
Most companies rely on network infrastructure security (NIS) to run smoothly. Network infrastructure includes resources like hardware, software, and services. They enable effective communication between processes, applications, and users. Cybercriminals, though, can exploit vulnerabilities. They gather private information, steal data, or cause network disruptions.
Companies use infrastructure security measures to protect their networks. This reduces the financial loss risk from malicious activities. In this article, I’ll explain NIS. I’ll also look at its benefits and implementation strategies in detail. First, let’s start with the definition of the term.
What Is NIS?
NIS combines the strategies, processes, and technologies protecting your network resources from exploitation. Every network infrastructure component creates an attack vector. This is basically an entry point into your internal IT systems. NIS includes installing security hardware and software. This prevents unauthorized access, modification, network resources, and data theft.
It combines various technologies, including:
- Strict access control
- Firewalls
- Authentication protocols
- Data encryption
- Intrusion prevention systems (IPS)
These further strengthen your network security. Before learning about implementation, let’s explore the benefits of NIS.
4 Reasons Why NIS Is Important
Data is a company’s greatest asset. This makes it the biggest target for theft. For instance, data leaks can cause financial and reputational losses. They may also cause operational disruptions. Effective infrastructure security measures can limit the impact. An effective NIS strategy can also bring:
1. Efficient Network Performance
NIS ensures that a company’s network is reliable and runs efficiently. Companies enjoy more uptime, consistent app performance, and faster product implementation.
2. Resource Monitoring and Allocation
Companies track network asset usage and performance using NIS tools. Thus, admin personnel can allocate resources for optimal network efficiency.
3. Secure Communications
Employees can communicate securely with both internal and external stakeholders. Customers also feel secure communicating private data with your employees.
4. Cost Saving
To reduce operational costs, companies share network resources among teams, departments, and offices. They also reduce costs associated with repairing damages caused by a security breach.
Now, let me explain how NIS works!
How Does NIS Work?

Your company’s NIS measures depend on various factors. These include industry regulations, legal obligations, and your network’s unique requirements. I’ve listed some common strategies that companies use to implement NIS effectively.
Network Segmentation and Segregation
Network segmentation divides network resources into smaller segments. The segments depend on factors like geography or usage. That said, segregation separates resources based on functionality, criticality, and risk. You can also assign unique firewalls, security protocols, and access controls to each segment.
This tactic doesn’t prevent an attack though. Instead, it ensures the vulnerability exploits on one segment don’t penetrate others. You can also easily unplug an exploited segment. This limits the capacity for cybercriminals to spread malware to the entire network.
Limiting Infrastructure Attack Surface
An infrastructure attack surface is the sum of all attack vectors. Intruders use these attack vectors to gain unauthorized access. Thus, you should map your attack surface to understand all vulnerabilities. Afterward, you can put in place the following strategies:
- Uninstall unused network devices, apps, and services.
- Scan third-party devices and services for vulnerabilities and uninstall insecure ones.
- Update all networking software to get the most security patches.
- Limit privileges assigned to network servers, databases, and applications.
- Separate critical systems and applications.
- Install various authentication protocols to prevent unauthorized access.
Limiting Unfiltered Peer-to-Peer Communications
Unfiltered peer-to-peer communication is a significant vulnerability for any network. This includes router-to-router communication. Cybercriminals exploit these unfiltered communications to gain access and spy or steal data. You can install host-based firewalls to restrict communication from peer hosts.
Hardening Infrastructure Devices
Hardening a device is the process of making your network device more resilient. You can also use hardening measures like:
- Adhere to industry standards on network encryption.
- Disable unencrypted remote protocols for managing network infrastructure.
- Limit administrative privileges for infrastructure resources.
- Update operating system and other software on all network devices.
- Restrict physical access to infrastructure devices.
Validating Integrity of Hardware and Software
Low-quality software and hardware often fail to meet appropriate security standards. They can introduce malicious programs into a network. You should adopt the following measures:
- Buy products from authorized vendors only.
- Define device and software integrity standards.
- Enforce regular checks on all software and devices.
- Inspect products immediately after buying to ensure they meet defined integrity standards.
- Confirm serial numbers of purchased products from trustworthy sources.
- Download updates and patches only from official websites.
Out-of-Band Management
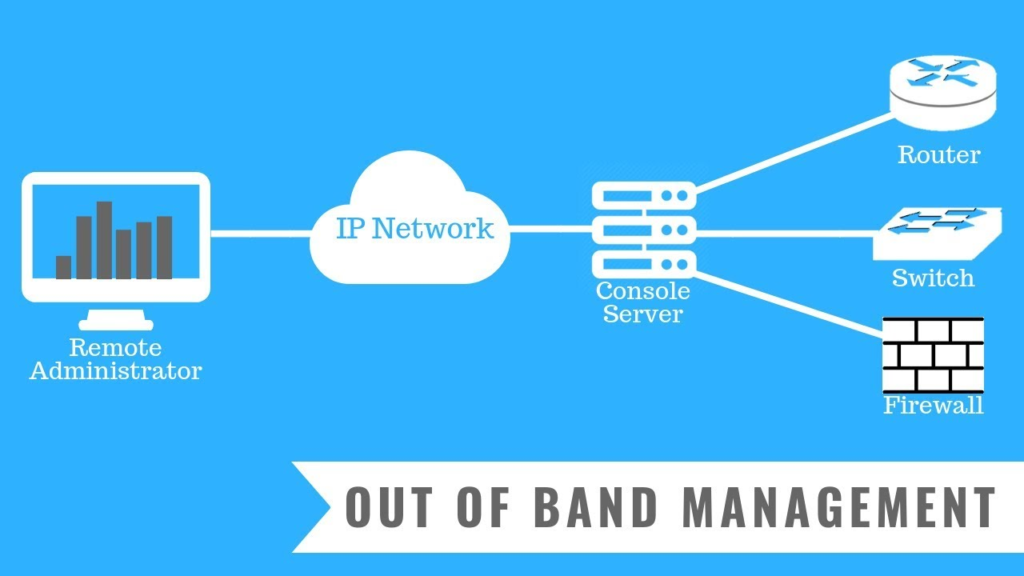
Out-of-band management (OOBM) refers to alternate secure dedicated access to a network. It enables specific executives to manage networking devices. It also doesn’t disrupt network traffic. With OOBM, executives check vulnerabilities and restrict network access to prevent security breaches. In case of an attack, an executive can also affect configuration changes. This locks the cybercriminal out of the network.
Next, I’ll explain the various technologies you can adopt to action the above ideas.
6 Different Technologies to Implement NIS
Your company may rely on the following technologies when implementing NIS.
1. Access Control Software
The access control software can assign appropriate network resource authorization to personnel and services. You give every employee the exact level of access they need to get their work done. Thus, no one can make network configuration changes by accident. You can also ensure that only trusted personnel can affect changes.
2. Virtual Private Network
A Virtual Private Network (VPN) is an ideal technology to guarantee network security. VPNs reroute all data traffic through an encrypted channel over the public internet. They also ensure communication between two endpoints remains secure and immune to eavesdropping.
3. Firewall
A firewall is a software barrier between a private network and the internet. Firewall software filters incoming traffic based on defined security configurations. In turn, this process protects the network from harm.
4. Antimalware
Antimalware programs scan all existing and incoming data for malicious software. This includes viruses and worms. These programs immediately expel discovered malware to protect the network and connected components.
5. Intrusion Prevention System
Intrusion prevention system (IPS) tools monitor network traffic for suspicious activity. They identify attack patterns and take action. They also send automatic alerts to your security team. As a result, they can stop the attack with minimal damage.
6. Security Information and Event Management
Security information and event management (SIEM) are tools and services. They provide centralized view and control of a company’s IT security. For example, you can use SIEM tools to view event logs and real-time network-traffic analysis.
You can choose any of the above technologies for NIS implementation. I’ll also share some more best practices to strengthen your network protection.
3 NIS Best Practices
To strengthen your company’s NIS, use the following best practices.
Ensure Password Security
Encourage executives and staff to use strong passwords. Create long, randomized passwords. To this end, combine letters, numbers, and symbols. Weak or easy-to-guess passwords also create an avenue for security breaches.
Ensure Regular Updates
Ensure that you often update user privileges to services. Once a user no longer needs access to a service, revoke their permissions. You can also use access control software to automate the process. In addition, you must update software patches to get the latest security fix.
Encrypt and Backup Data Regularly
Cybercriminals can’t use encrypted data, even when they enter your network. Thus, you must encrypt all files and communications with strong encryption protocols. You should also back up all data on your systems. That’s because data backups allow quick recovery for deleted or compromised files in an attack.
Now, let’s summarize!
Final Words
Attackers are always looking to exploit any vulnerability in your network infrastructure. Successful attacks are a gain for the cybercriminal and a loss for your company. NIS helps prevent, respond to, and recover from cyber attacks. You can use several methods and technologies to implement NIS effectively.
You must choose the best options based on your network requirements. Configuring the tools correctly is also a must. In addition, you’ll get optimal protection if you follow the best practices in daily network operations.
Do you have more questions? Read our FAQ and Resources sections to learn more about NIS.
FAQ
What are the three components of network infrastructure?
Network infrastructure comprises three components: hardware, software, and services. Hardware includes every physical network resource, like routers, switches, and cables. The software includes operating systems, firewalls, security applications, and intrusion prevention systems. Network services include IP addressing, satellite, DSL, or wireless protocols. However, all these components may contain vulnerabilities that cybercriminals can exploit.
What is network infrastructure vulnerability?
Network infrastructure vulnerabilities refer to weaknesses in a network component. Cybercriminals may exploit these weaknesses to gain unauthorized access to the network. Once they do, cybercriminals can install malware or launch DDoS attacks. Network vulnerabilities may also be physical or virtual.
What’s an NIS threat?
A network infrastructure security threat is a malicious act. For instance, it can corrupt or steal data. It can also disrupt your network or operations. A security threat doesn’t imply that the attack is successful though. It means the cybercriminal has carried it out.
Who’s responsible for a company’s network security?
The Chief Information Security Officer (CISO) leads a company’s network security team. The CISO creates and implements policies to monitor and secure network infrastructure vulnerabilities. The CISO also provides a response strategy if attacks occur. In addition, the CISO communicates the security status to executives and stakeholders. He encourages every company member to take charge of data security.
What’s the difference between network security and cyber security?
Network security is a cybersecurity subset and protects data from theft. The difference between both terminologies lies in the realm of operation. Network security is only concerned with network protection. On the other hand, cyber security involves protecting applications, smart devices, hardware, software, etc.
Resources
TechGenix: Newsletters
Subscribe to our newsletters for more quality content.
TechGenix: Article on Network Security Threats
Read about common network security threats.
TechGenix: Article on Importance of Network Security
Learn more about network security and its importance for your business.
TechGenix: Article on Cloud Network Security
Discover how to develop the most effective cloud network security.
TechGenix: Article on Network Security Key
Learn more about what a network security key is and where to find it.



