Cryptography is easily one of the most important tools in keeping information secure. The algorithms employed in encryption help ensure that data is not tampered with and is able to be seen only by intended parties. Especially in recent years, the discussion of cryptography has moved outside the realm of cybersecurity experts. Many of these discussions encompass various threats to encryption, through legal means or otherwise.
As encryption becomes more and more a part of the public consciousness, I felt it necessary to talk about how modern cryptography is threatened. Discussing threats is not sufficient, however, as that only highlights problems and not solutions. In this article, there will also be a discussion of how the cybersecurity community is combating these threats.
In order to accomplish the aforementioned goals, we will go through various cryptographic methods widely used today and analyze their flaws (through various threat vectors). It will not be an exhaustive list, but rather an overview. After this, I will explore arguably the greatest threat to modern encryption outside of vulnerabilities: the government.
Let us begin first, however, with an exploration of popular modern day cryptographic methods:
RSA: Why encryption is meaningless if the developers are hacked
The RSA algorithm (named for creators Ron Rivest, Adi Shamir and Leonard Adleman) is an asymmetric cryptographic method. Asymmetric cryptography employs both a public key (which can be shared amongst anyone) and a private key (which cannot be compromised as long as it is guarded).
It is imperative to understand that RSA is considered the de facto standard for asymmetric cryptography. It is used in countless situations, such as creating a secure connection over an insecure network (SSH, VPN authentication, etc.). As this is the case, imagine the chaos should the algorithm become compromised.
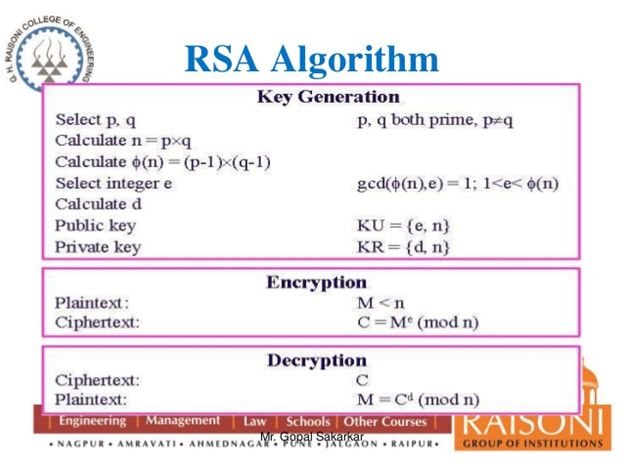
Thankfully, when implemented properly, the RSA algorithm is particularly hard to crack. The threats that face this cryptographic method more involve the company that distributes the keys. RSA (the company) has faced successful hacking attempts which caused a massive threat to all keys in use at the time. Most notably in 2011, the company came under “an extremely sophisticated cyber-attack” as a result of phishing emails.
The extent of the damage was never revealed by RSA, but the damage was bad enough that the company gave out free replacement keys, wiping the compromised ones from existence. This occurred at defense contractor Lockheed Martin, a customer of RSA, and ultimately RSA replaced any and all tokens, an expensive and laborious task.
In this case the greatest threat to cryptography is more of an outside force. Should RSA suffer a security breach, then its algorithms are at risk. The RSA algorithm itself is very strong and very difficult to crack, but none of that matters if the actual company is compromised. The measures to protect against threats to RSA (cryptographic method) really are in the hands of the people in charge of RSA (the company).
SHA (Secure-Hash-Algorithm): A lesson in how complacency is the death of security
There are various hashing algorithms that exist to protect against crackers attempting to find sensitive information (like passwords). Of all the algorithms, SHA is considered to be the most secure, namely due to its 160-bit hash value. It currently exists in three forms, each an improvement upon the last.
As it stands today, most still use SHA-1 due to incorrect projections. For example, a report from security researcher Bruce Schneier said that it would cost at least $700,000 USD to break the algorithm. This report was in 2012 and many in the security world based their policies regarding SHA-1 on estimates like it. As such, SHA-1 became the de facto algorithm and it still is to this day.
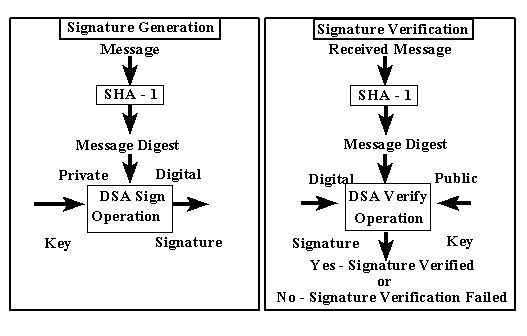
The problem is that it turns out that the projections were wrong. As it stands today, it is possible for roughly $100,000 USD to create a collision attack which capitalizes on two different hashes having the same output that deciphers the SHA-1 hash value. What this means is that numerous systems, until they upgrade to the 224 to 512 SHA-2 (preferably the 1600 bit SHA-3 as it is the most secure), are vulnerable.
Even then, however, these algorithms will eventually face threats. Quantum computing is, at the moment, far away from being an actual option for the entire world, but many are warning of a near-future in which quantum computing renders even the strongest hashing algorithms like SHA-3 useless.
The lessons to take from this are vital. Firstly, becoming complacent in encryption methods without staying up to date on cybercriminal activity is foolish. Far too often those in the security field set up a method of data protection and then fail to actively research threats over the years. It usually isn’t until something is horrifically wrong that IT divisions take notice. It should not simply be the job of InfoSec journalists and researchers to warn of a security method becoming more vulnerable.
The second point to understand about threats to hashing algorithms is that technology is always changing. Black hat hackers are always coding new exploits to take advantage of a system. In addition to this, the computer world is always on the edge of a massive paradigm shift. The technology that seems powerful today will be minuscule compared to phenomenon like quantum computing. The response that the cybersecurity world must have is to attempt to stay in lock-step with technological advancements. This is imperative but it will require solutions that may seem totally insane at this time.
Governmental threats to cryptography: A pressing issue
Especially in recent years, the fight for cybersecurity has moved into the realm of government. The intention of discussing government can cause apprehension in the security community. The reason for this is that politics tends to be something that makes us uneasy. There tends to be a lot of vitriol and few solutions in the political discourse we see daily, so why would we want to become involved?
Unfortunately, the government (in this case I refer to the United States government) has become more brazen over the years when trying to circumnavigate cryptographic methods. The go-to method for intelligence agencies is installing backdoors into various programs and equipment.
Often there will be technology companies willing to compromise the security and privacy by acting as the executor of the backdoor. Take, for instance, the previously mentioned RSA. Beginning in the early 2000s, the company allowed the NSA to install a backdoor in Dual_EC_DRBG. What the kleptographic backdoor allowed the NSA to do is steal information without any detection.
This is not the only instance though, as there are countless cases of Silicon Valley doing covert operations with intelligence agencies. This has effectively allowed the government to bypass encryption and violate the privacy of unwitting American citizens.
I realize that there are legitimate threats to national security that must be dealt with. The problem is, simply put, that we are setting a dangerous precedent. With private companies placing code in everyday products that allow a powerful entity unbridled access, we are seeing cryptography’s mission being compromised. What is the point of coming up with powerful encryption algorithms if the technology sector is willing to sell out?

This issue is equivalent to opening Pandora’s Box, but it is absolutely valid. It is not simply a matter of privacy; it is a matter of security. These covert backdoors can be used by black hats as easily as they can be used by someone at the NSA’s Fort Meade headquarters. The only way to ensure that cryptography does its job is to reject the politics of fear. Both the security field and ordinary citizens will be better off for it.
In the end, cryptography is an extremely complex topic. I have only scratched the surface of the issues that face it in today’s ever-changing technological world. My hope is that you, the reader, may possibly become more conscious of just how valuable cryptography is. Hopefully, you will see the need to further its advances no matter how much resistance it faces.
Photo credits: Mr. Gopal Sakarkar, Giorgio Ingargiola, and D-Wave Systems




