In this issue:
Editor’s Corner – how to sleep well at night. Make money killing bugs. Quick Assist headaches. Alerts on Windows Server problems. Password manager reviews. Tips and tutorials on PowerShell, Windows Server, Web stuff. IT Bookshelf – Cyber Arms: Security in Cyberspace. Factoid: Why am I still hungry? Listening to mushrooms while watching TV in your car. Plus lots more — read it all, read it here on WServerNews

Cakes have layers, just like networks. Which layer of your network is most important to secure? Photo by Annie Spratt on Unsplash
Help spread the news!
Please tell all your colleagues and friends about WServerNews and let them know that they can subscribe to these and other TechGenix newsletters for free by going here. Thanks!!
Editor’s Corner
Network security is always a big concern for administrators of enterprise networks, and the rush towards remote work at the start of the COVID-19 pandemic only served to emphasize its importance. IPsec has traditionally been the technology of choice, and it’s widely used for connecting remote workers to the corporate office using virtual private network (VPN) products or services. IPsec is less widely deployed internally on corporate networks however because of the complexity of configuring it in large heterogeneous networks. SD-WAN is another solution that is displacing VPNs in many enterprises, though as this Cisco Community article illustrates SD-WAN can be even more complex to deploy than traditional IPsec—unless you buy their products of course.
IPsec however operates at layer 3 of the OSI networking model and for some organizations that might not be enough as far as network security is concerned. That’s why I was very interested to read Ethernet Encryptor Market Overview (PDF) a whitepaper by Christophi Jaggi which has recently been updated to cover new concepts and technologies. By using technologies that encrypt network communications at the Data Link Layer (layer 2), Ethernet networks of all shapes and sizes ranging from the carrier level to single enterprises can have a greater degree of security that IPsec-based solutions. Solutions from vendors like the Thales Group and atmedia GmbH that encrypt Ethernet traffic at layer 2 can give you more peace of mind since 99% of network attacks generally occur in layers 3 through 7. If worrying about network compromise and intrusion keeps you awake at night, it might be worthwhile for you to read what Jaggie says in his whitepaper about the capabilities of Ethernet encryptor solutions from different vendors because you might sleep better afterwards, knowing there’s hope for securing your network.
That’s all for my Editor’s Corner this week and I hope that you enjoy the remainder of this issue. Feel free to email me if you have comments or questions about anything in our newsletter.
Got questions? Ask our readers!
WServerNews goes out each week to almost 200,000 IT pro subscribers worldwide! That’s a lot of expertise to tap into. Do you need help with some technical problem or are looking for expert advice on something IT-related? You can Ask Our Readers for help by emailing us your problem or question. Do it today!
This Week in IT
A compendium of recent IT industry news compiled by Your Editors. Feel free to email us if you find a news item you think our newsletter readers might be interested in.
The rise of digital fraud was raised as a major concern during the recent two-day National Cyber Security Center (NCSC) conference in Wales, UK. For an overview of everything discussed see this article by Vuk Mujovic (TechGenix). Vic also as a good overview of the Tech.eu Summit that took place last week in Brussels. Data security, fintech, sustainability—these are all important issues as the EU tries to catch up to tech competitors in America and Asia.
Along these lines it’s important to be aware that EU countries and lawmakers have recently agreed on tougher cybersecurity rules for key industry sectors including energy, transport and finance (Reuters). These new rules significantly expand the scope of the NIS Directive, and give how greatly GDPR legislation has impacted companies worldwide one would be well advised to pay close attention to what the EU is bringing forward. Even those working in IT in Europe itself are facing challenges as Martin Urwaleck, an IT leader working in Austria, indicated to me recently when he said “We have no details yet but NIS2 is definitely more demanding than ISO27001 and I have to be prepared.” We’ll try to stay ahead of the curve on this topic for our European newsletter subscribers. If you have any more news to report on NIS2 please email us.
Returning to the UK for a moment, the news that (ISC)2 has launched a free scheme to get 100,000 UK citizens into cybersecurity is a welcome initiative given the ongoing shortage in the industry (ITPro). The program is open to UK residents who do not already hold an (ISC)2 cybersecurity certification. If you’re interested you can apply here.
Not to be left behind in the rush to bolster the security of our increasingly online world, the Open Source Security together with the Linux Foundation has set forth a 10-point plan to improve the security and resilience of open source software. The plan was announced at the Open Source Software Security Summit II that took place recently in Washington DC. The plan it’s worth looking at though it’s probably too ambitious to ever be realized completely
And finally comes news about how security researchers developed a tool for scanning popular office software. By using the tool they were able to discover numerous previously unidentified bugs in such programs as Microsoft Word, Adobe Acrobat, and Foxit Reader, and as a result they netted around 22k USD in bug bounty rewards. I guess there’s money in pest control, even for IT professionals!
Windows news
I was startled recently when I wanted to use Quick Assist to provide support for a user over a remote connection. Quick Assist is a feature of Windows 10 that lets a person share their device with someone else and view their display and/or take over control of their machine. I’ve used it many times in the past to resolve support problems, but when I pressed Ctrl + Winkey + Q this time to launch the Quick Assist program, I was greeted by the following message:

What’s this? The Microsoft Store?! Yech!!
A little googling showed that I wasn’t the only admin who was frustrated about Microsoft ending support for the native version of Quick Assist in Windows 10 and forcing users to use the Store to install the new version (Günter Born). Bad move, Microsoft, stop trying to push the Store by removing built-in functionality from Windows.
And in other news Canonical has now made preview builds of Ubuntu available on the Microsoft Store (Ubuntu Blog). This means that if you use Windows Subsystem for Linux you are no longer limited to running Long Term Supported (LTS) releases of Ubuntu on Windows 10 and Windows 11 (BetaNews).
***HOT TIP*** We thought we’d stick this into the news section even though it’s not strictly news about Windows. If you’re tired of being forced to create a Microsoft Account when you’re setting up a new installation of Windows 11, you’ll want to read this article on Neowin that explains step-by-step how you can bypass the Microsoft Account requirement when setting up Windows 11 with an Internet connection. The downside of course is that when Windows 12 arrives Microsoft will probably make it even more difficult to set up a new Windows installation without having or creating a Microsoft Account.
Windows Server news
***ALERT***
CISA warns not to install May Windows updates on domain controllers (BleepingComputer).
(Too late, probably!)
***ANOTHER ALERT***
Check out this tweet by Ryan Ries:
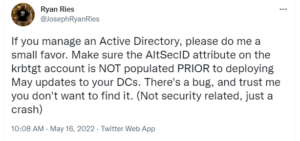
It was unclear to me at first who might be affected by this issue as several colleagues have indicated this attribute is not configured in their AD database. The after some more research I stumbled across this tweet by Kevin Beaumont:

It might be best to stay tuned to commenters on both of these tweet threads if you have AD DS deployed in your environment.
Upcoming webcasts, events and conferences
Got an event, conference or webcast you want announced in our newsletter? Email us!
FREE WEBINAR: Leveraging Your ICS Community with Collective Defense and Request for Assistance – May 26/27 – Register Now
(AOVPN) Always-On Virtual Private Network DPC Webinar Q&A: Richard Hicks and Leo D’Arcy – Sponsored by PowerON – UK session on June 7; US session on June 16 – Register here
Reminder of HPE Discover 2022 in Las Vegas on June 28-30 – Register today!
Also be sure to check out Redmond Channel Partner’s calendar of upcoming Microsoft conferences for partners, IT pros and developers!
Got comments about anything in this issue?
Email us! We love hearing from our readers!
Meet the Editors!
MITCH TULLOCH is Senior Editor of WServerNews and is a widely recognized expert on Windows Server and cloud technologies. He has written more than a thousand articles and has authored or been series editor for over 50 books for Microsoft Press and other publishers. Mitch has also been a twelve-time recipient of the Microsoft Most Valuable Professional (MVP) award in the technical category of Cloud and Datacenter Management. He currently runs an IT content development business in Winnipeg, Canada that produces books, ebooks, whitepapers, case studies, courseware, documentation, newsletters and articles for various companies.

INGRID TULLOCH is Associate Editor of WServerNews. She was co-author of the Microsoft Encyclopedia of Networking from Microsoft Press and collaborated on developing university-level courses in Information Security Management for a Masters of Business Administration (MBA) program. Ingrid also manages Research and Development for the IT content development business she runs together with Mitch.
Subscribe today to WServerNews!
Subscribe today and join almost 200,000 other IT professionals around the world who subscribe to our newsletter! Just go to this page and select WServerNews and you’ll receive it every Monday in your inbox.
IT Workshop – tools, whitepapers and more
Got a product or solution or some other resource you’d like to tell our readers about? Email us!
Our TOOL OF THE WEEK is Unlimited Secure Email a solution from GFI Software that gives you collaboration tools plus the security of four anti-virus engines, four advanced content filtering engines, and fourteen anti-spam engines.
Looking for a guide to navigate the labyrinth of network security? Check out this new article by John Villanueva: What Is Network Security and Why It Is Essential to Your Business (TechGenix).
One of the most important things to train your employees on is how to avoid getting scammed in ways that could impact your business. Check out this article by Stu Sjouwerman on why people fall for scams.
Here are some tools from IgniteTech for businesses involved in manufacturing, warehousing and supply chain management:
- PurchasingNet helps you optimize your organization’s procurement processes to lower costs and improve supplier management.
- Tradebeam leverages lean principles to provide manufacturers and their suppliers with real-time insight and control over inventory.
- Gensym applications control & automate industrial systems, large machinery, manufacturing processes and more.
- With Gemini mobile data management, keep your manufacturing and warehouse operations in sync — no matter what the future brings.
And here are some reviews from Tom’s Hardware you should check out if you’re looking for a good password manager:
- Keeper Password Manager Review: Checks All the Boxes
- Dashlane Review: Solid, Web-Based Password Management
- LastPass Review: Great password management for a price
Tips and Tutorials
Got tips or tutorials you’d like to recommend for our readers? Email us!
We thought we’d try organizing our tips & tutorials in this section according to platform & product instead of our usual mix & match method. Do you find this more helpful? Let us know!
PowerShell:
How to Fix Windows 11 SSD Problem Using PowerShell (ITPro Today)
Microsoft PowerShell lets you track Windows Registry changes (Bleeping Computer)
Should You Use Strict Mode for Your PowerShell Scripts? (TechGenix)
Getting Started with PoshBot (Rambling Cookie Monster)
Windows Server:
Windows Server 2022 SFTP (PeteNetLive)
DHCP: How to work with user classes on Windows (NetworkWorld)
How to Create a Windows server 2022 SOFS Cluster on a VM (Robert Smit MVP Blog)
Web stuff:
How to use Telegram on your PC (OnMSFT)
Discourse is the Future of Web Forums (Linux Journal)
How to benchmark a website with the Siege command-line tool (TechRepublic)
Freebies!!
Got a freebie you want to offer our readers? You can reach almost 200,000 IT pros worldwide with our newsletter—email us!
Volume 3 of SysAdmin Horror Stories is now available from Altaro. BWA-HA-HA-HA!!!
Panda Free Antivirus provides free protection for your Windows and Android devices. Read the review on ITPro.
IT Bookshelf – Cyber Arms: Security in Cyberspace
Cyber Arms: Security in Cyberspace (CRC Press, 2020) is already several years old but in my opinion it still remains the best overview on the subject of cyber warfare. The book describes in detail both the offensive landscape of cyberspace and countermeasures organizations can use for cyber defense.
The first portion of the book focuses on the offensive side, starting with an excellent overview of how cyber warfare has evolved since the computing age began. The cyber arms industry is summarized in detail with a discussion of the accessibility of tools for launching cyber attacks. Details concerning the cyber arms industry infrastructure are presented along with a description of the various marketplaces where offensive tools can be procured. Case studies of different cyber warfare incidents and operations are highlighted along with various strategies and tactics used by the attackers.
The second part of the book focuses on cyber defense and countermeasures. Cryptography and access control are discussed, and different kinds of vulnerabilities are explained. Different cyber defense strategies are presented corresponding with different kinds of exploits, and much of this information was already familiar to me. What I found most interesting however is the detailed discussion of vulnerabilities in nuclear weapons systems and the role of artificial intelligence (AI) in developing autonomous weapons systems (AWS), an area of engineering technology that is receiving much attention in certain nations and which in my opinion is leading us towards a dangerous cyber arms race from which the world may not survive. The closing section of this part that focuses on U.N. initiatives towards international regulations on cyber conflicts are laudable but seem woefully inadequate in the light of what’s currently happening with the hybrid war different nations have become involved in because to the Ukraine/Russia conflict.
The final short section of the book deals with future challenges involving next-gen cyberattacks and cyber-physical weapons. My hope is that the authors of this book, who are excellent writers in my opinion, will bring out a second edition soon that brings us up to date on the latest incidents, strategies, systems, tools and regulatory initiatives in the rapidly evolving field of cyber warfare.
You can buy Cyber Arms: Security in Cyberspace on Amazon here.
Factoid: Why am I still hungry?
No hits by readers on last week’s factoid so here’s another one to think about:
Fact: Doritos Cuts Number of Chips in Each Bag, Blames Bidenflation (The Washington Free Beacon)
Source:https://freebeacon.com/latest-news/doritos-cuts-number-of-chips-in-each-bag-blames-bidenflation/
Question: Personally I *hate* shrinkflashion, I’d much prefer that a business I buy something from raise the price on a unit instead of reducing the amount it contains or delivers. How do our readers feel about this? And what’s the worst example you’ve seen recently? I’m sure you’ve encountered this phenomenon lately with how oil and gas prices have skyrocketed causing prices to go up on everything by 20-30% (which is the reality compared to the so-called “official” inflation rate that our governments and the news media are feeding us. Email us your answer and we’ll include it in our next issue!
And Finally
The odd, the stupid and the remarkable. Good for your mental health.
Mushrooms communicate with each other using up to 50 ‘words’, scientist claims (The Guardian)
https://www.theguardian.com/science/2022/apr/06/fungi-electrical-impulses-human-language-study
[I wonder what they would say to dolphins?]
Pinterest bans climate change misinformation with new policies (BetaNews)
https://betanews.com/2022/04/08/pinterest-bans-climate-change-misinformation-with-new-policies/
[I’d be happier if they could ban climate change entirely!]
Enjoy This Animatronic Eyeball’s Smooth Moves (Hackaday)
https://hackaday.com/2022/04/08/enjoy-this-animatronic-eyeballs-smooth-moves/
[Here’s looking at you, kid.]
Startup Plans Nuclear-Powered Data Centers on the Moon (Tom’s Hardware)
https://www.tomshardware.com/news/company-plans-to-put-datacenters-on-the-moon
[It’ll take a pretty long run of fiber optic cabling to connect those datacenters with us here on Earth.]
Highway Code: Watching TV in self-driving cars to be allowed (BBC News)
https://www.bbc.com/news/technology-61155735
[Oh, great. What could possibly go wrong?]
Hey reader! Got an amazing or weird or funny link you’d like to suggest for this section of our newsletter? Email us! But please make sure that it’s G-rated as in “Gee whiz”, “Golly!”, Good grief!”, “Gaaahh!!” and so on. Thanks!
Please tell others about WServerNews!
We hope you enjoyed this issue of WServerNews! Feel free to send us feedback on any of the topics we’ve covered—we love hearing from our readers! And please tell others about WServerNews! It’s free and always will be free—and they can subscribe to it here. Thanks!!!
