The ongoing COVID-19 pandemic has forced many businesses and organizations to implement remote work solutions in a hurry, often without proper planning and preparation. Companies have tried various solutions to allow their employees to work safely from home instead of coming into crowded office environments. Mark Van Noy has been dealing with this situation at the University of Colorado Boulder in Colorado, where he works managing the virtual desktop infrastructure. They have implemented VMware Horizon, which securely delivers virtual desktops and apps across the hybrid cloud. Mark describes below how they use this platform to enable remote access to physical computers. Readers who are already using VMware in their environment may find Mark’s explanation helpful for enabling safe remote work for their own users.
What problem are we trying to solve?

With the increase of work from home, there has been an increase in the number of employees accessing their work desktop remotely. The most obvious way to accomplish this on Windows systems is to provide the IP address or the DNS name of the computer to the end-user then have them use Remote Desktop Protocol (RDP) after connecting through the company’s VPN. Using RDP certainly works, but connecting to the VPN adds more complexity for the end-user, and RDP is not a great protocol for connections with high latency. For companies that already have a VMware Horizon View environment for providing VDI, there is an alternative.
What does the horizon view do to solve the problem?
The Horizon View infrastructure brings flexibility, efficiency, and customer ease of use. By leveraging existing infrastructure, the Horizon product allows physical computers to function like full VDI virtual machines. For example, a pool of physical computers can be created without assigned users. When end-users login, they are automatically assigned to an available computer in the pool. With a conventional Remote Desktop connection, there is no convenient way to tell if someone is already logged into a computer. The connection has to be made by the end-user to the named computer itself. Similarly, pools of computers can be created using physical computers that assign users to specific computers so that the H.264 based Blast protocol can be used for latency tolerant display of the desktop. Using VMware Horizon also removes the risk of an RDP connection bumping an already connected session as a new user tries to connect to a physical computer.
What does VMware Horizon View do to solve the problem?
The Horizon View infrastructure brings flexibility, efficiency, and customer ease of use. By leveraging existing infrastructure, the Horizon product allows physical computers to function like full VDI virtual machines. For example, a pool of physical computers can be created without assigned users. When end-users login, they are automatically assigned to an available computer in the pool. With a conventional Remote Desktop connection, there is no convenient way to tell if someone is already logged into a computer. The connection has to be made by the end-user to the named computer itself. Similarly, pools of computers can be created using physical computers that assign users to specific computers so that the H.264 based Blast protocol can be used for latency tolerant display of the desktop. Using VMware Horizon also removes the risk of an RDP connection bumping an already connected session as a new user tries to connect to a physical computer.
What is needed to get started?
First and foremost, an existing VMware Horizon View infrastructure is needed as it is unlikely worth the effort to build out new servers simply for a better way to connect to physical computers. It is also highly desirable to have at least one User Access Gateway, UAG, to remove the need for an active VPN connection.
Detailing how to configure VMware Connection servers and UAG appliances is beyond the scope of this article. The capabilities of the built-out VDI infrastructure will apply to the physical pools. So, if HTML access to VDI has been fully configured, then end-users can access physical computers with a web browser without needing to install any client software, for instance.
How to implement VMware Horizon
Begin by creating a new set of Group Policies to limit the number of connections that can simultaneously be made to any individual computer and to allow appropriate users to connect. The VMware Horizon agent relies on some RDS settings to determine how it should behave. For example, the agent assumes that Windows allows multiple Remote Desktop connections, which results in non-server flavors of Windows kicking logged in users off when another user tries to connect by default. Setting the maximum number of connections allowed to 1 will prevent sessions from getting kicked. Similarly, the Horizon agent relies on the Remote Desktop Users group to determine who is allowed to log in so appropriate users must be added to the Remote Desktop Users local group. Group Policy Preferences could be used rather than the older Group Policy for more granularity rather than using the GPO settings specified below.
Computer Configuration\Policies\Windows Settings\Security Settings\Restricted Groups\Remote Desktop Users
Computer Configuration\Policies\Administrative Templates\Windows Components\Remote Desktop Services\Remote Desktop Session Host\Connections\Limit Number Connections
- Enabled
- RD Maximum Connections allowed = 1
- Restrict Remote Desktop Services users to a single Remote Desktop Services session: Enabled
Next, the actual agent needs to be deployed to the physical computers that should be managed. The best way to deploy the agent is to use the command line install switches even if the agent is installed manually. The interactive installer does not expose the option to set the VDM_VC_MANAGED_AGENT property to false, which is a required setting to use the agent on physical computers. Note that there is no space in the command line between the double quotes after the v and the forward slash before the qn. If a space is placed between these elements, the install will fail.
VMware-Horizon-Agent-x86_64-7.12.0-15805436.exe /s /v”/qn VDM_VC_MANAGED_AGENT=0 VDM_SERVER_NAME=<broker/connection server> VDM_SERVER_USERNAME=<username> VDM_SERVER_PASSWORD=<password>”
The username and password need to be a service account with appropriate permissions to join computers to the domain used. There are also additional options that can be specified as properties on the command line. (VMware provides a list of the available options.)
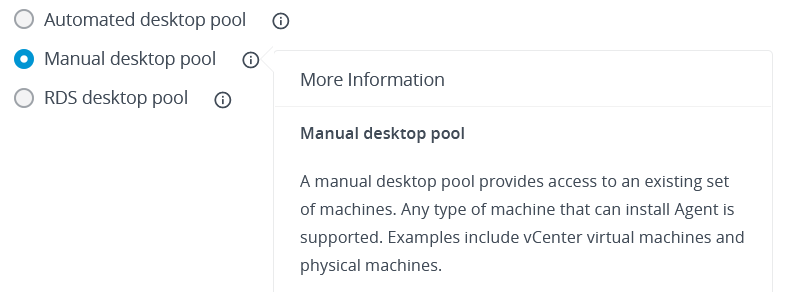
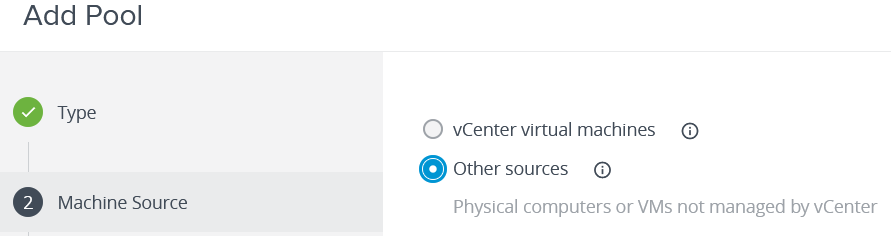
Once the agent has been installed, the final step is to create pools using the Horizon Management Console. Since physical pools of computers cannot be directly managed by VMware, the options are significantly limited compared to setting up a traditional VM based pool. This actually makes setting a pool up fairly simple. When creating a new pool, select the Manual desktop pool option. Then select the Other sources options when prompted for the source of the computers. The user assignment can be either floating or dedicated, with floating being the better choice for training labs. If access through a web browser is a desired feature, then the Remote Display Protocol should be set to VMware Blast. Otherwise, PCoIP or RDP could also be used. For step seven of pool creation, at least one computer must be added to the pool. This is why it was important to get the agent installed on the desired computers before creating pools. Horizon will only display computers to add to the pool that have checked in with the Connection servers through the installed agent.
Since VMware Tools cannot be installed on physical computers, there is some missing functionality. Most notably, if multiple NICs are present on the physical computer, or virtualization software such as Hyper-V has created multiple virtual NICs, the Horizon agent could become confused as to which NIC it should be communicating over. This could cause computers to show in Problem Computers as Agent Unreachable. If a computer needs to have multiple NICs and have access through Horizon, VMware has provided documentation on how to specify which network interface should be used. The documentation was written for specifying the appropriate interface with VM’s in mind.
VMware Horizon: Right for you?
Should you use VMware Horizon to access physical computers? If you already have Horizon in your environment, then probably. A physical computer will use up a concurrent user license just like connecting to a VM, so a lack of licenses could make this option a poor choice. Otherwise, being able to connect through just a web browser or the Horizon Client without having to worry about VPN connections or remembering IP addresses certainly is a better end-user experience. We currently use Horizon to provide access to our physical lab computers, and for that use case, it has been a real boon since our students do not need to know anything more than that they want to connect to a specific pool name.
Featured image: Shutterstock






My question is how do you indisputably prove the identity of an employee who uses a VPN solution to access virtual desktops remotely?
Hello Nicolas,
VMware Horizon does not use IP address or other location methods to determine identity. In order to access virtual or physical desktops without a VPN then either UAG or VMware Security servers need to be in place. The UAG appliances pre-authenticate credentials before passing a session along to the VM or physical desktop. That authentication is, at a minimum, the Active Directory credentials of the user trying to access resources. We decided to place UAG appliances in front of all our Horizon servers so that all traffic, no matter where it originates, has to go through the UAG pre-authentication process. It is certainly possible to forego UAG servers for connections originating from on-premises so that users connecting with a VPN do not need to go through the UAG appliances, but then they will still need to authenticate with their Active Directory credentials in order to access resources.
Hi Mitch, thanks for the article. I am attempting to follow this article but when I use the RDP protocol to connect I get an authentication error because it looks like it’s trying to connect to 127.0.0.1 (my local host). Is there a setting that was missed? Blast works but then the screen does not blank out on the remote end.
Hello Bill,
Since I wrote this, I received a definitive response from VMware that RDP is not supported despite the option being presented. You will need to stick with Blast. If you are locally connected to a Windows 10 computer and then connect through Horizon with Blast I would expect the screen to not blank since Horizon should be connecting to the already active session. I have not tried this to confirm. If no one is logged in to the computer and a Horizon connection is made then the computer should still look like it is waiting for a login; much like it would appear if an RDP connection was made.