
The types of malware in existence are vast. The term itself is a catch-all for any malicious software. According to DataProt, 560,000 forms of new malware get discovered in the wild each day. These rates are also growing annually. Some malware can be crude, while others can be elegant in their implementation. Attackers sometimes use malware to play a light-hearted practical joke or extort money from a company; the use-cases are endless. The malware issue is so rife that every business is likely to be the target of a malware attack within the next 10 years.
Anyone interested in security will need to understand the attack vectors and functionality of common malware they may face. To this end, I’ll show you common types of malware and what you can do to defend against them. First, let’s look at what malware is.
What Is Malware?
As mentioned before, malware is the catch-all term for malicious software used by cybercriminals to accomplish a nefarious goal. The term can refer to computer viruses, worms, trojans, bots, and more.
Firewalls are a good solution for defending against malware. Most firewalls work on a malware list that gets periodically updated with new malware sightings. You can then report this malware to agencies such as the FBI, CISA, or the Secret Service in the US.
In some industries, it’s mandatory to report malware unless you have a low probability of data getting accessed during the attack. This is to reduce the impact on multiple organizations or critical industries needed to keep the country functioning.
In the next section, I’ll go over the main types of malware and how they work. Let’s begin.
Types of Malware
Cybercriminals combine and recycle malware to produce thousands of different threats each day. In essence, to understand malware, you only need to know how a handful of them work. Below I’ll discuss 12 of the most common types of malware you’ll likely encounter:
1. Viruses
Viruses ‘infect’ computer systems and infrastructure. Like its namesake, they pass to other devices they come in contact with through replication. Transmittance can be digital. You can get a virus by downloading a file from a nefarious website. You can also get them through malicious email attachments. Alternatively, viruses can get passed on physically. For instance, a cybercriminal can leave an unlabeled USB in or near a targeted company. In turn, an unsuspecting employee might end up plugging it into their computer to find out who this USB belongs to.
Overall, viruses cause disruption to a system, either by using resources or damaging data. This data could be the company’s intellectual property. It could also be data used to support a system’s kernel operations. Modifying a kernel can cause the operating system to fail to work. The modification can also provide cybercriminals with a ‘backdoor’ and full control of the system.
Most firewalls effectively spot viruses, quarantine them, and remove them from your system. To help improve your security, you should train users on several best practices. For example, employees shouldn’t click on suspicious email attachments. They also shouldn’t plug in unknown devices to the network or their computer.
2. Worms
Worms are similar to viruses. One key difference is that they cause their damage through repeated replication. Eventually, this eats up a system’s resources. Once all the resources get allocated, the system fails. While viruses replicate to propagate the virus to new systems, worms replicate to take a system offline. Some worms are even carried by viruses to new systems. Some others also have their own virus-like propagation method. In essence, you can consider a worm as a type of virus.
Most firewalls will recognize worms and prevent them from running. Much like before, consider training users in the best IT security practices to avoid any damage.
3. Trojans
A trojan is a type of malware that obfuscates itself to gain access to a system. The idea here is that the carrier is a trusted file or software. Administrators will run this file, expecting it to be virus-free. A good example is some freeware that you can find online that performs a utility such as recompiling a file into a different format. The software itself could contain a trojan that works once the software gets installed. It could also be an online compiler that adds the trojan to the file.
Most trojans force the administrator to allow the software to run. Because this software gets considered legitimate, some do allow it to run. This is where most problems with trojans arise. A firewall will only work if it’s on and not forced to accept software as being legitimate by the administrator. To hide trojans better, many of them were designed to compile on the target system from building blocks hidden in the file they reside in. Sometimes, multiple files get used to help speed up this process, including spreading parts over different folders.
Effective trojans are complex to write. However, once found, they become useless. Firewalls find ways of protecting your system against them. Many cybercriminals also develop and save trojans for one large crime to maximize their profitability.
4. Ransomware
Ransomware is a form of malware that attempts to extort money from a target. Most work by encrypting computer files or systems needed for the running of a company. Even if you do pay the ransom, it’s no guarantee that the cybercriminal will provide you access to your files.
Cybercriminals use cryptocurrency as a payment method. That’s because it generally hides the recipient. Most criminals choose to ask for bitcoins which, ironically, are pseudo-trackable. This means that you can find out exactly who owns the wallet address. Then, you’ll find the criminal easily. However, even if you find the perpetrator, you may not have the jurisdiction to take action.
Ransomware is a serious threat. These attacks can cause severe collateral and financial damage. Ransomware can also be contagious with many complex examples including ones that propagate supply chains using vendors as the entry point. In this case, cybercriminals need to be patient and hope their ransomware software isn’t spotted. After some time, the criminals initiate the attack across multiple companies. You can expect this process to increase over time and target operational technology (OT). This is because OT has significant and underlying security flaws. Cybercriminals use these highly integrated environments and unsecure operational code levels to propagate malware. Most highly automated engineering plants and power plants are easy high-profile targets.
In highly automated and OT environments, it’s almost impossible to protect systems where air-gapping gets removed from plant equipment, IT systems, and IoT systems. Your best option is to incorporate operational risk assessment software. This type of software simulates production environment risks in real-time as workflows change through use. This software also helps to find patches for known issues.
5. Bots and Botnets
Bots are automated processes often found in internet searches. You can use a bot to ‘web-scrape’ websites. Then, you’ll gain meta-data and useful information from user posts. Bots can also work in bot networks called botnets to do this many times over. Web-scraping is generally disliked, but not illegal in most circumstances. Because bots query sites, they use resources provided for real users. As a result, administrators dislike bots. Websites can also use bots to web-scrape online game sellers to produce a rank of the most bought game, for instance.
On the more sinister side of things, cybercriminals use bots and botnets as a form of online stalking. They could find out what targets are buying online or what websites they’ve visited. They’re also used in some forms of adware and spyware for better data analytics.
Cybercriminals can also use bots and botnets to take down a website by repeatedly attacking it with queries. In most cases, when attacked, an IP address gets barred from making a query for a few seconds. This allows the server to keep working on real requests. Botnets can make this very difficult. First, the attackers will pack a bot into a piece of software and get it installed onto unsuspecting computers. Once enough have gotten installed, the bots get activated and a calculated attack gets carried out. Due to their numbers, a server can’t distinguish each bot as a threat. If enough queries pop up, the server can go offline.
Bots and botnets are complex to program and use. After detection, most of them get rejigged to fit a new exploit; a form of a cybercrime recycling program. Once detected, they become useless as firewalls update their policies to recognize queries irrespective of the IP address.
6. Adware
Adware is essentially malware that’s inadvertently downloaded and installed as part of the browser. It can also add adverts such as pop-ups and banners to web pages for a specific product or offering. They’re not designed to destroy a computer. But they do make browsing the internet tedious.
Adware needs the user’s permission to install on a browser. Usually, most administrators will stop this type of installation. Firewalls will also screen downloads to help avoid installation.
Normally, you don’t really see adware these days. That’s because firewalls can detect the majority of them by scanning browser downloads. Avoid adware by keeping the firewall maintained with the latest updates. You should also customize browser permissions to stop adware from being inadvertently installed.
7. Spyware
Like adware, spyware is browser-centric malware. Yet, instead of adding ads to your browser, it sends cybercriminals valuable information. This can be personal information, credit card details, and login details.
Non-browser-centric spyware includes software that’s often ‘injected’ into a computer’s flash memory. In turn, this will stop it from getting detected by antivirus software. This is also how many ‘click-the-link’ email attachment attacks work.
Of the two, injection attacks are nearly impossible for antivirus software to scan and detect. That’s because they’re already running. Once the computer gets turned off, the virus isn’t stored and needs to get sent again. Alternatively, the cybercriminal needs to have a way to provide access to the system the next time the system turns on.
Besides sending your valuable data to cybercriminals, spyware can also help them establish a remote connection. In turn, attackers will use this to their advantage. They’ll send themselves periodic screenshots or camera shots from your computer.
8. Rootkits
A rootkit is a piece of software that normally installs itself in a vital part of the computer system. This means that it integrates and modifies your operating system’s kernel. A rootkit gives cybercriminals complete control over your computer. This also enables them to use it or capture data remotely. They’ll usually add a ‘backdoor’ to provide easy access in the future. Because rootkits modify the operating system, they essentially become a part of your system. In turn, they’re almost impossible to find and remove. If you think you have a rootkit on your system, your only option may be a clean install. Alternatively, and with regards to more virulent rootkits that hide in hardware components and firmware, your only option is to destroy the hardware and hope nothing else got contaminated.
The National Security Agency (NSA) usually publishes its outdated hacking software, including rootkits. It also provides notes on what they are to help companies protect their assets. Traditionally, organizations like the NSA would use rootkits to spy on potential criminals and parties of interest. This is because they received a ‘backdoor’ and full monitoring potential to the owner’s system.
9. Fileless Malware
Fileless malware attacks are viruses not stored permanently on a system. Antiviruses can only detect malware if it’s stored on the system. Flash memory is in flux when powered on. This means it’s impossible to scan it and make any sense of the results from one instance to another. Fileless malware attacks are also called ‘injection attacks’. They can happen by getting users to click on an email link or plug in a USB. Most fileless attacks these days are made up of injection attacks which work by reading data that looks normal. Then, this data gets compiled and runs on the flash memory.
Some Wi-Fi attacks also work similarly. They push malware straight to the flash memory before execution.
10. Malvertising
Malvertising has only been around for a few years now. It works by injecting code into flash memory that displays adverts. You’ll need good antivirus software to remove it, with an ad-blocker. In addition, ensure users can’t install plugins in their browser without your approval.
Most code redirects users to websites for products that they don’t want. Train your users to check the URL of sites they continually navigate to. You could also teach them to avoid visiting unknown sites. As a best practice, most users using internet resources should only be using established and reputable sites.
11. Keyloggers
Keyloggers are normally independent scripts that need a delivery mechanism. Generally, they log a user’s keystrokes and send these to a cybercriminal. One classic example is the ‘rubber ducky’ attack. This involves a USB, or rubber ducky, being plugged into a target computer. After this, the USB is keylogger-injected into the machine’s flash memory. In this example, the attacker needs to distract the user while the computer is unlocked. Then, they’ll add the script or ‘payload’ to the memory. Once injected, the USB can be removed. Attackers obfuscate the attack by hiding the command windows needed to run the script. PHP or similar is usually used to route logged data to an attacker’s server.
The firewall doesn’t scan the payload. As a result, this attack can steal information from the user and business. To protect against it, train your users to lock their computers when they’re away from their desks. Furthermore, tackle the problem of using social engineering to gain access to a system. You can also try turning off unsecured USB ports on machines that could get accessed by non-authorized personnel.
12. Cryptomining Malware
Cryptomining is currently a trend where people intentionally or unintentionally install crypto mining software. For example, some employees might try installing this software on unused hardware to generate passive income from cryptocurrency. Effectively, they’re stealing resources and energy in the process. Cryptomining software could look like it’s legitimately generating crypto assets for the user. However, it could be generating assets for a cybercriminal without the user’s knowledge.
This type of malware runs as a genuine piece of software. It also mines a user’s personal details to disrupt a user’s machine. Teach all users not to install crypto mining malware. If you find it on a machine, it’ll likely need to run a clean install of the machine’s image. As crypto mining is CPU or GPU-intensive, bad actors will try to install it on servers with multiple processors. This will help them generate more money. As a result, you should regularly check your servers for CPU or GPU performance irregularities.
And those are some types of malware that you should be wary of. Now, let’s take a look at how you can protect yourself from different types of malware.
How to Protect Yourself from Malware
Different types of malware will require different techniques to remove. To save yourself time, you’ll want to ensure all machines have a firewall and antivirus solution. Look for solutions that also include ad-blocker, anti-malware, and anti-spyware features. You’ll also want to compare malware lists between solutions to see what catches more malware on scans. The bigger the list, the better. That said, here are some things to consider when defending against malware.
Implement an Anti-malware Solution
When choosing an anti-malware solution, make sure it can check or sniff individual packets as part of the firewall. Most firewalls are also rolling out this feature to help find malware.
You’ll also want to check that the solution has automated updates. Additionally, consider the frequency that these get rolled out to the software. Ideally, your firewall and antivirus should be part of an integrated solution. This will help you implement and maintain it effectively.
Train Users and Implement Robust Security Policies
Train your users to understand what malware is. You should also teach them about other cyber threats. Additionally, make this a routine training exercise. Periodically test these users by sending them suspicious emails and noting down if they flag it with you.
Test Your Security
If your organization is large enough, bring in penetration specialists or use your own to see if they can gain access to your network. They can tell you which attack surfaces need further attention. Do this regularly as your business grows, adding or removing attack surfaces.
Add Extra Layers of Security and Permissions
Using multi-factor authentication (MFA) is crucial. You should also be applying it to every application you use. This can help stop many attacks, as malware won’t have a way around it in most circumstances apart from some injection attacks.
Ensure you also implement a spam filter. This will help reduce the risk of users clicking on nefarious email links.
Finally, customize your operating system policies and browser policies on both client and server-side infrastructure. Customize permissions and access rights so users can conduct ~80% of their work comfortably. If they require administration to provide temporary escalation to conduct non-routine tasks, you can adjust the permissions. Overall, this helps reduce your need to fix problems later and ensure management that their system is both secure and working effectively. As an administrator, you’ll also reduce your liability if ever questioned after an attack.
Now that you know the basics of keeping your system safe, let’s take a look at solutions that can help you.
Best Solutions to Fight Off Malware
Protecting your system from malware can be challenging if you’re using only one solution. Consider making a list of features you’ll need before choosing an appropriate solution. Below are the top 3 anti-malware tools that you can use to help secure your business against different types of malware.
1. GFI MailEssentials
All administrators worth their salt would have already added a firewall and antivirus solution to their network. You’d also have considered corporate policy, implemented periodic training of users, and customized permissions and privileges to meet policy requirements.
One thing that many people miss is protecting users from nefarious emails before they receive them. This is where GFI MailEssentials comes into play. It’s used worldwide to help filter out many different types of malware. This is something you should strongly consider using to protect your users from themselves and not rely on standard email tools. It has 14 anti-spam filters, uses 4 antivirus engines, and actively scans for malware. By using Avira, Bitdefender, Sophos, and Cyren in the GFI MailEssentials email solution, it’s unlikely that anyone will miss a reported virus during checks!
GFI MailEssentials also allows you to block the senders’ IP addresses. This ensures no users ever receive messages from them again. You can also block email users or nefarious domains.
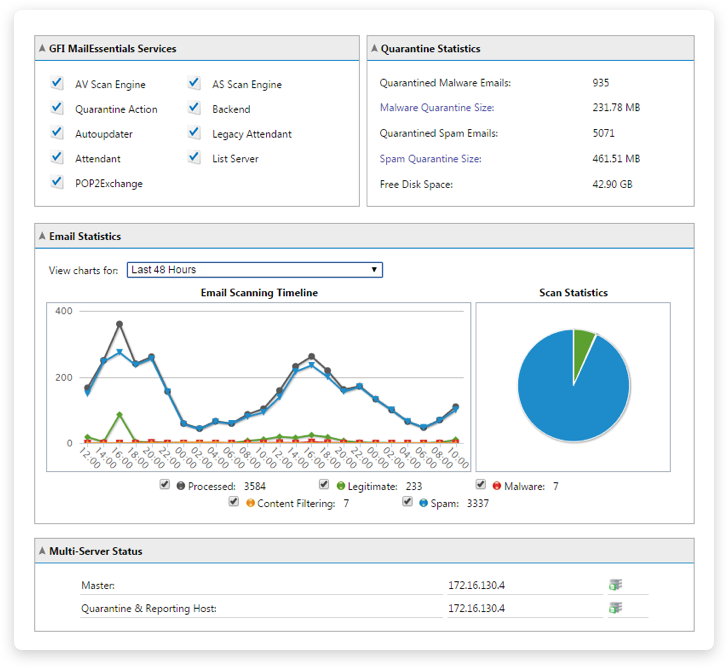
Administrators also get a real-time data analytics dashboard. This way, they’ll see exactly how successful the solution is. The dashboard also shows if you’ve just experienced an email-based malware attack!
2. Malwarebytes

Malwarebytes has been around since 2006 and comes in both a free and paid offering. It’s a great tool for finding malware on a computer that other antiviruses sometimes miss. However, it does have one drawback. Unlike other products that give a complete solution, Malwarebytes has never grown from a specialist offering to a total solution. This means that if you want to use its features, you also have to fork out for an antivirus and firewall solution. This can be very financially painful for companies, and they’ll only consider it when they know they’re having issues.
Malwarebytes’ free offering is only really useful for scanning for viruses. On the other hand, the paid offerings come in many different forms. This helps you implement them without excessively paying. One offering even scans your VPN connection for malware. Otherwise, its features are fairly similar across offerings.
As an administrator, if you can’t afford Malwarebytes, have a copy of the free version. Then, use it to find issues and report them. That’ll persuade management to go for the paid offerings. Obviously, this isn’t a good situation, but some administrators do find themselves going through this process.
3. BitDefender

BitDefender is a popular antivirus solution that helps protect you against a range of malware in a home and business environment. Many businesses use it as it has a measured detection and response system. This also stops users from getting burdened by malware prevention and removal activities. Traditionally, total solutions would become an unacceptable overhead. They’d burn through resources to a point where users would notice. BitDefender is a lightweight solution that runs in the background. But it’s still powerful enough to protect diverse working conditions, including cloud-hybrid workflows.
Enterprises buy this solution as it gives them a complete package. It also provides an enterprise-level of support to customers. This is important to clients who need to remain operational to reduce losses from malware. One of its drawbacks is that it still doesn’t adequately protect users against spam emails, unlike GFI MailEssentials. It also doesn’t discover as many malware threats as Malwarebytes.
Thus, those are a couple of solutions that you should consider when looking for an anti-malware solution. Let’s recap.
Final Thoughts
You have millions of types of malware working on different variations of the types we’ve discussed in this article. To protect against them 100% is impossible, but you can take measures to reduce their ingress. In most cases, after adding in security measures, users are typically the root cause for most successful malware attacks. Using the software discussed above will help reduce a user’s exposure to malware. You’d also limit the option to install or inject malware into their system. To help protect against different types of malware, use a patchwork of training, antivirus and firewall software. Then, test if your policies are robust through regular pen testing. I hope this article helped you prepare for any malware attack.
Do you have more questions on the different types of malware? Check out the FAQ and Resources sections below!
FAQ
How can keylogging affect my business?
Keyloggers are one of the types of malware that logs a user’s keystrokes and sends the log to a cybercriminal’s server. They’re used to steal user credentials, personal information, and intellectual property. Attackers also use keyloggers to steal information and money from a company and need to be removed by anti-malware software.
What is malware?
Malware is any software created with malicious intent. Viruses and ransomware are also types of malware. Malware is often created from combinations of software to create a payload that can run on a target machine. Attack vectors can be digital, such as using emails to add the payload. They can also be physical, such as using a USB to host the malware.
How can I protect my users from nefarious emails?
Emails by themselves are harmless. However, sometimes, they contain links or files from a cybercriminal. In those cases, they deliver malware into the target computer’s flash memory. Use an antivirus or anti-malware software to scan emails before users get them. Train users not to ‘click-the-link’ and why they shouldn’t to help them remember this practice.
Who’s responsible for malware security in an organization?
Everyone is responsible for protecting an organization against different types of malware. In some sectors, you’re legally obligated to report malware to protect other businesses. You’re also responsible for protecting your business, your supply chain, and your clients. Make sure you have robust security policies and regularly pen test your systems, including physical security and personnel behavior.
How does malware in email attachments work?
When a user clicks an attachment containing malware, it downloads a malware payload directly into the computer’s flash memory. As such, it’s difficult for anti-malware software to scan for it due to how flash memory works. The malware remains active until the power gets cut to the flash memory.
Resources
TechGenix: Article on Mobile-Based Malware Attacks
Learn about the latest mobile-based malware attacks.
TechGenix: Article on Discord’s Malware Issues
Discover how Discord is becoming targeted by malware.
TechGenix: Article on the Latest Supply Chain Attack
Find out how cybercriminals are targeting supply chains through vendors.
TechGenix: Article on the Latest Botnet Attack
Learn about the latest botnet attack and how you should prepare to protect your business.
TechGenix: Article on Firewall as a Service
Find out everything you need to know about FaaS and cloud solutions.



