If you would like to read the other parts in this article series please go to:
- OSI Reference Model: Layer 1 Hardware
- OSI Reference Model: Layer 2 Hardware
- OSI Reference Model: Layer 4 Hardware
If you would like to be notified when Russell Hitchcock releases the next article in this series please sign up to the WindowsNetworking.com Real time article update newsletter.
In my last two articles I discussed the Open System Interconnect (OSI) reference model and its first two layers. In this article I will discuss the third layer; the network layer. The network layer is concerned with getting data from one computer to another. This is different from the data link layer (layer 2) because the data link layer is concerned with moving data from one device to another directly connected device. For example, the data link layer is responsible for getting data from the computer to the hub it is connected to, while the network layer is concerned with getting that same data all the way to another computer, possibly on the other side of the world.
The network layer moves data from one end point to another by implementing the following functions:
-
Addressing
-
Routing
-
Encapsulation
-
Fragmentation
-
Error handling
-
Congestion control
Addressing
Those who have read my previous article may be curious why layer 3 implements addressing when I also said that layer 2 implements addressing. To cure your curiosity, remember that I wrote that the layer 2 address (the MAC address) corresponds to a specific network access point as opposed to an address for an entire device like a computer. Something else to consider is that the layer 3 address is purely a logical address which is independent of any particular hardware; a MAC address is associated with particular hardware and hardware manufacturers.
An example of layer 3 addressing is the Internet Protocol (IP) addressing. An illustration of an IP address can be seen here in figure 1.
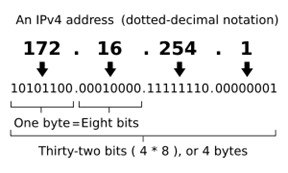
Figure 1: Illustration of an IP address (Source:Wikipedia.com)
Routing
It is the job of the network layer to move data from one point to its destination. To accomplish this, the network layer must be able to plan a route for the data to traverse. A combination of hardware and software routines accomplish this task known as routing. When a router receives a packet from a source it first needs to determine the destination address. It does this by removing the headers previously added by the data link layer and reading the address from the predetermined location within the packet as defined by the standard in use (for example, the IP standard).
Once the destination address is determined the router will check to see if the address is within its own network. If the address is within its own network the router will then send the packet down to the data link layer (conceptually speaking that is) which will add headers as I described in my previous article (link previous article to my OSI Layer 2 article) and will send the packet to its destination. If the address is not within the router’s own network, the router will look up the address in a routing table. If the address is found within this routing table the router will read the corresponding destination network from the table and send the packet down to the data link layer and on to that destination network. If the address is not found in this routing table the packet will be sent for error handling. This is one source of errors which can be seen in data transmission across networks, and is an excellent example of why error checking and handling is required.
Encapsulation
When a router sends a packet down to the data link layer which then adds headers before transmitting the packet to its next point, this is an example of encapsulation for the data link layer.
Like the data link layer, the network layer is also responsible for encapsulating data it receives from the layer above it. In this case it would be from the data received from layer 4, the transport layer. Actually, every layer is responsible for encapsulating data it receives from the layer above it. Even the seventh and last layer, the application layer, because an application encapsulates data it receives from users.
Fragmentation
When the network layer sends data down to the data link layer it can sometimes run into trouble. That is, depending on what type of data link layer technology is in use the data may be too large. This requires the network layer have the ability to split the data up into smaller chunks which can each be sent to the data link layer in turn. This process is known as fragmentation.
Error handling
Error handling is an important aspect of the network layer. As I mentioned earlier, one source of errors is when routers do not find the destination address in their routing table. In that case, the router needs to generate a destination unreachable error. Another possible source of errors is the TTL (time to live) value of the packet. If the network layer determines that the TTL has reached a zero value, a time exceeded error is generated. Both the destination unreachable error and the time exceeded error messages conform to specific standards as defined in the Internet Control Message Protocol (ICMP).
Fragmentation can also cause errors. If the fragmentation process takes too long, the device can throw an ICMP time exceeded error.
Congestion control
Another responsibility of the network layer is congestion control. As I am sure you know, any given network device has an upper limit as to the amount of throughput the device can handle. This upper limit is always creeping upward but there are still times when there is just too much data for the device to handle. This is the motivation for congestion control.
There are many theories for how to best accomplish this, most of which are quite complicated and beyond the scope of this article. The basic idea of all of these methods is that you want to make the data senders compete for their messages to be the ones to get accepted into the throughput. The congested device wants to do this in a way that lowers the overall amount of data it is receiving. This can be accomplished by ‘punishing’ the senders which are sending the most data which causes the senders to ‘slow’ their sending activity to avoid the punishment and thereby reducing the amount of data seen by the congested device (which at this point is no longer congested).
Author’s rant: The congestion control algorithms are quite complex for various reasons. Firstly, the mathematics involved is intense. So, for all of you who have ever wondered why people study mathematics in university and what job they could possibly get with that education…. this is an important one, and one that pays well with networking companies such as CISCO and Nortel. Secondly, after you have determined the proper mathematics to accomplish this task, how can it be implemented in a efficient and fast manner? This is the domain of engineers, who need to understand the mathematics, possible software implementation strategies, possible hardware implementation strategies, and design methodologies. Many people, including those who work in the tech industry, do not really understand what these, and other, professions bring to the table: they should. It is important.
In my next article I will discuss the fourth layer of the OSI reference model; the transport layer. Until then, as always, if you have any questions about this or any previous article please feel free to send me an email; I will do my best to answer any and all questions.
If you would like to read the other parts in this article series please go to:
- OSI Reference Model: Layer 1 hardware
- OSI Reference Model: Layer 2 Hardware
- OSI Reference Model: Layer 4 Hardware
If you would like to be notified when Russell Hitchcock releases the next part of this article series please sign up to the WindowsNetworking.com Real time article update newsletter.



