
Source: Unsplash
Team82 research has found a generic bypass to industry-leading web application firewalls. This includes those used in Palo Alto Networks, Amazon Web Services, Cloudflare, F5, and Imperva. Researchers found that an SQL injection, or SQLi when launched alongside a JSON syntax, blinded most of these web application firewalls.
Since cybercriminals can use this SQLi vulnerability “to exfiltrate sensitive information,” Team82 quickly alerted the vulnerable vendors and web database administrators. They instructed them to patch their systems immediately.
SQLi remains the top security vulnerability for cloud providers and IT companies. While easy to defend against, the sheer scale and the ease with which they’re carried out make SQLi a continual threat.
Generic Bypass Penetrates Firewalls in Major Cloud Providers

Source: Claroty
The discovery of the web application firewall vulnerability is an all-too-familiar story. Researchers serendipitously stumbled upon something they didn’t set out to find in the first place. Researchers at Team82 started investigating Cambium Networks’ wireless device management platform. As their research continued, the team became interested in Cambium’s cnMaestro cloud network manager application hosted on AWS.
After discovering several security vulnerabilities in the application, the researchers zeroed in on the SQLi vulnerability. Later, they developed the bypass technique. This high-threat exploit—labeled CVE-2022-1361—could allow an attacker to retrieve information about user identity and devices.
In testing the bypass technique against major web application firewalls, the researchers didn’t alter the mechanism of the SQLi attacks, except for a few functions based on JSON implementations in different databases. This was done to ensure the vulnerability was common to all web application firewalls, and the technique, thus, could deservedly be called “generic”.
The Significance of Web Application Firewalls
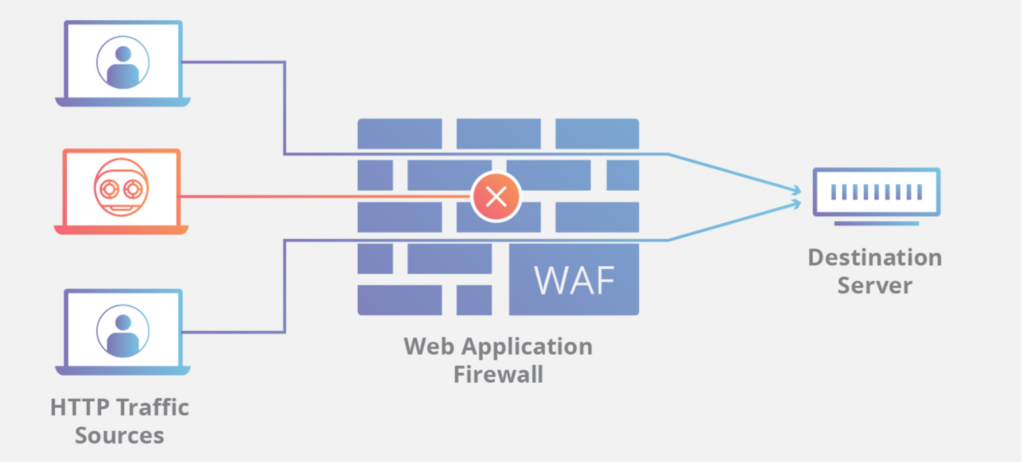
Source: Cloudflare
This generic bypass technique has blown the lid off web application firewalls that are supposed to protect company and user information stored in databases. First introduced around 2000, web application firewalls counteracted vectors like cross-site scripting or XSS—executed in JavaScript—and SQLi—executed in MySQL. Web application firewalls protect web-based applications, application programming interfaces or APIs, and online databases hosted on the cloud from HTTPS traffic.
Historically, these firewalls have performed well, and bypasses have been rare. Even the cloud-based data security breaches at Verizon, Accenture, and Kaseya didn’t happen due to the failure of web application firewalls. They were due to negligence and the simple misconfiguration of databases.
JSON Syntax—the Secret Ingredient in Razing Web Application Firewalls
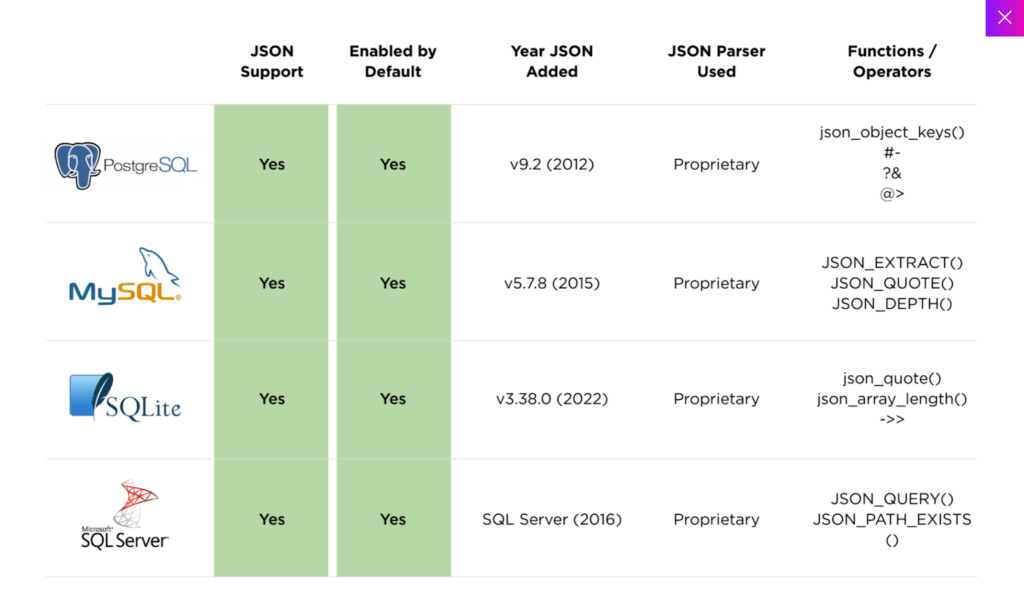
Source: Claroty
Team82 tested various types of code before discovering the generic bypass that uses JSON and SQLi to raze web application firewalls. The technique works possibly because relational databases now use both JSON and MySQL. This is also true for the latest editions of MSSQL, PostgreSQL, SQLite, and MySQL.
JSON sends data from servers to web applications and vice versa. This increases the operational efficiency of databases. But this seems to have come at a steep cost: security. Security, cost, and convenience have a triangular relationship, and developers may have sacrificed security for efficiency when they added JSON support to relational databases.
Web Application Firewall Vulnerabilities Should Alarm Everyone
In today’s interconnected world, a single compromise can ripple out to affect many. This interconnectedness makes securing networks even more important for businesses using cloud hosting providers.
Otherwise, cybercriminals can easily access their information by exploiting various firewall vulnerabilities. And what’s more is that they can then sell that information on the darknet, hold it for ransom, use it for business email compromises, or launch social engineering scams.
Using quality tools for network security and managing cloud hosting operations can go a long way. Moreover, cybersecurity shouldn’t be reactive but proactive. Expect a breach to happen, devise measures to protect against it, and implement them.
In this instance, Team82 discovered the security vulnerability and alerted the concerned companies before cybercriminals could catch wind of it even existing. But the day a black-hat organization discovers such a vulnerability, they won’t write a blog about it.
Safeguarding Information Accessible on the Web
The Team82 report has sparked discussions about the vulnerability of IoT and OT processes on the cloud. Yet it has gone a step further. It provides a solution for the problem it diagnosed with the cloud systems: regularly updating security tools may shield companies against such attempts.
Companies should regularly seek and patch security vulnerabilities by scanning, updating, and monitoring their systems. Database misconfiguration can be catastrophic and lead to cybercriminals exfiltrating sensitive company information. Knowing about such vulnerabilities and the safeguards against them is essential as more businesses migrate services to the cloud.



