If you missed the first part in this article series please read Publishing Exchange Client Access with ISA 2006 – The Complete Solution (Part 1).
If you would like to read the next part in this article series please go to Publishing Exchange Client Access with ISA 2006 – The Complete Solution (Part 3)
Exchange 2003 Front-End Configuration
Now we have to make some changes to the Exchange 2003 configuration so that ISA Server Web client publishing works properly:
- Confirm forms-based authentication is not selected on the Exchange front-end server
- Enable RPC over HTTP on the front-end Exchange server
- Require secure channel (SSL) communications to the Web site
- To confirm that forms-based authentication is not selected on an Exchange front-end server, start Exchange System Manager, expand Servers, and then expand your front-end server. Expand Protocols, expand HTTP, right-click Exchange Virtual Server, and then click Properties. Click the Settings tab, and clear the check box Enable Forms Based Authentication. Click OK.
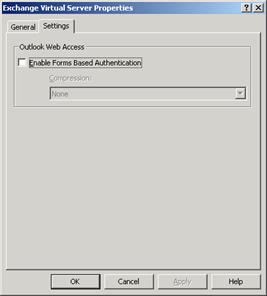
Figure 1
- To make your Exchange Front-End server an RPC proxy server, expand Servers, right-click your front-end server, and then click Properties. Select the RPC-HTTP page, select RPC-HTTP front-end server, and click OK to close the properties dialog box for the selected server. Click OK.
- After a certificate is installed for the Web site, you need to require the Web site to only accept secure channel communications. In IIS Manager, expand the local computer, and then expand the Web Sites folder. Right-click the /Exchange virtual directory and click Properties. On the Directory Security tab click Edit. Select Require secure channel (SSL) on the Secure Communication page and then click OK. Click OK again to close the Web site properties dialog box. Repeat this step for /Public, /Exchweb and /rpc.

Figure 2
Exchange 2007 Client Access Configuration
For Exchange 2007, the required changes are:
- Confirm forms-based authentication not selected on the Exchange Client Access server
- Enable Outlook Anywhere on the Exchange Client Access server
- Require secure channel (SSL) communications to the Web site
- To confirm that forms-based authentication is not selected on an Exchange CAS, in the Exchange Management Console, expand Server Configuration, and then click Client Access. Select your Client Access server and then select owa (Default Web Site) on the Outlook Web Access page. In the action pane, click Properties under owa (Default Web Site).
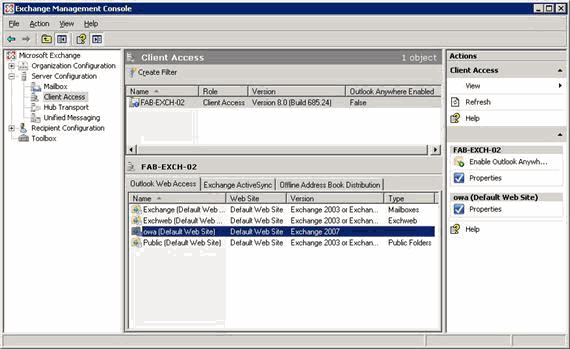
Figure 3
- Select the Authentication page and confirm that the following are selected: Use one or more of the following standard authentication methods and Basic authentication (password is sent in clear text). Click OK.
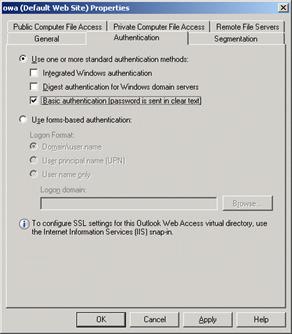
Figure 4
- Review the Microsoft Exchange Warning dialog box and click OK. For the changes that were just made, you must restart Internet Information Services (IIS). To restart IIS, run the following command: “iisreset /noforce”.
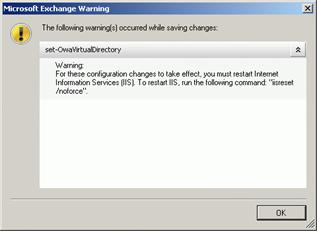
Figure 5
- Repeat steps 1–3 for the following sites: Exchange (Default Web Site), Exchweb (Default Web Site), and Public (Default Web Site).
- To enable Outlook Anywhere on your Client Access server, in the Exchange Management Console, expand Server Configuration, and then click Client Access. Select your Client Access server. In the action pane, click Enable Outlook Anywhere under the server name you just selected. Enter the host name that the client will use to connect to the Client Access server in the External Host name field. This name should match the common name or FQDN used in the server certificate installed on the ISA Server computer. Confirm that the External authentication method is set to NTLM authentication and click Enable.
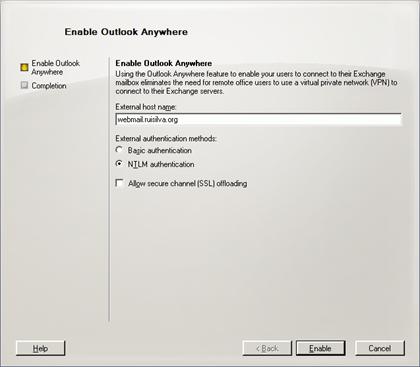
Figure 6
- To require the Web site to only accept secure channel communications, follow step 3 from previous section (Exchange 2003 Front-End Configuration) for all the mentioned virtual directories plus /owa.
ISA Authentication Basics
Before entering the publishing rules section, let’s take a look how ISA Server pre-authenticates client requests.
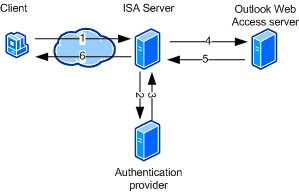
Figure 7
Step 1, receipt of client credentials: The client sends a request to connect to the corporate Outlook Web Access server in the Internal network. The client provides the credentials in HTML form.
Steps 2 and 3, sending credentials: ISA Server sends the credentials to the authentication provider, such as a domain controller for Integrated Windows authentication in Active Directory, or a RADIUS server, and receives acknowledgment from the authentication provider that the user is authenticated.
Step 4, authentication delegation: ISA Server forwards the client’s request to the Outlook Web Access server, and authenticates itself to the Outlook Web Access server using the client’s credentials. The Outlook Web Access server will revalidate those credentials, typically using the same authentication provider. The Web server must be configured to use the authentication scheme that matches the delegation method used by ISA Server.
Step 5, server response: The Outlook Web Access server sends a response to the client, which is intercepted by ISA Server.
Step 6, forwarding the response: ISA Server forwards the response to the client.
Remember that Active Directory validation can only take place when ISA Server is a domain member (either the same domain as the domain controller or in a trusted domain). Since our ISA Server is in a workgroup configuration, we will have to use RADIUS or LDAP.
In order to use RADIUS, you can install the IAS service on any Windows 2003 member server on your internal network.
ISA Server can connect to an LDAP server in any of the ways described in the following table.
|
Connection |
Port |
Requires Active Directory domain name |
Supports Change Password option |
|
LDAP |
389 |
Yes |
No |
|
LDAPS |
636 |
Yes |
Yes |
|
LDAP using global catalog |
3268 |
No |
No |
|
LDAPS using global catalog |
3269 |
No |
No |
To use LDAPS or LDAPS using global catalog, a server certificate must be installed on the LDAP server and the root certificate from the issuing CA needs to be installed on the ISA Server computer.
I prefer LDAP, though, so I will enumerate the required steps to configure this authentication method:
- Open the ISA Firewall console and expand the Arrays node and then expand the array name. Expand the Configuration node and click the General node. In the middle pane, click the Specify RADIUS and LDAP Servers link.
Figure 8
- On the LDAP Servers Sets tab, click Add to open the Add LDAP Server Set dialog box. In LDAP server set name, type the name of the domain.
- Click Add, to add each LDAP server name or IP address. In Server name, specify the DC and click OK. We must also provide user credentials that can be used to access the Active Directory. You do not need to use a domain admin account, a regular user account can be used. Click OK to close the Add LDAP Server Set dialog box.

Figure 9
- Click New to open the New LDAP Server Mapping dialog box. In Login expression, type DOMAIN\*. In LDAP server set, select the domain name previously defined, and click OK.
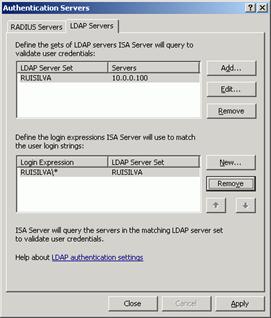
Figure 10
- Click Close to close the Authentication Servers window.
Summary
Now that we have our Exchange CAS/Front-End configured and ISA Server has the required authentication mechanism working, we can move on to the publishing rules. That will be covered in the next and final part of this article.
If you missed the first part in this article series please read Publishing Exchange Client Access with ISA 2006 – The Complete Solution (Part 1).
If you would like to read the next part in this article series please go to Publishing Exchange Client Access with ISA 2006 – The Complete Solution (Part 3)
Related Links

