Do you know that you can still lose your sensitive information to cybercriminals even when you’re using a security tool such as VPN? We all know that surfing the web through a virtual private network ensures that no one sees you or steals your data online. But sometimes, this may not work for you if there’s a WebRTC leak in the web browsers you’re using. Bear this in mind: VPN services are important if not compulsory for everyone using the Internet. But if you’re not aware that there are WebRTC leaks in your web browser, a weak VPN network can’t hide your IP address online.
This article will tell you all you need to know about WebRTC leaks, what it is, how it happens, how you can test for it and block it, and how you can disable it on most web browsers.
Let’s do it!

What are WebRTC leaks?
WebRTC is an acronym for Web Real-Time Communication. It is a technology that facilitates communication that exists between web browsers and websites without the need for an intermediate server.
It makes it possible for a web browser to send content to another user online and receive content. For this to work, WebRTC establishes a unique communication channel from your web browser so that they can exchange all kinds of information with the websites you visit.
WebRTC has many benefits, including reducing lag time, supporting mobile applications, and facilitating group-calling services. In addition, this technology is an open-source application, and it is free for commercial and personal use.
When do WebTRC leaks happen?
WebRTC opens up vulnerabilities in your web browsers due to how it works. To establish real-time communication between two devices, the real IP address of the devices must be shown. The problem is that a third-party website may access your IP address through the WebRTC in the browser you’re using. When that happens, you’ve had a WebRTC leak.
The worst is that WebRTC makes it possible for every website you open to get your IP address even when you’re using a VPN. So, you may be unknowingly revealing your identity to different hackers in multiple locations. Unfortunately, real-time communication between devices is the main function of WebRTC, so there’s no way to fix the vulnerability.
WebRTC leak is more frequent where people depend on unreliable VPN services that can’t protect users from such attacks. WebRTC channels, in some cases, bypass a VPN’s encrypted tunnel through which your traffic flows. Unfortunately, once your IP address is sent out, your privacy is no longer protected. The only option is for a user to block the leak or disable the software.
Steps to test for WebRTC leaks
Before you can fix a WebRTC leak, you must first check the VPN network for a possible IP leak. To do that, follow these simple steps:
- Disconnect your existing VPN from your web browser.
- Open Google on any web browser such as Chrome and type in this request “What is my IP.” After typing it, hit enter for Google to reveal your main IP address.
- Write down your IP address and exit the browser you used.
- Launch your VPN service once again and then refresh the web page.
- Open Google on your browser again and type “What is my IP” hit enter and note the IP address that comes up as your main address.
When you compare the two IP addresses, there should be a difference if there’s no WebRTC leak. But if you still get your main IP address even after relaunching your VPN, that means you’re not anonymous online anymore. Many websites and hackers have gotten hold of your IP address and can quickly identify you.
In that case, you must try to block the WebRTC leak through your browsers by using the information we’re going to share below.
How to block WebRTC leaks
When it comes to blocking WebRTC leaks, there’re many options. However, the easiest way to block a WebRTC leak is by using strong VPN services such as Express VPN and NordVPN. These two services are reliable, strong, and can protect your IP against WebRTC leaks.
It doesn’t matter whether you’re using their browser plugins for Chrome, Firefox, or using their regular VPN. Their network is solidified with powerful encryption that can mask your IP address no matter the website you visit. Moreover, ExpressVPN and NordVPN facilitate WebRTC connections through your anonymous IP address once authorized.
Another way to block a WebRTC leak involves a direct approach from your web browser. This process is complicated, and it disables the WebRTC function. Sometimes, if you don’t handle it well, it may cause your web browser to malfunction.
How to disable WebRTC on web browsers
1. Firefox web browser
There’s no built-in process to disable WebRTC from Firefox. That’s why it’s usually difficult for some people to do. So, do the following:
- Type in “about:config” into Firefox address bar and press Enter. A warning will pop up.
- Click “Accept the Risk and Continue.”
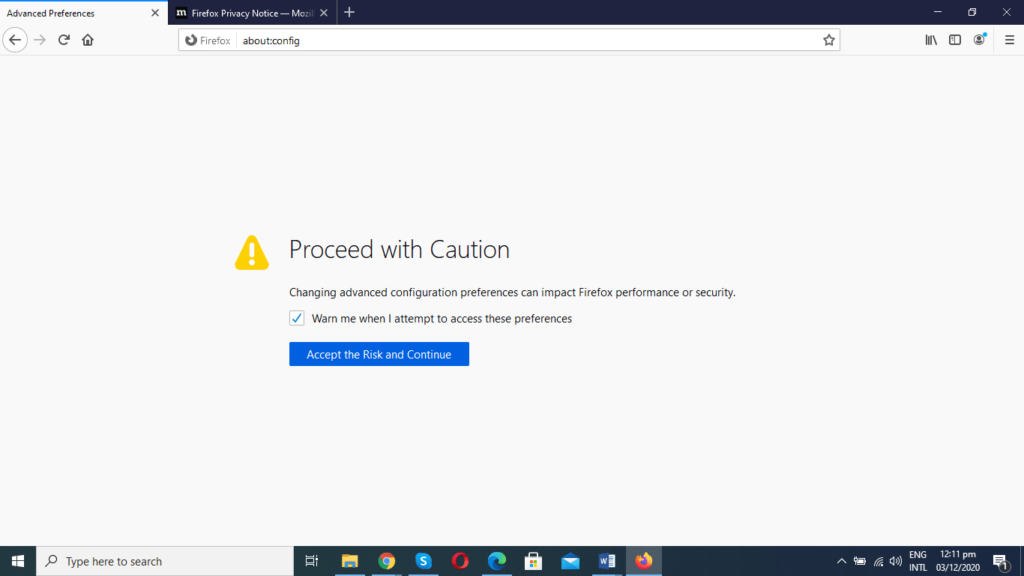
- Click “Show All.”
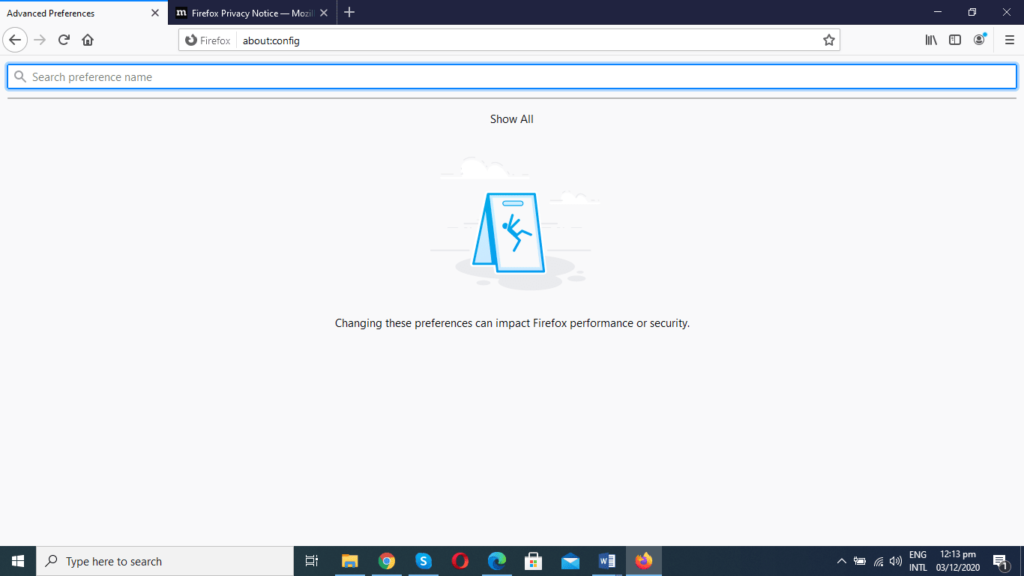
- A long list will appear after clicking on “Show All.”
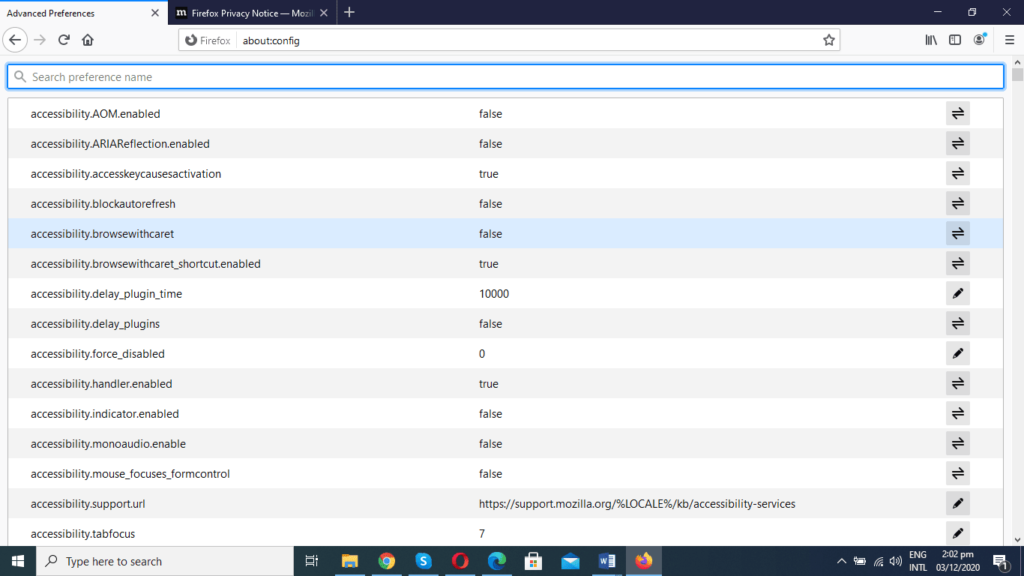
- Type in “media.peerconnection.enabled.” When you write it, you’ll get a screen like the one below, but it will have True instead of False.
- Then press the toggle button at the right to change it to False.

- Once you’ve changed it to False, you’re done with disabling WebRTC on the browser.
2. Chrome browser
Disabling WebRTC from Chrome is very complicated. That’s why we recommend that you get a Chrome extension such as WebRTC Leak Prevent to prevent it. Unfortunately, you can’t disable WebRTC from Chrome without an extension because it involves manual editing of setting files that may lead to browser malfunction.
But the Chrome Extension we mentioned above can change the security & privacy setting of the WebRTC but can’t disable it.
3. Safari browser
If you’re using this web browser, you can also disable WebRTC. But note that the developers of the browser only recently implemented WebRTC to it. That’s why it may seem more complicated than Firefox. But you can get it right by doing the following:
- Open Safari browser.
- Click on the drop-down arrow beside the Setting Icon.
- Click on Preferences.

- Click Advanced.
- Check “Show Develop menu in menu bar.”

-
- Click on the “Develop” tab.
- Choose “Experimental Features” from a drop-down menu that’ll appear.
- Click on “WebRTC mDNS ICE candidates” if it’s “checked.
- That’s it! You’ve disabled WebRTC from Safari.
4. Microsoft Edge
If you’re using Microsoft Edge, you should know that the browser has added the WebRTC features. It also has its version known as ORTC. But it is not possible to disable WebRTC on Edge. What it allows is to conceal your local IP over the software connections but not the public IP.
The good news is that you can use the “WebRTC Leak Shield” extension from the Microsoft application store. But we can’t recommend it since the details about it are not enough to verify its effectiveness.
So, if you want to make sure that you’re not a victim of WebRTC leak on Microsoft Edge, use NordVPN and ExpressVPN. The two networks are very effective in hiding your main IP address no matter the website you visit.
Final words on WebRTC leaks
The best way to handle a WebRTC leak is to prevent it from happening in the first place. That’s why we recommend that you use VPN services such as NordVPN and ExpressVPN to protect yourself against unnecessary exposure online.
Instead of giving hackers the chance to compromise your privacy, it’s better to be safe with a strong and reliable VPN service. But if you do not use a VPN or you’re already a victim of WebRTC leak, follow the steps we shared above to stop it.
Featured image: Flickr / Blue Coat Photos



