NASA’s Jet Propulsion Laboratory recently found itself in a rather odd predicament due to phishing attacks. According to an internal email sent to all employees from the Office of the CISO, a phishing email caused all outgoing email to Gmail, Yahoo, Hotmail, and other email accounts to be blocked. The email in question, which was provided by my anonymous source within JPL, says the following:
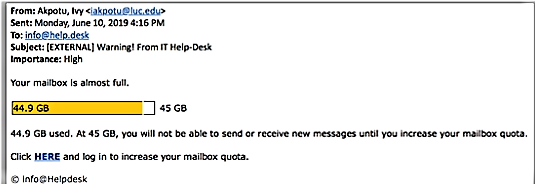
Monday, June 10 at 4:16 pm, over 3,100 JPL users received a phishing email appearing to come from an IT Helpdesk. The email contained a malicious link to “outlookstoragequotaportal.yahoosites[.]com” or to “webmailaccessstorageportal.yahoosites[.]com”.
The link, if clicked, directed users to a Yahoo-hosted site requesting a JPL username, email address, and password. At least nine JPL users fell victim to the phishing attack and provided their email and password. On Tuesday, June 11 at 5:34 am, at least four of the compromised JPL accounts were used to launch 1.8 million emails to individuals including JPL users, NASA employees, external partners and email services. Two external email services (SORBS and IBM DNS), who monitor SPAM for industry, responded by blacklisting all email coming from JPL. As of Thursday morning, at 7am JPL was removed from the blacklist lists and email is functioning normally.”
I have said it before, but it bears repeating. Jet Propulsion Laboratory, and NASA as a whole, has struggled with implementing effective cybersecurity practices. The amount of top-secret projects (both for NASA and the Defense Department) that are developed at this location is reason enough to be alarmed at their lax initiative. JPL is simply lucky that this phishing email attack was not the start of a larger network infection. While it only takes one individual to compromise a network, the fact that nine employees fell for a poorly crafted phishing email is absurd.
Ultimately NASA, especially the Jet Propulsion Laboratory campus, needs to overhaul their cybersecurity training. The next incident may not be so easily solved.
Featured image: NASA/JPL-Caltech




You’re mistaking the general computing network from the areas that actually have critical data. You can’t fix stupid, this was a social-engineering attack and effectively accomplished very little. Anything of interest is on the FlightOps network (fltops.jpl.nasa.gov) isolated from the main JPL network and requiring 2FA. And anything sensitive (as you claim) is located in a SCIF which is air-gapped and has physical security measures to enter and exit.
I worked there for 16 years. There was a time it was bad, everybody had a public routable IP (no NAT) and no firewall to prevent listening on any port. About 20 years ago they implemented a massive security audit and really began locking things down.
Just report the facts (phishing attack compromised a few email accounts, temporary blacklist ensued) and leave your opinions (JPL is simply lucky that this phishing email attack was not the start of a larger network infection) out of it. You have no idea what you’re talking about. As a fellow UCLA alumni you’re tarnishing the name.
Because in the general network there is still a ton of sensitive data being transmitted via email. Plenty of individuals there don’t use end-to-end encryption when using email, and while you can’t fix stupid, there is still a chance that something can be accessed as a result of such phishing attacks. All it takes is access to one privileged account to start a destructive chain of events. I know this since I am a penetration tester in addition to being a journalist.
Also for somebody so concerned about JPL security, why the hell would you link to the entire world the address to the FlightOps network? Not to mention telling the entire world they use 2FA and that they hide all the juicy stuff there? You do know 2FA is not nearly as secure as people think it is right? For somebody who claims to know so much about security you just gave black-hats plenty of inside information that I never would have personally disclosed in my article.
Go Bruins?