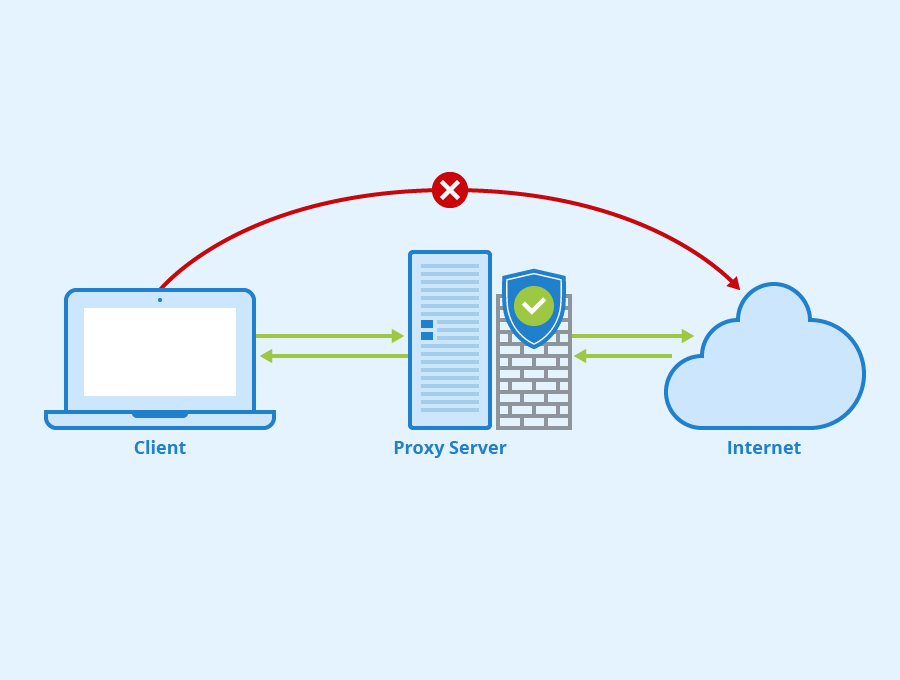
Proxy servers are fundamentally used to hide the IP address of a client from the internet. A proxy server takes the form of an agent, which then takes a client’s request and passes it to the internet destination and vice versa.
When connected to a proxy server, traffic uses the server’s IP address, and not the client’s. Proxy servers help hide users who are typical targets for malware attacks. This often includes CEOs, board members, division leads, and IT professionals. These individuals are usually targets because they have the authority to escalate permissions. They also have access to sensitive data.
In this article, I’ll explain what a proxy server is and how you can use one to protect yourself from cyberattackers. Let’s go ahead and start with a simple definition!
What Is a Proxy Server?
Proxy servers work at the network’s perimeter behind the exterior firewall to relay data between network users and the internet. Their primary goal is to hide an end-user’s IP from the Internet, making it harder to target key people of an organization. Hiding the IP addresses of clients is called network address translation (NAT). Often, firewalls and routers perform this NAT function.
Proxy servers can act as a caching mechanism to speed up transactions, reduce network traffic, and improve performance. They do this by holding previously requested content locally. This data is only replaced if it doesn’t meet the specific request by the end-user.
In addition to that, you can use proxy servers to also control traffic, both inbound and outbound. Most firewalls, such as those from Norton and Bitdefender, also have this IP filtering function. In general, look for fourth-generation or higher firewalls. These often ship with IP filtering and other useful administrative capabilities.
Moreover, logging traffic can be very useful for networks that need to meet specific security audit requirements or de-facto industrial standards.
Lastly, you can even use proxy servers to bypass a firewall. For instance, a user in a local area network (LAN) may wish to check a blocked IP address like Twitter or another social media website. To get around this, that user might install a proxy server at home that they can connect to and access the blocked website. In this case, you can also use a VPN, but proxy servers give owners access to their own network and content remotely.
In addition to these use-cases, you can also use a proxy as a reverse proxy. Let’s talk about those now.
What Is a Reverse Proxy Server?
A reverse proxy server hides the server an end-user is connecting to. This is the exact opposite of the proxy server scenario mentioned above. Companies like Google or Amazon use this process to hide which the server being used. It also helps with load-leveling, caching, and logging.
A reverse proxy server also allows companies to do something unique like offering new features to only some of the users of their solution; this is a canary deployment. You can test deployment on a group of users. If it’s a success, you roll it out to other servers in the network.
Another feature is that you can use reverse proxies to control internal traffic access from external users, much like a router or later-generation firewall.
Now that you understand more about proxies, let’s see how they work with cybersecurity overall.
Proxy Servers and Cybersecurity
The fundamental use of proxy servers is to hide a user’s IP or the IP of internal servers depending on your setup. This is vital for network cybersecurity, as most cyberattacks need to gain access to specific target machines. Furthermore, cyberattackers might need to scalp credentials from a victim to escalate a fake user’s permissions.
Attackers use IP addresses to map out the internal infrastructure to find out what they can exploit in a network.
Blocking IP addresses can make it difficult for cybercriminals to target specific users or platforms. You can also use geo-filtering to stop attackers from accessing websites from regions of the world that don’t conduct business with the organization.
In addition, you can also use proxy servers to create a demilitarized zone (DMZ) that enables any traffic to enter a no-trust segmented network zone. Through this setup, you can use proxies as a gateway to services and log traffic. By doing this, users need explicit, not implicit, trust to do anything in this zone.
And there you go, you’re now much more educated on proxy servers than you were about five minutes ago. You can now easily protect your users or infrastructure from any external threat. Let’s wrap up.
Final Thoughts
Proxy servers enable you to protect your users or your platforms by hiding the IP addresses used. You can also use them to cache data to improve a network’s performance, log access to the network, and filter traffic through inbound and outbound access controls.
Nowadays, proxy servers share a lot of similarities with modern routers, with vendors adding more integrated features over time to beat competitors. If you decide not to use a proxy server, then you can set up your perimeter and how it operates through most commercial routers.
Do you have any more questions about proxy servers? Check out the FAQ and Resources sections below!
FAQ
What is a proxy server?
Proxy servers hide the IP address of a client from the Internet. These servers become an agent that takes a client’s request and passes it to the Internet destination and vice versa. When connected to a proxy server, traffic uses the proxy’s IP address, and not the clients. In essence, they help hide users who are typically targeted for malware attacks, such as CEOs.
How can I hide my IP address when connecting to the internet from my LAN?
You can use a proxy server for all local area network (LAN) connections to the Internet. This enables you to use the proxy’s IP and not your client machine’s IP. This is very useful, as it can stop a cyberattacker in their tracks. You can achieve something similar with a VPN and create IP filtering with a filtering with a firewall.
How does proxy server caching work?
You can use a proxy server to hold data requested by users on the local area network (LAN). This includes webpage images, videos, or other large assets. When a user requests the page, these assets can complete the request faster than retrieving it from a remote server. You can use this to improve network performance overall.
Can my users access the Internet if I use a proxy server?
If you’ve set up a proxy server, then all users will connect through it using the proxy server’s IP to exchange requests with the internet. This enables you to cache data to improve network performance and log who’s accessing your network. Also, ensure your perimeter firewall is fully set up between the proxy server and the Internet.
What is a reverse proxy server?
Companies like Amazon use reverse proxy servers to hide servers the user accesses for services. This makes it more difficult for attackers to target the network. You can also use reverse proxies for IP filtering, internal routing, and testing new platform rollouts on only some users; this is called a canary deployment.
Resources
TechGenix: Article on Proxy Servers and Firewalls
Learn what the difference is between proxy servers and firewalls.
TechGenix: Article on Fuzzing
Discover how fuzzing can be potentially used to gain useful information about your business.
TechGenix: Article on Malware Attacks
Get to know more about the different types of malware you’ll encounter in the wild.
TechGenix: Article on GRC
Find out what you need to keep your business safe with governance, risk, and compliance.
TechGenix: Article on SOX Compliance
Get to grips with SOX Compliance.



