
Firewalls are the first line of defense for any organization. Essentially, they’re a barrier between your network and the internet. They filter all traffic and block data that meets the patterns of an attack. You have many types of firewalls to choose from, but in this article, I’ll highlight the differences between a traditional firewall and a next-generation firewall (NGFW).
Because attacks are becoming more sophisticated, firewalls also need to evolve. Particularly, they need to protect from ransomware and man-in-the-middle (MITM) attacks. As a result, firewalls are changing.
So, what are these changes? How do the traditional and NGFW stack up against each other? How can you choose one over the other for your organization?
Read on as I answer these questions and more in this article. But before going any further, let’s understand what these two types of firewalls are.
What Is a Traditional Firewall?
A traditional firewall has limited capabilities when compared to an NGFW. It inspects the traffic that enters or exits a network. Specifically, it examines the state of the packet, source/destination IP address, port number, and protocol. If any of these match with any banned IP addresses, ports, or protocols, the firewall raises an alarm. In other words, it only exercises control over the flow of packets in one or both directions. Many traditional firewalls also come with Virtual Private Network (VPN) capabilities.
Let’s move on to next-generation firewalls next.
What Is a Next-Generation Firewall (NGFW)?
An NGFW is an advanced firewall that uses static and dynamic filtering strategies to filter packets based on applications. As a result, these firewalls provide wide-arching control and visibility over the data that enters and exits your network. Furthermore, NGFW comes with features such as Intrusion Protection Systems (IPS) and Deep Packet Inspection (DPI). That way, they block malware and viruses from entering your network.
A mere glance at the two shows that the NGFW is more advanced, and technically more sophisticated, than a traditional one.
But in which areas do they differ? That’s exactly what you’ll see next. I’ll compare the two types of firewalls against several features. Let’s briefly talk about the features before comparing the two.
Important Firewall Features
These features are important for you to consider when choosing between a traditional firewall and a next-generation firewall. One feature might be preferable more than another based on your organization’s needs. Here’s a brief overview of each feature:
Stateful vs Stateless
Firewalls can be stateful or stateless. Stateful firewalls filter packets based on the packet’s complete context, and not just a single parameter like your port or IP address. On the other hand, stateless firewalls compare individual packets against established security conditions only such as source IP address, protocol, etc.
Out of the two, stateful firewalls can better detect forged messages, attacks, unauthorized access, malware, and more. They also come with extensive logging capabilities. However, these stateful firewalls are more prone to Distributed Denial of Service (DDoS) and Man-in-the-middle (MITM) attacks. Stateless firewalls, on the other hand, can detect advanced attacks, but can also fend off DDoS and MITM attacks.
Application Visibility
Application visibility and control is a security feature that allows firewalls to identify the application that created or sent the malicious data packet. This information is especially handy for developers; it allows them to quickly identify the security issue in an application and fix it immediately.
OSI Model Layers
The Open Systems Interconnection (OSI) model describes the inner workings of a network system. Here’s an image you can use for reference. Layer 1 is the physical layer, and it goes up to layer 7, which is the application layer.
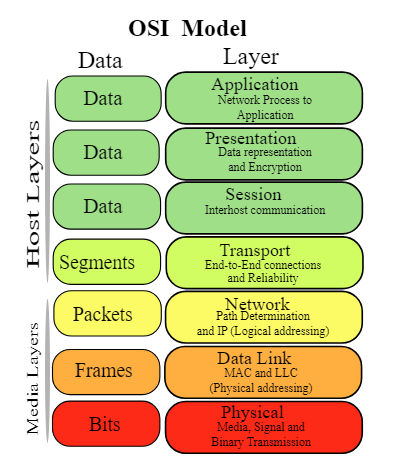
Communication starts from layer 7 and goes down to layer 1. Eventually, layer 1 transmits the data packets through the cable. Different firewall types operate on different OSI layers. As such, they may have more or less capabilities.
Application-Level Awareness
Application-aware firewalls offer a layer of security for corporate networks. This technology enables firewalls to inspect and control traffic to and from applications. Furthermore, they use this information to configure or block inputs/outputs from certain applications.
Reputation and Identity Services
Reputation and identity services in a firewall aggregate malicious IP addresses. They also provide a context for the data packets. In turn, this helps provide an identity and context to every packet for more efficient filtering.
Integration of Security Tools
Firewalls are no longer isolated tools; they now play a bigger role in an organization’s security infrastructure. This is why many firewalls support the integration of security tools. That way, they provide organizations with a comprehensive understanding of security vulnerabilities.
Decryption and Inspection of SSL Traffic
Encryption has become an essential part of data transmission today. Even cybercriminals encrypt malicious data packets. As a result, many firewalls can now decrypt the content and inspect the SSL traffic. Otherwise, malicious code could infiltrate your network.
NAT, PAT, and VPNs
Network Address Translation (NAT) maps the public IP addresses to private ones. Port Address Translation (PAT) maps multiple private IP addresses to a public one. Virtual Private Networks (VPNs) provide secure connections to your network. Now, these three technologies may not always work well with each other, but they work well with a firewall. Again, firewalls that support these three technologies provide better protection overall for your network.
IDS and IPS
Intrusion Detection Systems (IDS) and Intrusion Protection Systems (IPS) monitor the traffic on your network. After that, they match it with signature patterns. If they detect a match, an IDS alerts you. On the other hand, an IPS alerts and blocks the packet from entering your network. Undoubtedly, these protect better security for your network.
Now that you’re familiar with these features, let’s see which firewall ticks the most boxes. I’ll start with traditional firewalls.
Traditional Firewalls
As mentioned earlier, traditional firewalls have very limited features. Still, they’re a good starting point. Let’s see how a traditional firewall measures against the features above:
Stateful vs Stateless
Most traditional firewalls are stateless, though some can perform a stateful inspection. To clarify, they mostly compare incoming data packets against an existing list of malicious/banned IP addresses, ports, and protocols. Afterward, they raise a flag accordingly.
Application Visibility
Traditional firewalls only provide partial control and visibility. This is why many security threats easily go undetected in these firewalls. Developers also can’t rely on this info to remedy application vulnerabilities.
OSI Model Layers
Traditional firewalls only work in layers 3 and 4. These are the network and transport layers respectively. The network layer handles IP addresses The transport layer handles the TCP or UDP protocols. Since traditional firewalls only work in these layers, they can only monitor IP addresses and protocols.
Application-level Awareness
Traditional firewalls don’t support this feature and hence, can’t make intelligent decisions about application traffic. Also, they don’t analyze the data transmitted by applications. Therefore, their efficiency in blocking malicious traffic is very limited.
Reputation and Identity Services
Traditional firewalls don’t support reputation and identity services. Hence, they can’t help with data aggregation and dynamic filtering.
Integration of Security Tools
It’s extremely difficult to integrate security tools in traditional firewalls. In fact, they’re standalone systems. Additionally, you may have to manage each firewall separately, and this maintenance can be expensive.
Decryption and Inspection of SSL Traffic
Traditional firewalls don’t support decryption and inspection of SSL traffic, so encrypted malicious content can enter your network.
NAT, PAT, and VPNs
Traditional firewalls support all three technologies.
IDS and IPS
In traditional firewalls, the IDS and IPS systems aren’t integrated within the firewall itself. The two systems are only deployed separately.
Let’s dive into NGFWs next!
NGFWs
Stateful vs. Stateless
NGFWs are stateful firewalls. This translates to more precise filtering as they tend to see the entire context. These are also intelligent systems. They go beyond comparing a packet’s information against the“banned” list. They also make dynamic filtering decisions based on the entire context.
Application Visibility
NGFWs offer complete application visibility and control. They use specific methods such as signature matching and in-depth analysis to identify safe applications.
OSI Model Layers
NGFWs work in layers 2 to 7, which means they can get the complete context of a packet. In turn, this helps with making accurate filtering decisions.
Application-Level Awareness
NGFWs support application-aware monitoring. As a result, they go beyond just inspection and monitoring. They also perform a deep-packet analysis. After that, they identify any malicious content located within the packets. Needless to say, the protection offered is more comprehensive.
Reputation and Identity Services
NGFWs support reputation and identity services. Hence, they can provide intelligent and dynamic packet filtering. They can also aggregate the IP addresses or applications sending malicious packets. This can help your organization take the necessary actions to protect your networks.
Integration of Security Tools
NGFWs integrate easily with a growing number of security tools. This way, they can transfer data to a centralized log system. As such, they get a larger picture of the threat. They also help you connect well with incident tracking systems. Maintenance costs are lower as well.
Decryption and Inspection of SSL Traffic
NGFWs support decryption and inspection of SSL traffic. Through it, they also provide an additional security layer for your network.
NAT, PAT, and VPNs
NGFWs support these three technologies. They can extend them to integrate with more sophisticated technologies such as sandboxing. In turn, this protects your network from advanced threats like malware.
IDS and IPS
Most NGFWs come integrated with IDS and IPS capabilities. This reduces installation and maintenance costs of a separate IDS/IPS. Overall, it provides better security for your network.
And that’s it! That’s a lot of information to take in, but don’t worry. In the next section, I’ll simplify things for you if you.
Traditional Firewalls vs Next-Generation Firewalls: Feature Comparison Simplified
To sum up, here’s a table comparing traditional firewalls and NGFWs:
| Feature | Traditional Firewall | Next-Generation Firewall (NGFW) |
| Stateful vs Stateless | Mostly stateless | Always stateful |
| Application Visibility and Control | Partial and limited | Complete |
| OSI Model Layers | 3 and 4; only monitors IP addresses and protocols | Layers 2 to 7 for complete context |
| Application-Level Awareness | No | Yes |
| Reputation and Identity Services | No | Yes |
| Integration of Security Tools | Extremely hard | Easy |
| Decryption and Inspection of SSL Traffic | No | Yes |
| NAT, PAT, and VPNs | Supports | Supports and extends to include newer technologies |
| IDS and IPS | Deployed separately | Integrated |
From the above table and discussion, it’s clear that NGFWs are much better than traditional firewalls. In fact, they have better features to handle sophisticated attacks. Of course, they also come with downsides. Primarily, they take up too many resources. They also tend to be slower than traditional firewalls. Finally, they’re likely more expensive.
All this leads to the next question: how can you choose a firewall that’s well-suited for your organization? And that’s exactly what I’ll answer next.
How to Choose a Firewall
If you’re not sure how to make the best choice, I’m here to help. Here’s a step-by-step list of things to consider before choosing a firewall.
Step 1: List Your Requirements
Make a list of all the features you need in a firewall. To give you some examples, let’s say you have a remote working team that connects through a VPN. Since they’re constantly exposed to the internet, you’d want a firewall that performs a deep packet inspection.
So, understand your business requirements. Make a list of the features you need in a firewall before you try to purchase one.
Step 2: Size Your Hardware
This is an important, yet often overlooked, step in choosing a firewall. Understand your hardware. Figure out how much it can support. Ideally, you want a comprehensive and high-performing firewall. However, your underlying hardware needs to support it.
Likewise, understand your bandwidth and its utilization rate. Similarly, the average traffic volume is another metric to consider. Keep all these factors in mind while choosing your firewall. That way, you’ll choose a firewall that matches your capabilities.
Step 3: Choose a Suitable Brand
After this, you’ll have to select the vendor. This is a difficult choice as most leading companies have similar offerings. In this step, take your team’s inputs and their preference, or expertise. If a majority of your employees are comfortable with a certain brand, go for it. That’ll make your employees feel comfortable and involved. This will also reduce the training and onboarding time for your employees, especially if they aren’t familiar with certain brands.
Step 4: Consider Your Budget
Another important thing to consider is your budget. Do a bit of research to understand which firewall has most of the capabilities you need. Then, check if it’s priced within your budget. Sometimes, you might need to pick a cheap firewall with basic functions. Yet, it’s still better than not having a firewall in the first place. If your company can afford it, then you can go ahead and choose a more expensive firewall. Be ready to make some trade-offs here.
Step 5: Consider the Future
When choosing a firewall, plan for its scalability and ease of upgrade. Consider cloud-based firewall services if you can. These are flexible and scalable. It’s also better to know how you’ll use your firewall. Buy a firewall that can stay with you for a long time. Otherwise, you’d be wasting money. Finally, try to find a balance between cost and scalability!
Now, you should be able to make an informed decision about your firewall type. Finally, let’s see a neat recap of everything you need to know.
Which Firewall Is Best for My Organization
Many organizations today are moving towards NGFWs. After all, they have advanced features and increased capabilities for protecting your network. That said, they may not always be the best choice for you. Here are some pro tips that can help you decide:
Pro Tips
Choose a traditional firewall if you:
- Want a simple and fast firewall without any advanced features
- Have a tight budget and can’t spend much on a firewall
- Are just starting out, and you want a “beginner” firewall
- Don’t want your firewall to consume many computing resources in your organization
Choose a next-generation firewall if you:
- Want access to many more features than a traditional firewall
- Have a larger budget
- Are experienced with firewalls, i.e., this is not your first one
- Are able to dedicate more resources to it
And there you have it! I hope this information comes in handy when you’re choosing a firewall.
Final Words
To conclude, firewalls are your network’s first line of defense. As a result, they’re critical for your security. Yet, choosing a firewall isn’t easy, as many types of firewalls exist today. Broadly speaking, you have traditional firewalls and next-generation firewalls (NGFWs). The former is a relatively simple firewall that only examines the headers. Conversely, NGFWs are more advanced and provide comprehensive protection.
In this article, you learned about their differences across many aspects. Finally, you understood, through several steps, how you can choose the appropriate firewall for your organization. Remember, even a traditional firewall is better than no firewall.
Do you have more questions about traditional and next-generation firewalls? Check out the FAQ and Resources sections below!
FAQ
Are stateful and stateless firewalls similar?
No, stateful firewalls can detect the complete state of traffic and its flow. Then, they can make intelligent decisions. A stateless firewall, on the other hand, only checks packets against preset rules. After that, it raises flags if it detects any anomaly.
Can I get log data with my firewall?
Yes, you can get log data with your firewall. It’s important to monitor your logs from time to time. For example, you might have added some new rules to your firewall. In that case, examining the logs can help you see if these rules require further debugging. If you have a centralized logging feature and want your log information to move there, then consider purchasing an NGFW.
Can a traditional firewall block malware?
No, a traditional firewall can’t block malware. It also can’t stop any of the other Advanced Persistent Threats (APTs), such as cyber espionage and eCrimes. To counter these threats, you’ll need a next-generation firewall (NGFW). It comes with advanced features such as deep packet inspection (DPI), filtering, decryption, and SSL inspection.
Do I need an NGFW?
This depends on your infrastructure and your available resources. NGFWs consume more resources. They also require the necessary supporting hardware for optimal performance. At the same time, they offer comprehensive protection. So, if you need the protection and can afford the infrastructure and resources, go for it.
How do I choose a firewall?
Simply put, you must take into account your organization’s firewall requirements. Then, see which firewall meets these requirements. It’s also important to try and find a good balance between cost and features. Finally, consider factors such as flexibility and scalability when making this choice.
Resources
TechGenix: Newsletters
Subscribe to our newsletters for more quality content.
TechGenix: Article on the Best NGFWs for Your Organization
Read this article to learn more about the best NGFWs for your organization.
TechGenix: Article on the 8 Types of Firewalls
Understand the 8 types of firewalls for your organization.
TechGenix: Article on Firewall as a Service
Learn more about Firewall as a Service.
TechGenix: Article on the Best Firewalls for SMBs
Educate yourself on the best firewalls for SMBs.
TechGenix: Article on the Best Firewall Strategies
Decide if you must choose between a single or multi-vendor for your firewall.



