Introduction
“Compliance.” It’s a word that strikes fear in the hearts of everyone from the lowly IT pro to the folks in the executive suite. Between all the industry standards, federal and state mandates and regulatory agency rules and regulations, getting and staying in compliance with everything is increasingly becoming an ongoing challenge. Depending on your organization’s line of business, you may be required to comply with PCI standards, FISMA, HIPAA, GLB or SOX statutes, ISO standards and other requirements that you prove your systems and network meet a specified level of security.
It’s not that organizations don’t want their networks to be secure; it’s that the myriad of rules can be confusing and determining how to follow them can be frustrating and expensive. You may find yourself buried in so much information that it’s difficult to make sense of any of it. And you have the specter of fines and other penalties hanging over your head if you fail to comply. Even if you get it right, the laws and rules are changing all the time, so it’s easy to fall behind again.
Even if your particular industry isn’t subject to government mandated rules, you may be taking a proactive approach on your own because you want to ensure that your organization has some protection from the liability that would accompany a serious data breach. In that case, the pressure might come from your own company’s upper management rather than outside, but compliance can be just as difficult to achieve (or even more so, when the requirements are less clearly defined and not as standardized).
Steps toward compliance
The steps required to bring your organization’s IT operations into compliance start with an understanding of what the requirements are, a plan for meeting them, and tools for implementing the process. The implementation process itself must be broken down into steps, as well, beginning with the identification of vulnerabilities (of both the technological and “human factor” varieties).
The starting point for the implementation of your compliance program is to ascertain where your organization stands right now in relation to the standards. That involves establishing baseline controls and doing a thorough risk assessment.
Microsoft Security Compliance Manager
The Microsoft Security Compliance Manager (SCM) is a popular tool designed to help you manage security baselines. SCM is one of Microsoft’s “solution accelerators” – a group of free utilities for enhancing Microsoft products. It installs a number of standard baselines that you can use as-is or you can copy and edit them to fit your own organization’s specific needs. For example, there is a baseline that Microsoft has determined to be appropriate for a corporate laptop. There are also many third party baselines you can use with SCM.
What does it do?
SCM can export the baselines into different formats so you can use them with other tools, such as Desired Configuration Management (DCM) format for use with System Center Configuration Manager. You can import an entire baseline into DCM and assign it to a SCCM collection, then run a compliance report to show how your organization measures up.
You can also export Group Policy Objects (GPOs). You can also make a “golden master.” That’s a reference copy that’s used to produce multiple copies.
You can export settings from computers that aren’t members of the Windows domain by using the Local Policy Tool. This will export only those settings that can be configured with gpedit.msc (the local Group Policy editor).
The baseline settings are divided into three categories: critical, important and optional. You obviously should give highest priority to applying those settings that are identified as critical.
What’s new in this version
The first version of SCM simply gave you a way to export your customized baselines to make it easier for you to apply the right security settings in a standardized way – an important aspect of meeting compliance requirements. Version 2 added the capability of importing your existing configuration into SCM. Further, it gave you the option to point SCM to a local instance of SQL Server or SQL Server Express instead of having to install a separate instance of SQL for its use (although you might still run into errors if you try to install SCM on the same instance of SQL that’s being used by another application). V2 also provided for a more user-friendly experience.
For all you command line fans, SCM v.2.5 added support for looking for specific configuration settings using PowerShell. It also provided new baselines for Exchange 2007 SP3 and Exchange 2010 SP2, as well as Windows 7 SP1, Vista SP2, XP SP3, Office 2010 SP 1 and Internet Explorer 8. The “golden master” option was also a new feature in this version.
Installing and using SCM
You can install SCM on Windows Vista or Windows 7 workstations or Windows Server 2008 and above servers. Microsoft just recently released version 2.5.40.0, which you can download as an executable from the Microsoft web site.
When you run the executable, Setup will check for prerequisites and install Visual C++ runtime libraries if not already installed. One wizard guides you through the process of installing both SQL Server Express Edition (if it’s not already installed) and SCM, as shown in Figure 1. By default, it installs in the C:\Program Files\Microsoft Security Compliance Manager folder. You can, of course, change the location.
Figure 1
All of this can take a while, depending on the performance of the system. You may also need to reboot to complete the installation of SQL Server SE. After SQL Server SE is installed, the SCM installation will automatically begin. Note that after you have started the installation process, there is no option to cancel the wizard.
After the installation successfully completes, you can access the SCM console by clicking Start | All Programs | Microsoft Security Compliance Manager | Security Compliance Manager. First, you’ll encounter the Welcome screen in the middle pane, which tells you what’s new in this version, how to perform common tasks and where to find things. The “Getting Started” section has links to resources to help you use SCM.
When you open SCM for the first time, it will download the baseline files. In the left pane you’ll see the Baseline Library, which shows you the baselines that are available, arranged in a hierarchical list for each product (such as Office 2007, Office 2010, Windows 7, Windows Server 2003, Windows Server 2008 and so forth). The right pane contains links to import GPO back (folder) and SCM (cab). This is also where you’ll find the Help resources. The SCM console is shown in Figure 2.

Figure 2
After you click on one of the baselines, the middle pane will then display information about the baseline you selected. The right pane will display the different actions that you can perform, which vary depending on your selection, as shown in Figure 3.

Figure 3
The Settings window arranges sections so that you can expand or deflate each section just by clicking the horizontal bar, and you can choose the Advanced View to navigate through the hierarchical list in a way that’s similar to the way you move around in Windows Explorer. It employs the same sort of “breadcrumbs” feature whereby you can click on any level in the hierarchy and go immediately to that level. The documentation is extremely useful. For each setting, the description explains to you, in depth, what the particular setting is used for and the scenarios in which it’s appropriate to use it. This information is in the Setting Details pane, which in some cases even gives you the content for a PowerShell script to make the configuration change, as you can see in Figure 4.
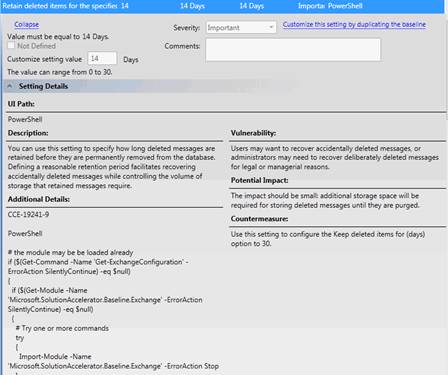
Figure 4
SCM includes a detailed security guide for each product, in Word (.docx) format, that serves as a handy reference with step-by-step procedures, tools and recommendations for strengthening security for that particular OS or application, as shown in Figure 5.
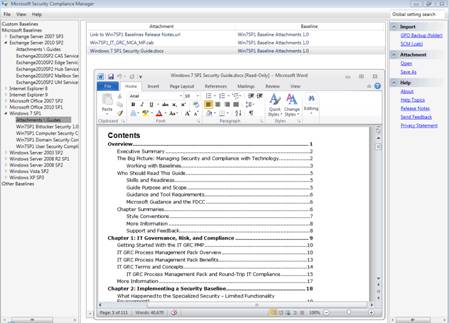
Figure 5
To customize a setting, you create a duplicate of the baseline, which you can then edit. The copy will appear in the left pane, at the top of the tree under “Custom Baselines,” as shown in Figure 6.
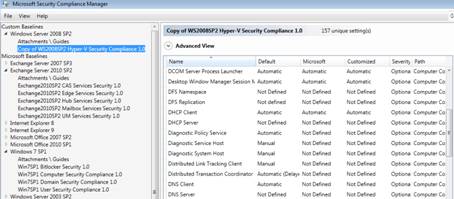
Figure 6
To export a setting to DCM, you create a .cab file by selecting the setting you want to export, then selecting SCCM DCM 2007 (.cab) in the right Action pane, as shown in Figure 7.
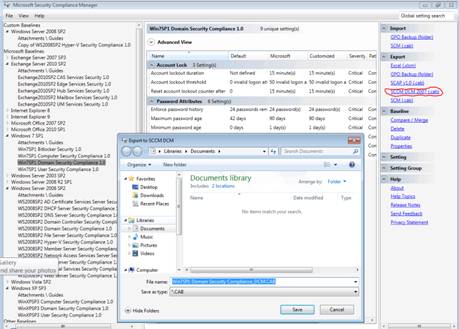
Figure 7
Then copy it to your SCCM server and right click it, and select to “import configuration data” to the appropriate DCM node. The Import Configuration Data Wizard will guide you through that process.
Note that you can also export settings to Excel (.xlsm), create a GPO backup folder, or export to a SCAP (Security Content Automation Protocol) or a SCM file (both .cab files).
There is also a Compare and Merge feature that you can use to see the differences between two baselines, as shown in Figure 8.
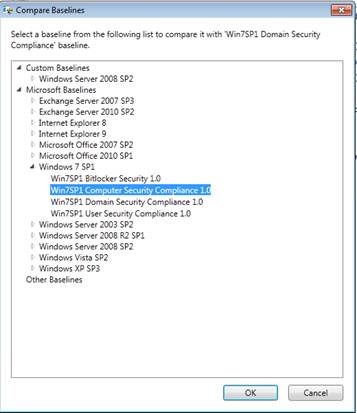
Figure 8
Summary
The Security Compliance Manager tool from Microsoft is a useful utility, especially when used in conjunction with other management tools such as System Center. It brings you Microsoft’s best security practices, based on millions of systems world-wide, into an organized package. This article provided an overview of what SCM v. 2.5.40 does and how it does it, but to get a true understanding of its value, you need to explore all the settings and read through the Guides that are included.




Has anyone ever come across the following error:
“The Microsoft Security Compliance Manager setup wizard failed while installing SQL Server Express Edition Unknown Error 0x375de77d”