May 2017 will be remembered for years to come for delivering the most hard-hitting lesson for global IT-dependent enterprises on why cybersecurity, and ransomware in particular, is going to be their biggest concern. The WannaCry cyber blackmail ransomware spread across systems in several countries at lightning speed, giving little time for IT experts to secure their systems. By May 15, 2017, the count of infected systems had reached more than 250,000 across 150 countries.
Though security experts were able to ultimately find a kill switch to neutralize the ransomware, they were soon staring at new variants of the same ransomware. This made it official – the war between good and bad IT is on now, and WannaCry seems to have drawn first blood. The hue and cry has lessened now, and thankfully, IT thought leaders, experts, security educators, and IT service vendors – all are shifting attention towards the key lessons that the bitter experience of WannaCry left on everyone’s palates.
Let’s tell you more about these lessons. Before that, however, here’s a bit more on WannaCry than most people know.
Is WannaCry the most technically advanced ransomware ever?
The answer’s a resounding “NO!” That’s because it doesn’t differ much from other ransomware in its basic operations. It’s a combination of several disparate but well-executed and well-tested parts. Since most of the components are previously tested, the perpetrators have succeeded in upgrading and adapting the ransomware quickly enough to defeat the efforts of global IT experts to diffuse it.
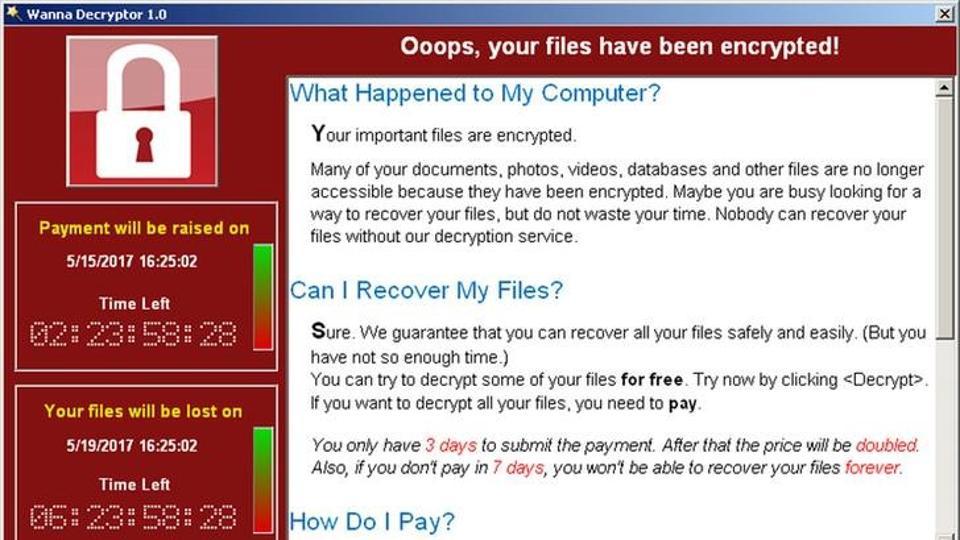
It’s same as any ransomware in the sense that it comprises three basic components. Firstly, there’s a mechanism to infect a system to start the chain. Secondly, there’s a mechanism to encrypt system and data files in the infected computer. Thirdly, there’s a mechanism to communicate the ransom amount and payment processing details to victims. WannaCry, however, adds a fourth element to the mix. It takes advantage of a Windows vulnerability to spread the ransomware. This means that within minutes of infecting one computer, it can overpower an enterprise’s entire network. This caused the wildfire-like spread and impact of WannaCry.
On to the lessons that enterprises would do well to learn from the ravages of WannaCry.
You just can’t ignore patch management
Patch management has been the savior for security professionals for several years now. Patching has prevented innumerable attacks already, and invariably, most successful attacks are attributed to lack of proper patch management practices in the affected network and enterprise. The massive attack of WannaCry was a result of the fact that hundreds of thousands of affected computers were running unpatched operating systems.
Continuous patch management practices are a key to ensuring sustained security against similar threats in the present and near future. Microsoft has released emergency patches in response to the outbreak of WannaCry. Running an unpatched or outdated operating system version in a production environment is an open invitation to similar ransomware and malware attacks.
Bridge the gaps in your enterprise IT practices
A question – how do you patch a system that doesn’t even exist in your books? Hackers make their first attempts at intrusion of enterprise networks via these unmonitored and forgotten systems that continue to exist and be a part of the network. Inconsistencies in IT assets management practices create these gaps. The result – your routine security upgrade practices such as patch management leave out these untracked assets. Over a period of time, the attack surface of your enterprise’s IT network becomes large enough for cyber criminals to make successful intrusion attempts.
To avoid such an event, enterprise IT experts need to envisage their organization’s networks as hackers, and look for the minutest of gaps. Secondly, IT asset management practices need to be tightened to bring all devices within the scope of the regular security upgrades and future readiness activities you conduct within the organization.
Risk mitigation approaches such as network segmentation
It’s hardly any wonder that so many organizations fell victim to WannaCry in spite of being aware of their computers’ security vulnerabilities. Updating legacy and embedded systems is a technical challenge in most organizations, which is aggravated by restrictions linked to government regulations and practices, discontinued support for old OS, organizational concerns about system downtime, and disruptions during the upgrade process.
This is where network segmentation has a tremendous role to play in risk reduction. Segmentation demands careful network architecture and expertise to manage the requirements of frequent changes in router and firewall settings. Adoption of rigorous network verification methods, however, helps with implementation of network segmentation, which keeps large organizations safe in cases of attacks of contagious malware such as WannaCry.
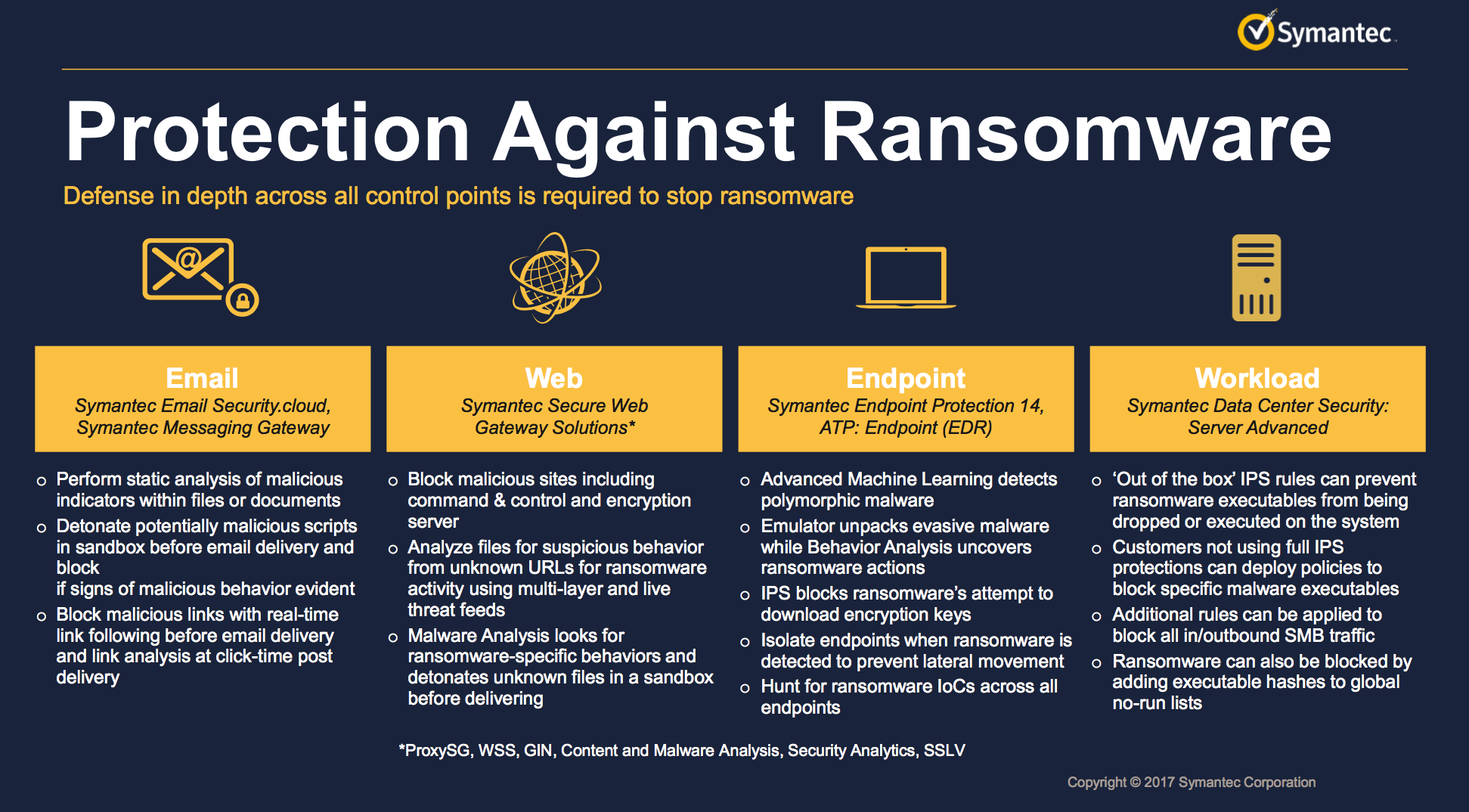
Implications of security vulnerabilities
WannaCry has been the equivalent of a whack on the face of IT security professionals. In spite of the increasing concern about cybersecurity, efforts to improve existing IT security has been excruciatingly slow.
WannaCry impacted the UK’s National Health Service to the extent that critical health-care devices were rendered useless, jeopardizing the life and health of several people. This puts into perspective the real-life implications of IT disruptions. It’s no longer just a question of data protection; we’re looking at multibillion dollar losses, loss of lives, and complete disruption in the flow of life of humans, all because of attacks such as WannaCry.
Acknowledgement of these WannaCry system security lessons and diligent effort to implement the learning in the form of better IT management practices are the way forward for global IT stakeholders.




The perpetrators, whom ever they are, need to be treated as terrorists. Being “WannaCry” affected healthcare systems and probably resulted in death the perpetrators should be charged with at least second degree murder.