probably already been built for patch distribution, application packaging, etc. FEP also supports a unified policy management workflow which allows you to create and apply policy from a single interface inside of SCCM.
From a scalability perspective, the integration with infrastructure you already have is beneficial as well. With traditional anti-virus solutions, there’s been a ‘cost’ of scale (additional SQL Servers, additional management nodes, etc.). There are SCCM deployments that support upwards of hundreds of thousands of clients currently out there. This may not be applicable to many smaller IT environments, but knowing the scalability is there helps.
FEP uses a number of technologies in the agent to detect malicious content. In addition to the traditional signature-based detection engine, there’s behavioral monitoring that detects anomalous system behavior and reviews reputation data to identify potentially unknown threats. FEP also has something called the ‘Network Inspection System’ which allegedly blocks exploitation of vulnerabilities on a FEP-protected endpoint as well as performing analysis on network traffic. These features appear roughly comparable to the anti-virus and host-based intrusion detection and prevention capability available in most competing anti-virus products.
FEP also allows for management of the host-based Windows Firewall policy via the SCCM policy configuration interface, allowing for configuration of endpoint security as well as allowing or denying connections. The UI for managing the firewall configuration isn’t as robust as what’s available in the Group Policy Management Console (GPMC), but basic configuration is possible via SCCM.
Configuration of the FEP agent is on par with what you’d see in other anti-virus clients as well, with both ‘full’ and ‘quick’ scanning. Real-time protection is a configurable option, although turning that off does not seem to be a good option for most corporations. Mapped drives can be scanned and exclusions can be made based on file name, file extension and process name. All in all, giving you granular control over the FEP agent. An overview of the FEP agent can be seen in Figure 3.
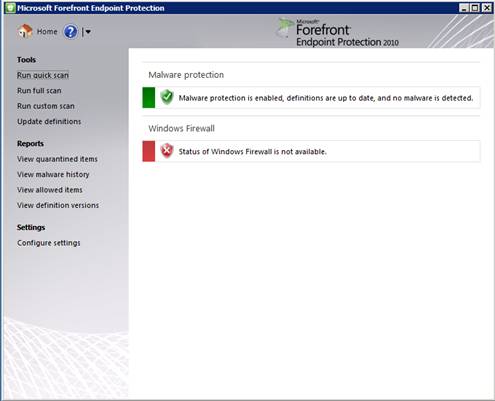
Figure 3: Forefront Endpoint Protection (FEP) agent.
Summary
So, what’s the verdict? If you’re an SCCM user today, you should give FEP a good, hard look. It’s clear that Microsoft has spent time building this solution as an integrated part of SCCM and the efficiency of managing anti-virus in this interface may be worth it. Integrating anti-virus updates into your SCCM or WSUS update infrastructure will most likely cut down on bandwidth usage (WSUS and SCCM distribution points use the BITS protocol to trickle down updates). FEP also has some interesting ‘delta definition update’ capability to only give your client the definitions it needs, not push a large definition package down each time. If you’re not using SCCM, you may want to hold off on FEP (while it’s technically possible to deploy FEP without SCCM, the management and hassles like lack of reporting and alerting are probably not compelling to most organizations). However, when negotiating pricing with your current anti-virus vendor, it can’t hurt to push to get the best price and consider moving from a 3 year renewal cycle to a 1 year renewal cycle to provide more flexibility should you want to move to another solution sooner, rather than later. The big question mark that seems to be a consensus amongst others is that FEP has only been released for 3 months. It is currently considered a ‘2.0’ product (it follows Forefront Client Security from Microsoft), only time will tell whether this solution is ‘good enough’ for many corporations to justify saving a large amount of money on anti-virus or if enterprise should wait for a ‘3.0’ release from Microsoft. More information about FEP is available from Microsoft’s site here.




