
Source: Pixabay
Back in the day, looking after a network was as simple as plugging a few leads into a router. But times have changed. Now, you’re swimming through a sea of cables and devices connecting and disconnecting to your network. And as a result, you can’t manage a network without tokenized management systems and IT best practices. Even then, you need to spend some time figuring out how it all meshes together. To this end, you need a network management solution (NMS) to help manage your network and give you more time to focus on essential business requirements.
But how exactly does an NMS help you manage your network? And do you even need one for your business? In this article, I’ll show you the different types of NMS solutions — and this will help you see how each type can address your specific business needs. I’ll also show you an NMS’s many operational and security benefits. And if this article helped you make up your mind about getting an NMS, the second part of this two-part series will show you how to make your choice. So stick around!
Network Management Solution Types

SOURCE: Infinity Tactics
Network management is the process of orchestrating network traffic across your enterprise. In essence, an NMS offers network analytics, security, and other tools. So, what protocols does an NMS use to govern your titanic network?
Protocols
An NMS uses protocols to work correctly. Essentially, each solution is unique and will use some or all of the protocols listed below. These protocols manage its utilities, data packets, and data analytics.
- Simple Network Management Protocol (SNMP): Uses SNMP to interact with network components
- Internet Control Message Point (ICMP): Helps with error reporting from hardware like routers
- Flow-based: Captures real-time data packets to identify network status, bandwidth utilization, and suspicious traffic
- Active Network Monitoring: Uses packet injection into network traffic to gauge transmission rate, data loss, reachability times, and more
Each of these protocols has a different objective, and that can be very useful for your different requirements. But that’s not the only way to distinguish the types of NMS out there. NMS differ in hosting types, too. And it’s up to you to choose whether you want this solution hosted on-prem or in the cloud. Let’s take a look at these two types, and see how each can help your business differently.
On-Premise Hosting
An on-premise NMS means you’re hosting the solution on your infrastructure. Consequently, you have complete control over it and the data it inspects. For this hosting type, you’ll need resources to use and manage the NMS and its infrastructure effectively.
In short, hosting your NMS on-site is expensive. But its benefits for specific industries and companies outweigh the expense. That said, smaller businesses generally opt to use cloud-based solutions.
Use on-premise hosting when your intellectual property is sensitive and needs controlling. Additionally, military suppliers and vendors associated with its supply chain should use this option.
Cloud-Based Hosting

Cloud-based solutions are hosted on hardware that can scale solutions to meet your business demands as it grows. In turn, this reduces costs on efficiency scales. In this setup, you don’t need to worry about backend maintenance — the vendor handles that.
Vendors offer services as a subscription. As a result, you can scale your service with business needs, reducing the barrier to entry. Thus, SMEs can afford cloud-based solutions, albeit with reduced data control.
Use a cloud-based solution if you’re a startup with a complex network that’s already difficult to manage. Additionally, if you’re using edge, IoT, or mobile devices, a cloud-based solution is an easy way to keep your network shipshape at a low entry price!
On-Premise vs Cloud-Based Hosting
In the table below, you’ll see what features you get with each hosting type. This way, you can better understand which type will achieve your business objectives — whether big or small.
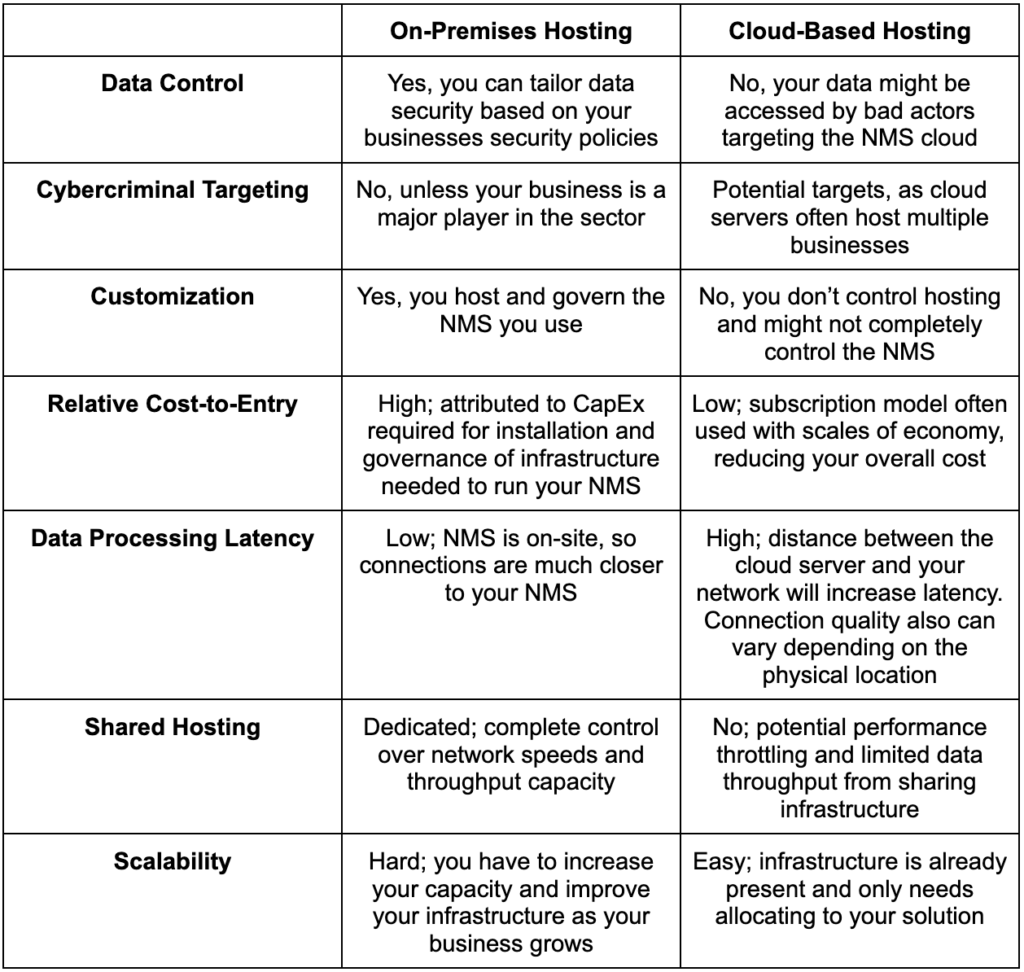
Clearly, an NMS can be an excellent tool to manage your network in line with your budget and business needs. But that’s not all! Let’s take a look at 6 benefits you can expect from an NMS tool.
6 Network Management Solution Benefits

SOURCE: SoberInfo
Different NMS tools have varying benefits. However, the following 6 are what you can expect from any good NMS tool.
1. Reduced Risks
Human error is unavoidable. But an NMS helps reduce the risk of missing a potential attack surface during server hardening activities. This is especially important for complex networks. In addition, your NMS can automate application patching. Reducing risk to your business will reduce the expenditure needed to resolve issues. In turn, this will help improve business growth.
2. Optimized Traffic
An NMS can automate load balancing and traffic flow even in complex networks. Most solutions use an abstraction layer that records your “intent”. It then optimizes your network. Basically, the NMS will use intelligent algorithms or artificial intelligence. These processes will help to improve the decision-making process during network configuration. This abstraction layer is similar to next-generation firewalls. In some cases, it’s also part of the overall NMS solution.
3. Improved CapEx Returns
You’ll improve your hardware cost-to-performance ratios for your network regardless of whether you choose an on-premise or a cloud-based solution. This is because optimizing traffic and server performance to send and receive traffic is reduced. In essence, you’ll have more capacity for your applications to use, saving you money.
4. Enhanced Data Logging
Your NMS automates data logging to improve your investigative productivity. Setting, checking, and turning off loggers can be very time-consuming. Also, if you forget to turn off a logger, you can often fill your storage space quickly. As a result, your server could fall over. An NMS can help automate the process across your connected devices and manage logging centrally.
5. Improved Data Inspection
You can assess data packets for malware threats in real-time on-premise or using a cloud-based solution. Most NMS solutions will incorporate a next-generation firewall solution that will inspect data packets for threats. As such, it’s harder for bad actors to get malware or advanced threats inside your perimeter or spread to network segments. Additionally, data analytics can be driven by the data flowing through your network and the NMS solution. This can help automate network balancing.
6. Improved Device Mapping
You can streamline the device mapping process by using the NMS’s automated mapping features. Basically, your NMS can find new devices and automate connection configurations through administrator intent. Mapping is a time-consuming process which doesn’t allow administrators to change device behavior remotely. An NMS simplifies this process and allows you to easily implement changes to network policy. So if you use edge devices, IoT-connected devices, or mobile devices, ensure your NMS can find and interact with them effectively.
At this point, you should understand the benefits of an NMS and how it helps monitor and improve network efficiency. However, most of these solutions also have integrated cybersecurity features. In the next section, you’ll learn how an NMS improves network security with some common utilities often shipped with these solutions.
5 Ways Network Management Solutions Help Security
All-in-one NMS solutions provide several security solutions. So whenever you implement an NMS, you’ll enhance your network’s security. This makes an NMS even more valuable for your company. So let’s take a look at 5 NMS security features and how they’ll boost your network security.
1. Patch Management
Your NMS should provide automated patch management for operating systems, third-party apps, and web browsers. Using a good patch management solution will reduce one of the many routine tasks you must conduct. In addition, it ensures your systems are always up to date. Essentially, it’s important to keep up with patches as they often have important security fixes for your systems.
2. Detect Vulnerabilities
An NMS should offer vulnerability detection that provides ways to remediate attack surfaces. As a result, up-to-date vulnerability detection will ensure your systems are safe from malware and other cyber threats.
3. Web-Based Reporting
For a cloud-based NMS, you can access your solution quickly from anywhere with a dashboard. In short, you can use high-level visibility and orchestration tools without needing to be on-site. For convenience, you can also get automated alerts and push notifications to mobile devices. Knowing what’s happening on your network provides top-level visibility that’s easy to access. As a result, you’ll be able to delve deeper into potential network and security challenges.
4. Track Recent Vulnerabilities
All network management solutions must be able to access the latest information about cyber threats. Without this ability, new threats may escape your NMS security filters. Consequently, they can cause damage to your business. Tracking vulnerabilities helps cybersecurity teams investigate the attacker’s end goal. As a result, this will give you information about how the network can be hardened to reduce future exposure.
5. Check Vulnerabilities on Networked Devices
Modern networks aren’t static infrastructures. To clarify, they often have connected devices that need vulnerability checking along with the broader system. And if your NMS has a unified operational feature, administration will be more efficient. In short, this streamlines finding and resolving vulnerabilities so you can focus on other administrative duties.
Now you know exactly what you’ll get if you choose to implement an NMS. So let’s recap!
Final Thoughts
If you’re yearning for the olden days when network management was simple, it’s clear you need an NMS.
For starters, network management systems use different protocols that can address your different business needs. They also come in two different hosting types—on-prem or cloud-based. And this gives you more flexibility when choosing an NMS based on your budget and business objectives.
In this article, I highlighted the different benefits that come with implementing an NMS—you’ll finally be able to optimize traffic and boost your security, all through your NMS.
So it’s clear that implementing an NMS is well worth the effort. But with many NMS providers competing on the market today, how can you choose the best one for your business? That’s what I’ll show you in the second part of this article.
In the meantime, do you have more questions about network management solutions? Check out our FAQ and Resources sections below!
FAQ
What are abstraction layers in network management solutions?
Network management solutions (NMS) use an abstraction layer between configuration settings and the user. This layer takes top-level administrator “intent” from a few questions. It then interprets the input to customize the configuration using AI or intelligent algorithms. As a result, it saves you time and reduces the risk of security errors.
What is a next-generation firewall solution (NGFW)?
NGFW uses administration intent and an abstraction layer to configure the firewall during installation. In short, you’re making the process faster and less error-prone during customization. Additionally, the same abstraction layer manages the NGFW during routine use. It allows you to work more efficiently than dealing with incoming and outgoing rule sets and getting them wrong occasionally.
Should I use an on-premise or a cloud-based network management solution (NMS)?
An on-premises NMS provides complete data control. But, you must invest in infrastructure and resources to manage and maintain it. Thus, most SMEs prefer to opt for a cloud-based subscription service with all the benefits at a competitive price. The NMS can be scaled as the company grows and reduces the cost-to-entry.
Should I use independent or integrated network management solutions (NMS)?
Network management solutions are modular utilities that, when designed to work together, work synergistically to manage and protect your system. Using independent components makes it challenging to manage each solution and ensure your network is secure and running optimally. Thus, choose an integrated NMS for both ease of use and network efficiency.
How do I improve my network efficiency to maximize my infrastructure utilization?
Networks are optimized using next-generation network management solutions (NMS) that integrate all the utilities required to manage a network and automate workflows. Administrators define the intent of the network during installation using an abstraction layer. This layer configures the network based on intelligent and AI-driven algorithms. As a result, it reduces the risk of you missing something during daily management.
Resources
TechGenix: Article on Traditional and Cloud-Based Firewalls
Discover the difference between traditional and cloud-based firewalls.
TechGenix: Article on Proxy Servers and Firewalls
Learn the difference between proxy servers and firewalls and how they work to protect your business.
TechGenix: Article on Out-of-Band Management
Get to grips with out-of-band management and how it can help improve business efficiency.
TechGenix: Article on Network Switches
Find out how network switches work and how they can help you manage your network traffic better.
TechGenix: Article on System Center Operations Manager (SCOM)
Learn everything you need to know about SCOM and how it can help streamline workflows.



