New and Improved EFS
EFS has been around for quite some time within a Windows environment, but it has grown up a bit in Windows XP and Server 2003. EFS, Encrypting File System, is an excellent way to help protect data that is stored on a server or desktop. EFS is one of many security mechanisms that Microsoft provides in the buffet line of security measures meant to help protect data that is stored and transferred across the network. If you attempted to use EFS in Windows 2000, but found it somewhat clumsy or limited, you will are sure to be impressed with the new features that are now available in Windows XP and Server 2003. If nothing else, you should be aware of the changes and keep the prospect of using EFS in the forefront of your arsenal as a security measure when you are faced with critical data that must be protected.
What EFS is and What EFS is Not
EFS does help protect data as it is stored on a file server. Obviously this is ideal for laptops that store data for traveling users as the move from city to city, then back to the office. If a laptop is stolen, it takes some gymnastics to get into the operating system, as well as into the encrypted files that are protected within the file structure. EFS is not intended to be as robust as using physical devices that encrypt files, but it does provide for a significant increase to security compared to typical storage of files on a laptop.
EFS is not designed, nor does it provide, a solution to encrypt files that are sent across the network. When a file that is stored using EFS is sent across the network, it is first decrypted, then sent on the wire. This does expose the file to possible interception and attacks if you have not implemented some other form of protection for data on the wire. Microsoft provides the robust solution of IPSec within Windows 2000 and greater that can encrypt files as they are sent from point-to-point on the network.
If you are using EFS or EFS in combination with IPSec, you might see a hit to performance when accessing the protected files. The level of performance hit depends on many factors, including server hardware, network structure, network performance, level of protection used in IPSec, and the files that are being accessed. Of course, if the data is critical, a hit to performance resulting in a lag time will not be a huge concern.
Data Recovery
If you are familiar with how Windows 2000 dealt with EFS data recovery, you will be a little shocked at how Windows XP and Server 2003 handle the issue. First off, EFS data recovery is a key concept when using EFS, in case the original user that encrypts the file loses the private key for decryption or worse, maliciously encrypts files before leaving the company.
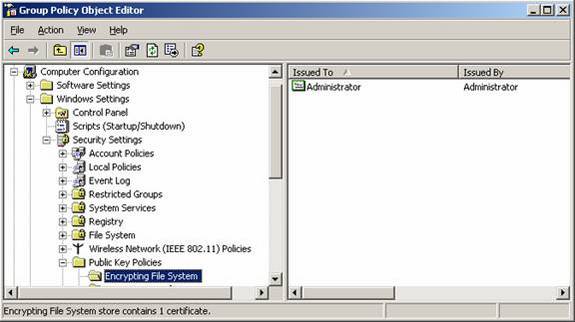
Windows 2000 domains by default configures the Administrator account as the data recovery agent (DRA). This can be seen within the Default Domain Policy, as shown in Figure 1. The idea is that when a user encrypts a file, the DRA is also given the private key so that it can decrypt the files in case of an emergency or disaster. There is quite a process that needs to be followed to decrypt these files, which can be understood by reading the article named “Implementing the Encrypting File System in Windows 2000” on TechNet.
Figure 1: DRA configured in the Default Domain Policy
If you ever want to “cripple” EFS for all domain computers in an Active Directory enterprise, you can just delete the DRA certificate from within the Default Domain Policy. This will in essence disallow any encryption, because Windows 2000 requires a DRA be configured for any encryption to occur. I do suggest that you back up this certificate before deleting it, although you can regenerate it if you have deleted it without backing it up first.
Windows XP and Server 2003 approach the DRA in a different manner. These operating systems don’t require a DRA. These operating systems can get by without a DRA, which can put the encrypted files in jeopardy if the original ability to decrypt the files is lost. The benefit is that there does not need to be a DRA configured within Active Directory or on the local system for these operating systems to perform the encryption of files.
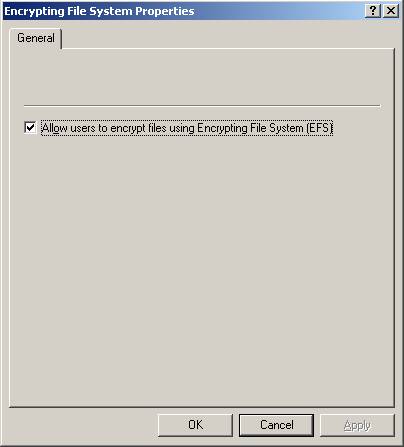
If you desire to disable encryption of files enterprise wide, you won’t be able to perform the same steps that you did with a Windows 2000 environment. The deletion of the DRA certification won’t do any good, since EFS no longer requires it for Windows XP and Server 2003. To disable EFS for Windows XP and Server 2003, you will need to go into the Default Domain Policy and configure the “Allow users to encrypt files using Encrypting file System (EFS)” check box, as shown in Figure 2.
Figure 2: Option to disable EFS for Windows XP and Server 2003
Multi-user Access to Encrypted Files
One of the major stumbling blocks of using EFS in a corporate environment with Windows 2000 was the limitation of only having a single user having access to encrypted files. In essence, the user that performed the encryption was the only user that could subsequently access the files. This limited the files that could be encrypted, omitting any files that were shared amongst multiple users in the enterprise.
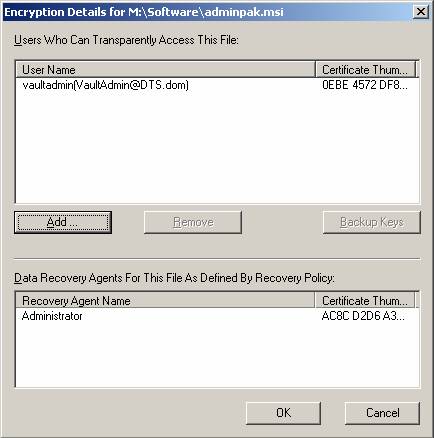
Windows XP and Server 2003 altered this behavior by allowing multi-user access to encrypted files. I feel that this new feature of EFS makes it a viable solution for a corporate environment, which before limited EFS to only be an option for a laptop. There are some configurations and gyrations required to get multiple users configured to use the same encrypted files, but it is not beyond the capabilities of even the most inexperienced network administrator. The key is that the user being configured to access the encrypted file must have a valid EFS certificate stored in Active Directory. This is required based on how the object picker searches for Active Directory for users that have the userCertificate attribute filled with a certificate. The interface that is used for selecting additional users that can access an encrypted file is shown in Figure 3.
Figure 3: Multiple users can be configured to access the same encrypted file
Encryption of Offline Files
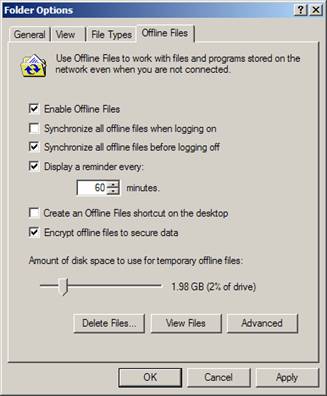
Another benefit of using Windows XP and Server 2003 is that files that are configured to be accessed offline when a user travels can be encrypted. This provides additional security and flexibility over Windows 2000, which forced users to keep a copy of the files on the laptop separate from offline files, if they wanted to encrypt the files while they traveled. The process to encrypt offline files is rather simple, once you get the offline files configured and working the way you want. The option exists within the Offline Files configuration settings within Windows Explorer. To access the option, you simply need to go to the Tools – Folder Options menu. From there, select the Offline Files tab, as shown in Figure 4.
Figure 4: Offline Folders tab in Windows XP allows for encryption of offline files
Summary
As you can see, EFS has grown up quite a bit from Windows 2000. Now, it is ready for a corporate environment and solves the nagging problems that EFS imposed in Windows 2000. The modification of how EFS uses and relies upon the DRA is a radical change, especially for management of the DRA. You do need to be cautious of your choices here, but at least you have options. Multi-user EFS by far is the biggest new feature of the new and improved EFS. Having multiple users having access to the same encrypted files allows for use of EFS for your HR, financial, and other essential data as it is stored on the server. For your traveling users, having the ability to use offline files and EFS in conjunction with one another makes administration easy, and the solution seamless. Be sure to test all of your solutions using EFS before rolling it out corporate wide, but you will see that EFS is now ready for use across the board.