A lot of businesses operate online, so it has become essential to include cybersecurity tools and threat-detection software in the organization’s IT infrastructure stack to protect it from unauthorized access. Several cyberattackers now use highly sophisticated methods to ambush users online, always attempting to intrude vulnerable systems. To detect and prevent such incidents, organizations can rely on security information and event management (SIEM) tools as an additional layer over traditional security software like antiviruses and firewalls. SIEM gathers the log data generated by a range of sources like host systems and security devices like firewalls and antivirus, converts it into a standard format, and aggregates it to analyze security alerts across the network. In several organizations, SIEM tools have become a core part of the organization to help identify, detect, and address internal and external cyberattacks. Below are seven top SIEM tools to put in your toolbox in 2020.
SolarWinds

SolarWinds is an SIEM software that comprises of a wide range of log and event management capabilities. Its log management tool has affordable and efficient threat detection capabilities, and its automated incident analysis and response system help IT professionals identify and respond to cyberthreats proactively. This SIEM tool is considered to be a solution with simple pricing and delivers several features like identifying cyber threats early and delivering an automated response to them, log collection and retention, advanced search and forensic analysis, real-time in-memory event correlation, file integrity monitoring, USB device monitoring, and log forwarding and exporting.
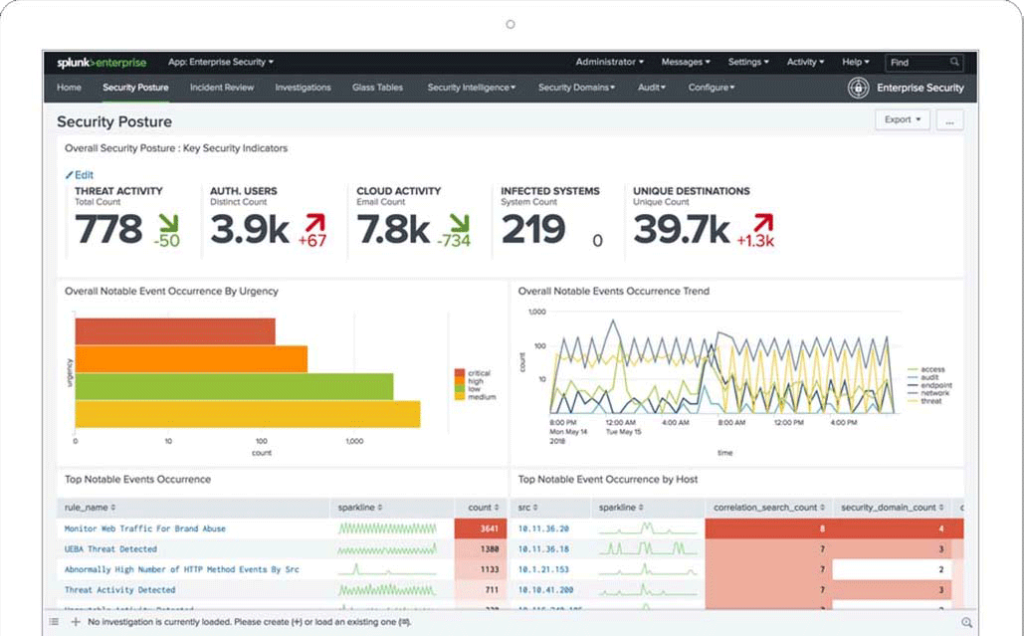
Splunk enterprise SIEM tools
Splunk is best known for its security operations such as customizable dashboards, asset investigation, statistical analysis, incident review, classification, and investigation. Its cutting-edge capabilities such as alerts management, risk scores, data analysis, automated incident response, centralized logs, predefined reports, and correlations help organizations to minimize risk by simplifying threat management and detecting and responding to internal and external cyberthreats in near real-time. By leveraging the power of AI and machine learning for predictive and proactive business decisions, Splunk SIEM solution also converts logs into metrics and boosts search and monitoring performance as well as helps in improving alerting functions. The built-in asset investigator instantly flags any malicious activities and prevents future damage across the network.
LogRhythm Security Intelligence Platform
LogRhythm NextGen SIEM platform is considered to be a pioneer among the available SIEM systems, which allows businesses to streamline operations by empowering teams. It helps to overcome resource constraints and quickly implement a capable and formidable security operations that leverages rapid monitoring, detection, and response. The problems like fragmented workflows, alarm fatigue, segmented threat detection, lack of automation, lack of metrics for understanding maturity, and lack of centralized visibility can be taken care of using LogRhythm. The platform provides a single, unified architecture that combines patented machine-based analytics, user and entity behavior analytics (UEBA), network detection and response (NDR), and security orchestration, automation, and response (SOAR) — all delivered from the cloud or as an on-premises solution. With the help of LogRhythm organizations can quickly identify threats, rapidly search through the log and other machine data, automate and collaborate on investigations, and take immediate action to remediate threats with agility.
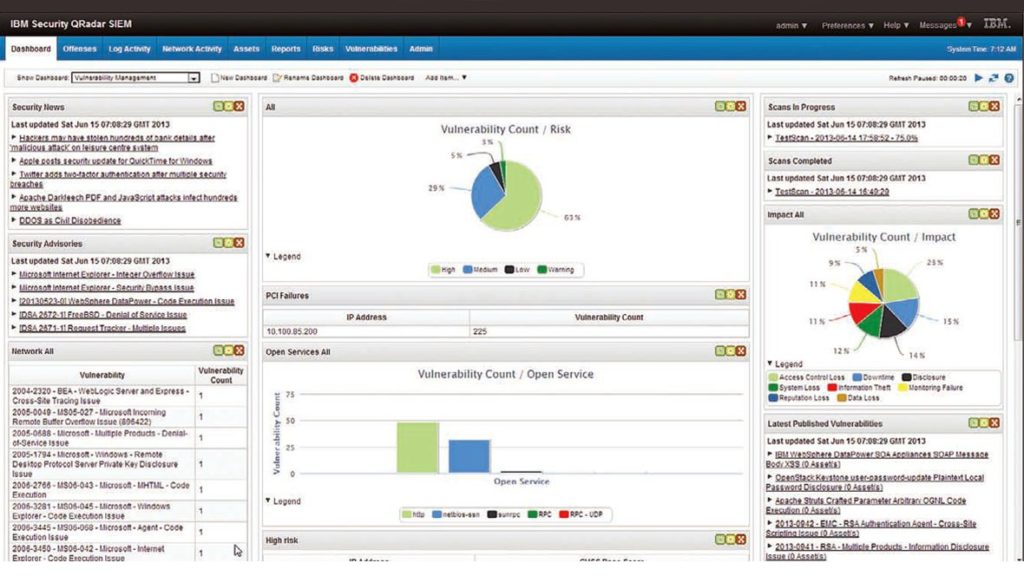
IBM Security QRadar
IBM QRadar SIEM is an intelligent solution that continuously monitors the organization’s network in order to proactively detect phishing, insider threats, data exfiltration, and malware through machine learning and AI algorithms. It is a reliable SIEM tool that is useful for businesses looking to integrate a wide range of logs across their critical systems. QRadar is considered to be the most versatile SIEM solution that offers risk management analytics to simulate potential cyberthreats. The platform offers a wide range of features like log management, analytics, data collection, and intrusion detection that are helpful in continuous monitoring of a variety of physical and virtual environments on the network. QRadar’s extensibility is what makes it appealing and powerful among other SIEM tools. Several other external modules can be integrated with QRadar for data ingestion, vulnerability management, and risk control.
Securonix
A scalable platform based on Hadoop, Securonix Next-Gen SIEM tool combines extensive capabilities like log management, UEBA, and security incident response into a complete, end-to-end security operations platform. It is a software-as-a-service (SaaS) solution and has the capability of collecting large amounts of data in real-time, using the combination of AI and machine learning algorithms to detect potential cyberthreats, and providing AI-based security incident response for fast remediation. It utilizes multiple algorithms at a time, working in harmony to identify and detect potential attacks launched from within or outside the organization. Securonix’s offerings include “response bot,” an artificial intelligence-based recommendation engine that suggests remediation actions based on the previous behavior patterns of Tier 3 analysts. Securonix Spotter and Securonix Investigation Workbench are the two important tools that enable threat hunting using natural language searches and allow the organizations to investigate incidents by tracing associated activities and events respectively rapidly.
RSA NetWitness
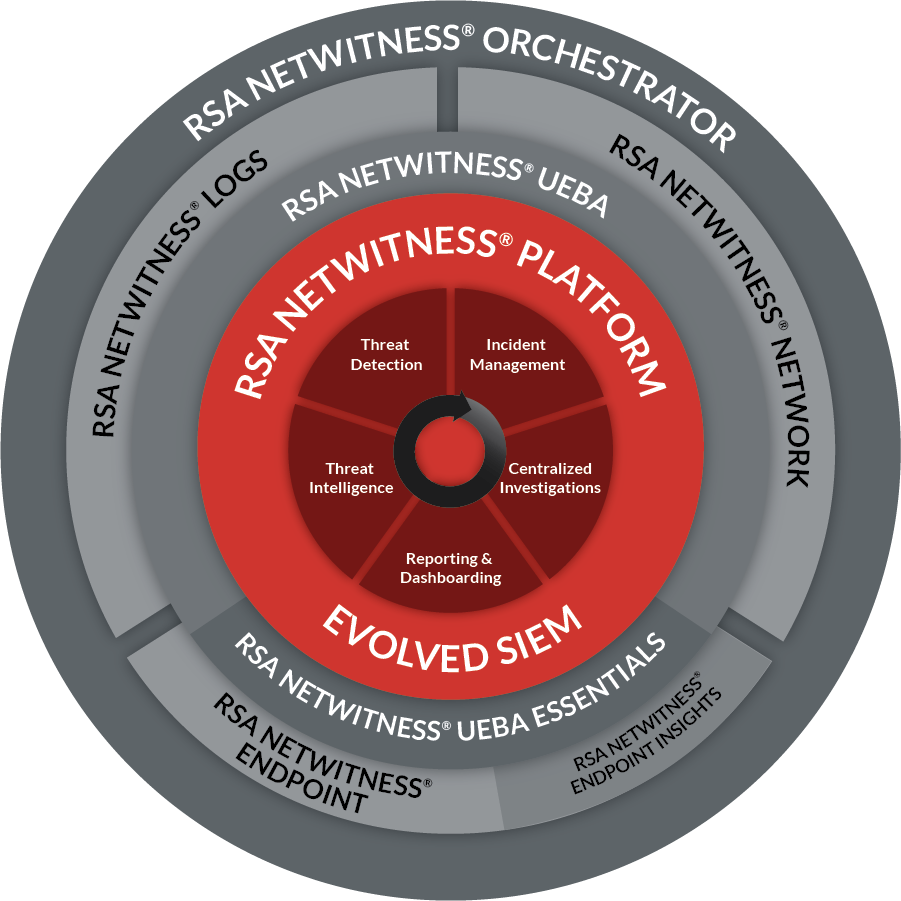
RSA NetWitness is a robust SIEM solution, which is a combination of various data sources such as RSA NetWitness Logs, RSA NetWitness Network, RSA NetWitness Endpoint, RSA NetWitness UEBA, and Orchestrator. RSA NetWitness logs and RSA NetWitness Network capture real-time data from logs and network packets and provide security visibility across the infrastructure. RSA NetWitness Endpoint helps block and quarantine malicious processes or potential cyberthreats, flagging anomalous activity, and providing deeper insights into IT endpoints at the user and kernel level. RSA NetWitness Orchestrator connects with incidents over time, identifies the scope of a cyberattack, and helps analysts to take action against cyberthreats before they impact the network.
McAfee Enterprise Security Manager
To prioritize, investigate, and respond to hidden threats while meeting compliance requirements, McAfee Enterprise Security Manager (ESM) can be considered as the best SIEM platforms in terms of analytics. It provides a complete suite of products related to security like McAfee Investigator, Advanced Correlation Engine (ACE), Application Data Monitor (ADM), Enterprise Log Manager (ELM), Event Receiver (ERC), Global Threat Intelligence (GTI) for Enterprise Security Manager, and Enterprise Log Search (ELS). McAfee’s SIEM solution can provide a real-time understanding of threat data as well as the view of the systems, data, threats, and activities inside the company’s network. As the foundation of the SIEM resolution, McAfee ESM delivers intelligence and integrations needed for the organizations to range, investigate, and answer threats, whereas the embedded compliance framework and inbuilt security content packs modify analyst and compliance operations. McAfee Enterprise Security Manager makes it possible and easy to support your organization’s current and future security and compliance goals.
SIEM tools: Why you need them
Providers of SIEM tools offer a huge package of robust solutions that are ready-to-use and feature-rich. These systems allow you to centralize and streamline the security operations across the organization using real-time monitoring and log analysis functions. Implementing a SIEM system step by step can assist you in checking whether or not you’re exposed to malicious attacks. Doing this helps you to secure the IT infrastructure of your organization and to fine-tune the adoption process. By comparing the features provided by each of these vendors, you can select the optimal option that best fits your organization’s objectives and proceed toward the adoption of the relevant SIEM tools gradually.
Featured image: Shutterstock



