
Source: Pxhere
The file transfer protocol (FTP) has been around for decades. When an organization had too much data to send via email, it used FTP. But over the years, cybercriminals started exploiting this protocol to conduct cyberattacks and steal information. So what’s the solution to this dilemma? Enter the Secure File Transfer Protocol (SFTP)!
In this article, I’ll explain what SFTP is, how it works, and more. Without further ado, let’s dive right in!
What Is the Secure File Transfer Protocol (SFTP)?
The Secure File Transfer Protocol (SFTP) allows you to securely transfer large files across the internet or your network. Essentially, it remedies some of FTP’s challenges. As the name suggests, SFTP is much more secure and efficient at transferring data. You can also use SFTP to transfer data in a virtual private network (VPN) solution.
SFTP protects you against password and data packet sniffing attacks. It encrypts data and uses a password hash function for user credential verification.
As mentioned earlier, SFTP outclasses FTP in many aspects — SFTP has all of FTP’s aspects, but it’s also easier to configure. That’s why you’re much better off using SFTP over FTP.
So how exactly does SFTP work to transfer your files efficiently and securely? Let’s take a deep dive into how the protocol works next.
How Does SFTP Work?

Source: Wikimedia Commons
SFTP uses the Secure Shell (SSH) protocol to transfer files securely. This means it requires user authentication to work successfully. Using SSH, SFTP encrypts data in transit to ward off prying eyes. It also uses SSH port 22, so you don’t need any other ports.
SFTP was primarily developed to manage files over a TCP/IP network. Much like FTP, you create folders on your server. You can then allow users to access these folders using an address and valid user credentials. To make your life easy, SFTP uses the same commands as FTP. Likewise, most SFTP commands are identical to Linux shell commands.
To connect to a server you’re trying to access, you’ll need an SSH client installed to use SFTP. The following SSH clients are good options for many organizations:
- PuTTY
- WinSCP
- Cyberduck
- FileZilla
- Tectia SSH Client
One more thing to note is that SSH clients come with SSH keys. These keys automate access to servers, and you’d often add them to scripts, backup systems, and configuration management tools. Every key in SFTP has two parts. You typically store the first part on the client machine and the second on the server with a public key. Admins can choose if a user ID and password identify a user, or if an SSH key identifies them. You can even use a combination of both.
So, how does this all fit in with your business? I’ll take you through some common use cases next.
SFTP Use Cases
Depending on the purpose of the SFTP, you can use this protocol for the following:
- Allows clients to upload data that’s too big to attach directly to support tickets or emails
- Creates a location that an onsite implementation team can access remotely to get installation files or other resources
- Transfers billing data, data recovery files, and sensitive client data securely
- Helps you meet regulatory compliance with the Health Insurance Portability and Accountability Act (HIPAA) and General Data Protection Regulation (GDPR)
You can also use SFTP to complement your VPN-encrypted traffic policies. This combination reduces the chances of a cyberattack occurring. As stated earlier, SFTP encrypts your data in transit. The credential system SFTP uses helps stop cyberattackers in their tracks. It ensures that anyone accessing sensitive data has the right credentials. In essence, encryption and user credential verification is a powerful cybersecurity combo!
Now, you’ve seen me mention FTP quite a few times in this article. Before discussing SFTP’s implementation process, let’s quickly look at the differences between FTP and SFTP.
SFTP vs FTP
So why should you use SFTP by default? Well, as you now know, it’s far more secure and more efficient than FTP for data transfer. But here’s a table showcasing all their differences:
| SFTP | FTP | |
| Security | Encrypts data before transmission | Not encrypted |
| Architecture | Operates as a subordinate of SSH | Works in a client-server arrangement |
| Ports | 22 | 21 |
| Transfer Method | Uses encryption tunneling between endpoints to help protect all data and verifies user with credential authentication | Direct transfer between endpoints |
As you can tell, FTP is now obsolete due to its inferior security when transmitting data.
Now that you know why it’s best to use SFTP, you’re probably wondering how to implement it. Let’s have a look at that process next.
How to Implement SFTP
When it comes to implementation, you’ll need to follow a few basic steps. First, you need to set up an SFTP server. Remember that you also need an SSH client. For this example, I’ll use OpenSSH and WinSCP.
Installing the SFTP Server
If you’re using Windows 11, simply follow these steps:
- Go to Settings > Apps > Optional Features
- Click on View features
- Navigate to the OpenSSH server and select it
- Click Next
- Click Install
If you’re using Windows 10 version 1803 or higher, you can follow these steps:
- Go to Settings > Apps > Apps & Features > Optional Features
- Click on Add a Feature
- Navigate to the OpenSSH server feature and expand it
- Click Install
This will install the binaries to %WINDIR%\System32\OpenSSH.
You can also find the sshd_config configuration file and host keys installed to %ProgramData%\ssh, but only after you restart the server.

Source: Flickr
If you want to manually install a newer version of OpenSSH (newer than the one shipped with Windows), simply follow this process:
- Download OpenSSH for Windows and match the system architecture with the version, e.g., 64-bit or 32-bit version
- Extract, as the administrator, the downloaded package to C:\Program Files\OpenSSH
- Install, as the administrator, sshd and ssh-agent services by running the following command from a terminal:
powershell.exe -ExecutionPolicy Bypass -File install-sshd.ps1
You’ve just set up your SFTP server! Now, it’s time to configure it.
Configuring the SFTP Server
Now that you have an SFTP server, you need to allow incoming connections to the SSH server in Windows Firewall. During installation, OpenSSH may have already updated your firewall. Check and see if the firewall rule “OpenSSH SSH Server (sshd)” exists. If it doesn’t, run the following PowerShell command as an administrator:
New-NetFirewallRule -Name sshd -DisplayName’ OpenSSH SSH Server’ -Enabled True -Direction Inbound -Protocol TCP -Action Allow -LocalPort 22 -Program “<sshd.exe location>”
Note that the sshd.exe location above defaults to C:\Windows\System32\OpenSSH\sshd.exe.
Alternatively, you can go to Windows Security > Firewall & network protection > Advanced Settings > Inbound Rules, and add a new rule for port 22.
Regardless, after adding the new rule, follow this process to continue the configuration:
- Start the service
- Open Windows Services in Control Panel > System and Security > Administrative Tools
- Find the OpenSSH SSH Server service
To set the service to automatically start on bootup, follow these steps:
- Go to Action > Properties
- Change the Startup type to Automatic
- Confirm the changes
Now, when you want to start the OpenSSH SSH Server service, you can use the “start the service” link or go to Action > Start in the menu.
Next, I’ll take you through how to set up the SSH public key.
Setting up The SSH Public Key
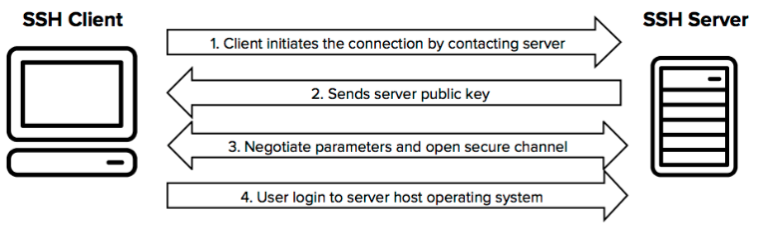
Source: Wikimedia
This process can vary depending on your needs and setup. But the below is a general example:
- Create the .ssh folder, which will host the authorized_keys file in your Windows account profile folder, e.g., C:\Users\username\.ssh
- Add Windows access control level (ACL) permissions
Set the ACL so that the respective Windows account is the folder owner. Also, ensure it’s the only account that has write access. Remember that the account that runs the OpenSSH SSH Server service needs to have read access to the file.
One other thing to note is that the default out-of-the-box Win32-OpenSSH configuration has an exception set in sshd_config for accounts in the Administrators group. This makes your life easier in the long run!
It’s finally time to connect to the server!
Getting Ready to Connect to Your Server
Before your first connection, you need to find out the fingerprint of the server’s host key. You can use ssh-keygen.exe for each file. As an admin, enter the following command in the Windows command prompt:
for %f in (%ProgramData%\ssh\ssh_host_*_key) do @%WINDIR%\System32\OpenSSH\ssh-keygen.exe -l -f “%f”
Note: Replace %WINDIR%\System32 with %ProgramFiles% if appropriate, depending on your OS architecture.
If you’re using PowerShell, simply enter this command:
Get-ChildItem $env:ProgramData\ssh\ssh_host_*_key | ForEach-Object { . $env:WINDIR\System32\OpenSSH\ssh-keygen.exe -l -f $_ }
Replace $env:WINDIR\System32 with $env:ProgramFiles, if needed.
After finding the server host key’s fingerprint, you can start WinSCP. Follow these steps in the dialog:
- Check that you selected the New site node
- Check if you selected the SFTP protocol on the New site node
- Enter the server IP address or host’s name under hostname
- Enter your Windows account name
For a public key authentication:
- Press the Advanced button
- Go to SSH > Authentication
- Select the private key file in the Private Key form input
- Click OK to submit your changes
- Enter your Windows account password (if your Windows account doesn’t have a password, you’ll need to use public key authentication)
- Click the Save button
Finally, click the Login button and check the host key by comparing fingerprints collected beforehand.
You’re now ready to use your SFTP server, but you still need software to manage users and files. Let’s explore this further in the next section.
Installing SFTP Management Software
Out of the many available solutions, I’ll use WinSCP in this example. If you haven’t installed it yet, go to the WinSCP website and find the correct operating system version. Then, download and use the installer to add the software to the server and end-user for a user-friendly interface. This helps you manage users as an administrator as well as manage file transfers. Likewise, your end users will also benefit from this interface.
Once installed, you must restart the machine on which you installed the software. Now that you have management software installed, you can create users and passwords. You must also ensure that each user has access to only one part of the SFTP location. This is useful if you have clients uploading sensitive information that other clients shouldn’t see.
Finally, I’ll now discuss how users can use your SFTP server.
How Users Can Use Your SFTP Server

Source: Flickr
After creating users and passwords, you can now provide your users with the necessary details to allow them to connect. They’ll need the following:
- Server hostname, e.g., ftp.example.com
- Server protocol used, e.g., SFTP
- Account username
- Account password
If they’re off-site, they’ll need a secure VPN connection to gain access to your network first before they can use the SFTP software.
And there you have it. Now you know how to set up an SFTP server and grant users access to it. Remember that each software solution works on the same principles we used in our example here. Earlier, I mentioned VPNs, so before wrapping up, let’s quickly touch on how VPNs can help support SFTP activities in your business.
How Can a VPN Support SFTP?
First, you should never rely on one security measure, and SFTP is no exception. Sure, it encrypts data and requires credential authentication to help provide users access to data, but you can improve your security further with a VPN.
SFTP perfectly pairs up with enterprise VPN solutions that offer unified threat management (UTM) and next-generation firewall (NGFW) protection capabilities. If you do decide to use a VPN, consider getting one that has those two along with the following features:
- Intrusion prevention system (IPS) and intrusion detection system (IDS)
- Gateway anti-virus
- Web and application filtering
Overall, these features ensure data encryption at the highest level across your entire network. Now it’s time to wrap things up!
Final Thoughts
To conclude, you should seriously consider using SFTP over legacy protocols such as FTP or FTPS. The latter options are less secure and inefficient for transferring files. This article included a comprehensive guide on how you can implement SFTP in your organization. Feel free to save this guide as a reference for the future.
Also, if remote workers want to connect to your SFTP server, remember that they need a VPN connection to your network. Moreover, to help secure your network even further, consider using multi-factor authentication (MFA). Until next time, stay safe out there in the world of cybersecurity!
Do you have more questions about SFTP? Check out the FAQ and Resources sections below!
FAQ
How can I make VPN access more secure for remote workers?
You’ll find a wide range of VPN software solutions in the wild, yet some are better than others. Ideally, you need a VPN that integrates with the rest of your security solutions and helps protect you and the remote worker. Use a VPN with a multi-factor authentication tool for the best results.
What are some best practices for using firewalls?
Firewalls, like any other software solution, are only as good as their implementation and adoption. To this end, ensure you follow firewall best practices to get the best out of your firewall. This includes blocking unused ports to help harden your network and updating traffic rules if the hardware gets lost or stolen.
What is a next-generation firewall (NGFW)?
NGFWs ask the user a series of questions to understand the intent of the solution. Once received, the NGFW interprets the solution’s installation and configuration while automatically detecting network hardware. To this end, NGFWs are excellent for large and complex networks where the administrator may miss an attack surface.
What is Software-as-a-Service (SaaS)?
Software-as-a-Service is a term that describes cloud-based software that offers a subscription model. This software helps reduce the barrier to entry for SMBs by offering a tiered pricing structure. Also, providers will often offer a free trial that businesses can use to test the proposed solution. Overall, these solutions can quickly scale to meet your business’s growth.
Do my users need VPN access to a remote site to use my SFTP server?
Yes, if you want someone to access your SFTP remotely, they’ll need to connect to your server using a VPN. Make sure they use a VPN with authentication features to stop cyberattackers in their tracks.
Resources
TechGenix: Article on Email Backup Solutions
Learn how to effectively archive your emails using these corporate email backup solutions.
TechGenix: Article on Network Protocols
Get to grips with the different network protocols and how you can optimize your network with better protocol policies.
TechGenix: Article on Cloud Web Security
Discover how cloud web security works to protect your business.
TechGenix: Article on InfoSec Challenges
Find out how to overcome InfoSec overload challenges.
TechGenix: Article on the Common Internet File System (CIFS) Protocol
Educate yourself on the CIFS protocol and how it helped companies manage internet files in the past.



