A Full, 60-day working version of GFI MailSecurity for Exchange/SMTP can be downloaded here
MSExchange.org Rating:
Implementing network security is like trying to chase a moving target at the best of times. Some companies spend tens of thousands of dollars per year reactively trying to solve problems as they occur. If you had the unfortunate experience of having to react to the Klez worm or the Love Bug virus, you certainly understand what I’m talking about. The days where you could rely on updated desktop virus definitions alone are unfortunately long gone. Securing a network is a constantly evolving challenge. Where most companies today would consider it incomprehensible to not have a properly configured firewall, many of these same companies still overlook the single biggest source of their problems – their email systems.
As the Love Bug virus showed, companies also still rely on their users to exercise good judgment when it comes to dealing with things like potentially malicious attachments. Disabling VBScript on their systems may be a great first step, but what’s your plan for dealing with HTML emails that include embedded ActiveX controls? With 25 critical security updates already released by Microsoft this year, the need for centralized email security has never been clearer. Instead of spending your precious hours trying to fix the security leaks that have already entered your network, secure the source – the free-for-all known as your mail server.
If your company is running Exchange 2000, one product definitely worth a look is GFI Software’s GFI MailSecurity for Exchange/SMTP. Not only does this application provide you with complete control of incoming, outgoing, and internal mail, but it also does so in a manner completely transparent to users. GFI MailSecurity is much more than just virus-checking software. The list below outlines some of the capabilities that we’ll explore further in this article.
· Content and Attachment Checking. GFI MailSecurity provides the ability to scan email messages that include specific words or attachments. Whether you’re looking to ensure that messages containing VBScript attachments are blocked, trying to filter spam, or want to stop certain users from sending or receiving attachments at all, this feature is a must-have.
· Quarantining. Emails that include checked content, attachments, or viruses can be quarantined. Quarantined messages can then be sent to an administrator, a user’s manager, or even a mail-enabled Exchange public folder, prior to being manually approved or rejected. You also have the option of automatically deleting emails that meet the conditions of the rules you’ve specified.
· Virus Scanning. GFI MailSecurity can also scan all incoming, outgoing, and even internal attachments for viruses. Not to be outdone, the program uses two virus-checking engines by default – Norman Virus Control and BitDefender. If two virus engines are still not enough, you have the option of adding the McAfee engine as well.
· Email Exploit Engine. If you think that it’s only email attachments that you need to worry about, think again. Over the course of the last few months, some of the most serious problems to work their way into the enterprise are those associated with active content or scripting, via HTML emails. GFI MailSecurity protects against these types of exploits as well, using their industry-first email exploit engine.
Whether you’re looking to secure your mail server or a way to control what your users can do with their email, GFI MailSecurity has something to offer. You hopefully already have a firewall. It’s time to consider something similar for your mail server.
The installation of GFI MailSecurity for Exchange 2000 requires Windows 2000 Service Pack 1. It also requires Exchange 2000 Service Pack 1 to take advantages of Microsoft’s new Virus Scanning API (VS API). VS API allows messages to be scanned within the Exchange message store, ensuring that scanning occurs before a user’s mail client accesses a potentially malicious attachment. The VS API is also much more efficient in how it deals with attachments – if sent to multiple users, it will only be scanned once prior to delivery, rather than multiple times according to the number of recipients.
The installation of GFI MailSecurity is exceptionally straightforward and not worth exploring in detail. Once installed, GFI MailSecurity is managed using the GFI MailSecurity Configuration tool, which is implemented as an MMC snap-in. The interface of the console is shown below.

Content and Attachment Checking
GFI MailSecurity provides you with the ability to “police” your mail server by controlling both the content of email messages and the associated attachments that are allowed to pass through. For example, it’s generally a good idea to block potentially malicious attachments like .exe, .vbs, and .js files. GFI MailSecurity takes care of all three (and more) in the default attachment-checking rule that we’ll look at shortly.
Content checking rules allow you to control the types of messages that can be sent or received on your mail server according to the words they contain. For example, you might choose to create rules that search messages for profanity, or common spam keywords. Not only is GFI MailSecurity capable of searching for these words in the body of a message and subject line, but also in attachments if so configured. Consider the options shown on the screen below.
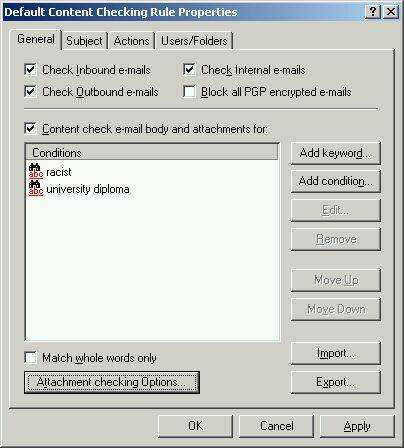
Once a rule has been specified, you need to associate it with an action, and optionally a group of users. Consider the screen shot below, which shows the Action tab for my new rule that checks all messages for the words “racist” or “university diploma”. The top of the page allows me to block the message and perform an action. Possible actions include quarantining the message, deleting the message, or moving it to a folder. Another course of action would be to specify multiple rules, which could then have different actions associated with them, or apply to different users. For example, you might delete messages considered spam immediately.

Notice the option to inform a manager. If you’ve ever looked at the properties of a user account in Active Directory, your may have noticed that you have the ability to configure the manager of a user within the properties of an account. In cases where this option is selected and the rule is matched, GFI MailSecurity will query Active Directory, find the manager associated with a user, and forward the message to the manager, allowing them to approve or reject the message. If approved, the message will be sent. If rejected, the message is deleted. In cases where the Manager attribute is not set in a user’s account, the message will be sent to the configured administrator.
After specifying an action, you can use the Users/Folders tab to control to whom this rule will apply. By default, a rule will apply to all users. For a more granular level of control, you can select the individual users to whom the rule should apply.

Attachment checking rules are something that every company will want to implement. The default attachment checking rule is set to deny commonly malicious attachments, such as those shown in the list below.

Notice that inbound, outbound, and internal emails can be selected as checking options. Select inbound to check attachments that originate from outside of your organization. Outbound attachments are those sent from users found in Active Directory to outside persons. Internal checking is used to check attachments sent to and from users within your organization. Remember that not all malicious code originates from the outside world. Ensuring that your users are not purposely or inadvertently sending potentially harmful attachments to others should also be a primary consideration. The actions associated with attachment rules are similar to those seen earlier with content checking. Users who are to be impacted by the rule can similarly be specified.
GFI MailSecurity is also a great tool for retaking control of your Exchange server. Every company has users who waste significant server resources in sending and receiving personal attachments like jokes, MP3 files, or similar. You can use GFI MailSecurity to block these attachments, for all users or a subset thereof. Trying to circumvent the rule by renaming the extensions of files won’t work either – GFI MailSecurity is capable of detecting files with renamed extensions.
Quarantining
After first installing GFI MailSecurity, consider quarantining messages that have been filtered by the content and attachment checking rules, rather than deleting them outright. Quarantining gives you the opportunity to manually approve or reject messages that have been filtered. To that end, it doesn’t necessarily need to fall on your shoulders alone – messages can be quarantined by sending them to the administrator, a user’s manager, or a mail-enabled public folder. The mail-enabled public folder is a great option, especially if distributing your workload is a priority (as it always should be!). As a test, I configured GFI MailSecurity to block and quarantine all messages with .exe attachments. I then sent an email from my personal account to the Administrator, which included the attachment test.exe. The administrator received the message shown below.

Notice that test.exe is not attached. Instead, the email includes an ErrorReport.txt file, which alerts the recipient to the fact that the attachment is not included, on account of the configured rules.

Within seconds of receiving the original email, a notification email about the quarantined attachment arrives for the administrator’s approval. It provides details about the message, and allows the administrator to approve or reject the attachment. If approved, the attachment will be forwarded to the recipient. Rejecting the message will delete it, allowing you to optionally send notification to the originating sender.

While approving or rejecting individual messages may be reasonable in a small environment, it would be more practical to be able to approve or reject multiple messages simultaneously in a larger environment. Another tool is provided for this purpose – the GFI Moderator Client. This tool allows you to view all quarantined messages, and provides the ability to approve or reject multiple messages at once. The tool also provides a listing of critical messages (any errors that may have occurred) and notification messages (such as those relating to the update of virus definition files).

Virus Checking
When it comes to protecting systems against viruses, there’s no such thing as being too careful. While desktop anti-virus packages are still an important part of a sound security strategy, updates can be troublesome to maintain, especially in larger environments. If IT departments have learned anything over the last two years, it’s that the latest definitions cannot always be relied upon for complete protection. With antivirus software vendors taking anywhere from less than a day to more than a week to update their definitions, the chances of a new virus infecting systems increases, bringing you back to reactive security management. That’s a big part of the reason why attachment and content checking is so important – they offer the possibility of being able to block and remove potentially malicious payloads. For example, blocking all .vbs files ensures that even new VBScript exploit attachments will be blocked from reaching desktop systems.
GFI MailSecurity offers a higher degree of virus checking than any other product that I’ve come across. By default, it ships with two ICSA-certified virus engines – Norman Virus Control and BitDefender. The benefit of multiple engines should be obvious – since different vendors get updates out in varying time periods, chances are good that at least one of the engines will catch a new virus. To that end, the McAfee engine is also available as an add-on feature.

Like content and attachment scanning, inbound, outbound, and internal messages can be configured for virus scanning. Virus-infected emails are automatically quarantined for review by the administrator. Another great feature of GFI MailSecurity is its ability to block Word and Excel documents that contain macros. This feature can be turned on or off for a given virus engine, as shown below.

Managing virus updates is also a simple procedure, since GFI MailSecurity will automatically download new definitions from the GFI FTP automatically once configured to do so. Just to be safe, GFI MailSecurity checks for new updates every 2 hours, allowing you to rest assured that you’ll have updates immediately, once they become available.

HTML Email Exploit Checking
One of the most remarkable features in GFI MailSecurity is its ability to check for exploits hidden within HTML emails. Given that many companies have implemented ways to disable users from running VBScript attachments, virus creators have been getting more creative, embedding malicious scripts and controls within HTML emails instead. Not only does GFI MailSecurity check for a wide range of known exploits, but it will also check for script code in all HTML email messages. When code is found, it is stripped from the message, and the “safe” message is passed to the recipient.

While many products claim to be able to protect your mail servers, I still haven’t seen anything as comprehensive and as easy to use as GFI MailSecurity for Exchange 2000. Think of how much time and money your company spent over the last two years battling various viruses, worms, and malicious content. Then think about how much easier your life would have been if you had software that was automatically quarantining any virus-infected or potentially malicious files before they ever reached your users. With pricing starting at $295, the time and energy saved by GFI MailSecurity will certainly pay for itself many times over, even if it denies only one major virus or worm from affecting your systems over the course of a year.
You can spend your time plugging holes, or you can deal with the problem at the source. Hopefully it won’t take much longer for companies to look at their mail server in the same way that they look at their firewall.
MSExchange.org Rating 5/5

Dan DiNicolo

