
Source: Unsplash
Okta, an identity provider with over 17,000 customers, 7,000 integrations, and 100 million individual users, has reported that cybercriminals accessed its GitHub repositories earlier in December. However, operations and user credentials remained safe in the breach. In response, Okta notified law enforcement, restricted access on GitHub, rotated GitHub credentials, and suspended GitHub integrations with third-party applications. Additionally, it investigated all its recent commits to validate code integrity.
Gartner regards Okta as a good identity provider platform and a leader in access management. It has also received high ratings in the Forrester Wave ™ Identity As A Service For Enterprises Q3 2021 report. In the report, it beat the likes of IBM, Microsoft, Oracle, SecureAuth, OneLogin, and CyberArk. Okta offers identity provider solutions to companies in various sectors. These sectors include public, finance, retail, healthcare, travel and hospitality, technology, energy, and nonprofit.
Okta GitHub Code Repositories Breached

Source: Bleeping Computer
Bleeping Computer was the first to report the breach when it obtained a confidential email sent to “Okta Advisory.” The email contents were largely the same as the official Okta update. Yet, both avoid explaining how cybercriminals managed to gain access to the GitHub repositories, especially when they were private and not public.
Despite the cybercriminals’ successful attempt at breaching the code, no damage was done. The company confirmed that “Okta does not rely on the confidentiality of its source code for the security of its services.” However, it has faced criticism in the past for causing unreasonable delays before alerting customers to a security breach.
The breach relates to Okta Workforce Identity Cloud (WIC) code repositories and not Auth0 (Customer Identity Cloud) products. Customer Identity Cloud offers authentication services for consumer and SaaS applications. Workforce Identity Cloud offers authentication for employees, contractors, and partners.
Okta successfully thwarted the cybercriminals’ aims because it uses zero-knowledge architectures. Recently, the LastPass credentials management platform was also breached. But cybercriminals were unsuccessful in stealing customer credentials in that case as well.
Okta Identity Provider in the Crosshairs
Source: Group IB
This isn’t the first time that Okta has been in the crosshairs of cybercriminals. Identity providers are prized targets for bad actors. This is because they hold access to better quality and quantity of user information. Exploiting an identity provider gives attackers access to applications that could potentially be without multi-factor authentication protocols.
In Jan. 2022, an attack on Okta affected 2.5% of its customers, a total of 375 businesses. Lapsus$—the data-extortion group—was behind the attack, which came after a support engineer’s laptop, with superuser privileges, was compromised. Fortunately, as per Okta, “Support engineers are also able to facilitate the resetting of passwords and multi-factor authentication [MFA] for users, but are unable to obtain those passwords.”
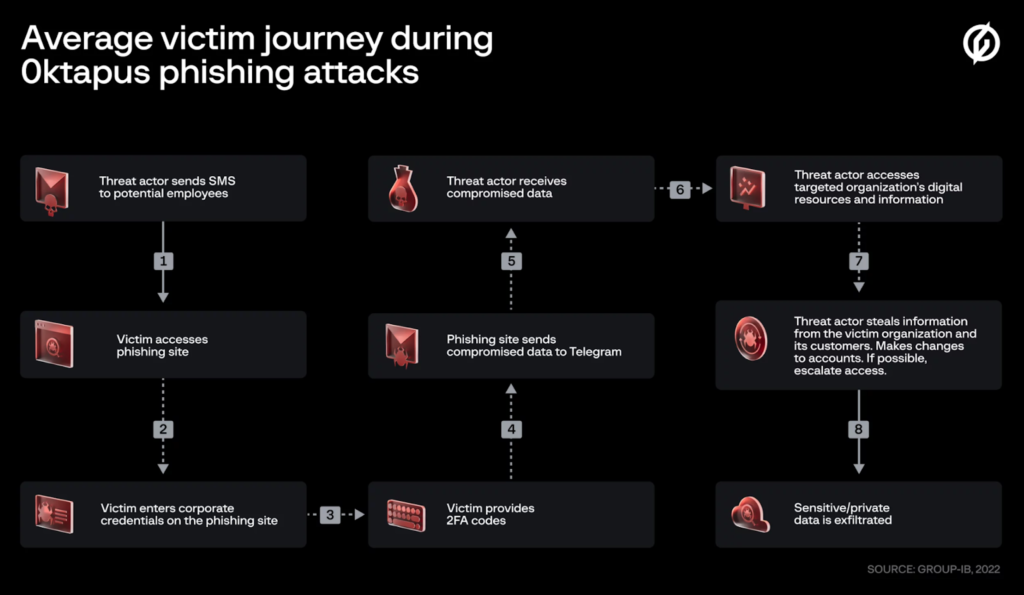
In Aug. 2022, Group IB released a blog titled Roasting 0ktapus: The Phishing Campaign Going After Okta Identity Credentials. Describing the aims of the attack, the blog wrote that cybercrime groups are targeting multi-factor authentication to overcome enterprise identity access management (IAM). This is so they can target supply chains. The attackers socially engineered Twilio and Cloudflare employees to gain access to their Okta user credentials.
Though only partially successful, the attack’s level of sophistication, complexity, and quality of execution are worrying. 0ktapus mostly targets cloud services, IT, and software development companies. Eventually, persistence may pay off for the cybercriminals, with deadly consequences for the wider economy, if security liabilities continue to exist.
What about GitHub’s Liability?

Source: GitHub
GitHub is a software development environment that entities in both public and private spaces heavily rely on. Development teams on GitHub use uploaded packages in the GitHub repositories. Since malicious code is hard to find immediately, it can spread and infect many systems before the vulnerability is found and patched. Unfortunately, this allows cybercriminals enough time to inflict damage.
Although just about anyone can upload packages to GitHub, the platform has recently announced plans to implement mandatory 2FA and also rolled out its secret scanning tools free to all users. In light of these developments, the GitHub ecosystem will become far more secure. These security innovations are welcome signs that highlight collaboration between larger organizations in combating sophisticated cybercrime with commonly accepted standards.
But, systems security is multifaceted and should rely on internal security protocols, such as next-generation firewalls, automated patch management, network monitoring, and endpoint detection. In addition, companies can use tools that find and patch known exploits. For example, Google’s OSV scanner tool, which it recently released, scans databases for known security vulnerabilities. Yet, despite these offerings available, many companies will ignore them. In doing so, they will expose larger supply chains to risks.
Okta Remains Secure
As Okta states on its website, “Everything starts with identity.” Compromised user credentials can lead to system-wide breaches. As an identity provider, Okta ensures legal compliance, user authentication, and business efficiency.
In this incident, Okta’s user authentication successfully denied cybercriminals from gaining anything of significance. And even more impressively, the Okta identity provider platform has yet to lose a single key pair for a single client to the attackers.
This incident also highlights the importance of introducing 2FA for all employees. By doing so, even if cybercriminals compromise a third-party identity provider, they’ll be unable to access user credentials in most cases.



