Windows 11 is out and this has been the talk of the town! This new operating system has also put the spotlight on hitherto unheard-of terms such as the Trusted Platform Module (TPM) technology. Though this technology has been around since 2016 and has been used in Windows 10, Windows Server 2016, and Windows Server 2019, it was not ubiquitous. But Microsoft has made TPM mandatory for Windows 11, and suddenly, everyone is talking about it now.
We’ll also hop on this bandwagon to explain what this buzz is all about in simple terms that everyone can understand.

What is the Trusted Platform Module (TPM)?
The Trusted Platform Module (TPM) is a device that creates trust in computing devices. They are dedicated microcontrollers where integrated cryptographic keys are used for security.
In the earlier versions of Windows OS, TPM, a secure crypto-processor with cryptographic keys, was optional, but due to the growing interest in cryptocurrencies coupled with the ever-increasing online security concerns, Microsoft believes this is integral for next-gen operations.
TPM is also tamper-resistant, and as of now, no malicious software can break its security.
There are many variations to TPM and these are managed by the Trusted Computing Group (TCG).
Is TPM on your computer?
Microsoft has made TPM mandatory before you can install Windows 11. Here’s how to check if it’s available and enabled on your computer:
- Open a run dialog box (press WINKEY + R)
- In the dialog box, type “tpm.msc”
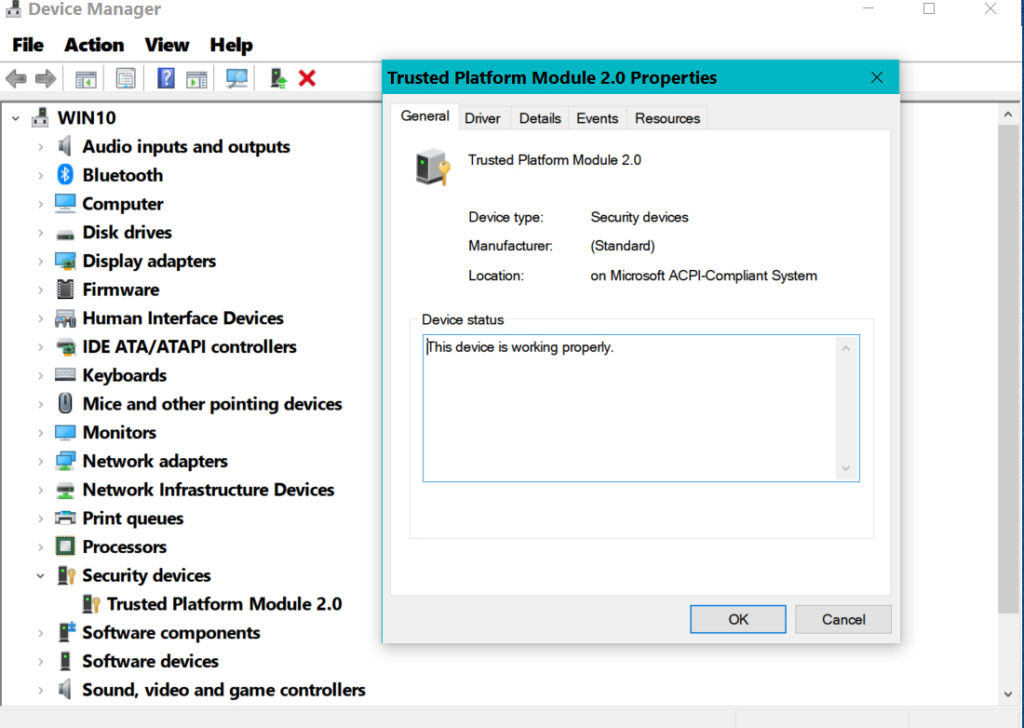
- If TPM is enabled, you will see this screen:
- If you do not have TPM or it is not enabled, you will see the screen below:
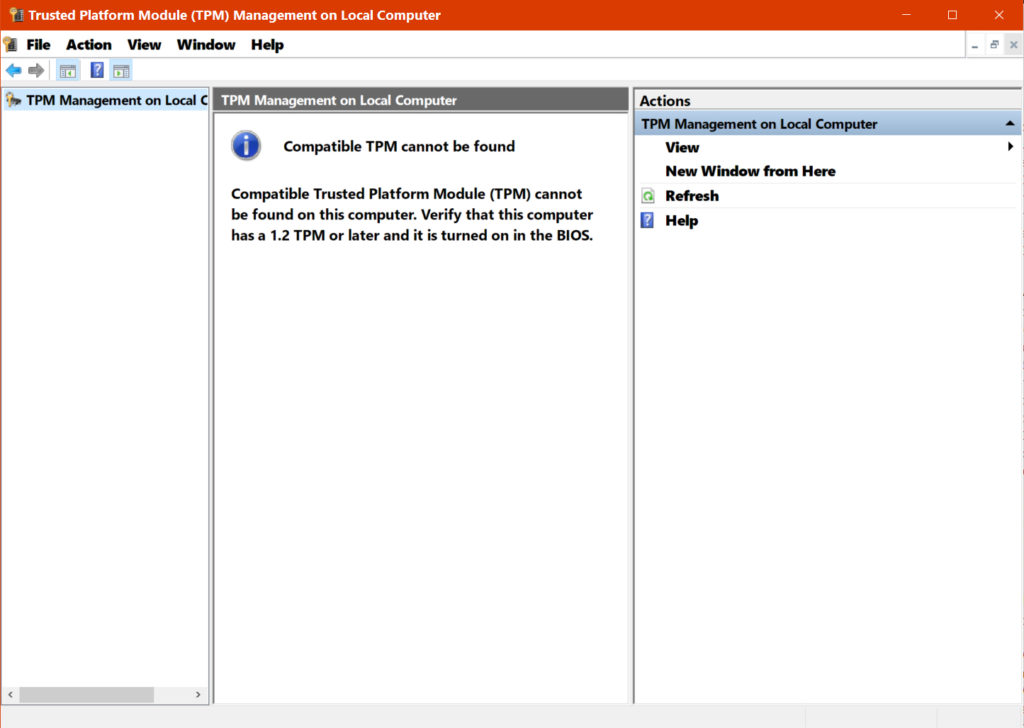
If you receive the “TPM cannot be found,” there is still a chance you have it but it has not been enabled. There are several ways to enable it. WindowsCentral has a good tutorial showing you how.
So, why is TPM so important for Windows 11?
There are a few core elements in TPM that make it so invaluable from a security standpoint. Let’s briefly look at three of them to better understand the role of a TPM in an operating system.
Trust
The core element of TPM that makes it so useful in today’s world is trust. The TCG defines trust as expected behavior. You expect an entity, like a university, to behave in a certain way. To know this expected behavior, you must know the identity of the entity. For example, a bank will behave very differently from that of a university.
Likewise, TPM has many schemas to determine the identity of hardware and software components, so it’s possible to know the expected behavior of each, and through it, trust is established as any unexpected behavior is flagged.
There are many building blocks of trust such as,
- Trusted Building Block (TBB)
- Trusted Computing Base (TCB)
- Transitive trust process
- Trust authority
- Roots of Trust, further divided into Root of Trust for Measurement (RTM), Root of Trust for Storage (RTS), and Root of Trust for Reporting (RTR).
These components come together to establish trust and eliminate security vulnerabilities.

Protection
This component handles the protection given by the TPM for a computing device and is further broken down into Protected Capabilities and Protected Objects.
As the name suggests, the protected capability is an action that must be performed correctly, while a protected object is data, including keys that must be protected. Both these are necessary for TPM to ensure there are no unauthorized changes (protected capability) to sensitive data (protected object).
Cryptography
This module handles TPM’s cryptographic functions and it uses some of the traditional and time-tested operations such as,
- Hash functions
- Asymmetric and symmetric encryption and decryption
- Asymmetric and symmetric signing and signature verification
- Key generation

Please note that more components make up the TPM’s architecture, but we’ve talked about these three to give you an idea of how TPM plays a big role in security.
A brief look into TPM implementation
From an implementation standpoint, TPM is a component that’s separate from the system (host) on which it is implemented, and it interacts with the host through an interface defined by the TCG.
TPM is implemented on a host directly or indirectly through physical resources assigned to it permanently or temporarily, depending on the configuration. Sometimes, these resources can be spread across different physical boundaries as well.
In some cases, TPM is implemented as a single chip that connects to the host through a low-performance interface. In such implementations, the TPM component comes with a processor, RAM, and ROM. The downside is that the host can change values only through the I/O buffer.
Using TPM
From Windows 10, Microsoft designed the operating system to automatically initialize and handle TPM. This means, as a user, there’s nothing for you to do as the operating system takes ownership of TPM and its operations.
Still, if you’d like to make changes to its configurations, which is not recommended, go to the TPM management console. Press WINKEY + R and type “tpm.msc” when you want to reset the keys or do a clean installation of the Windows operating system.
Many hardware companies like Dell and HP include an intuitive application for accessing TPM’s values and changing its configuration.
Why is everybody talking about TPM?

TPM is widely regarded as a technology that can power the next-gen computational leap. In this context, it offers the following benefits:
- Generates and stores the cryptographic keys
- Has the power to limit the use of these keys
- Authenticates devices with its unique RSA key
- Stores the security measurements and through it, ensures platform integrity
- Provides the evidence to know how a system started and a TPM-based key ensures that the correct software license was used to start the system.
- Prevents phishing attacks.
- Limits the number of incorrect authorization guesses. When the threshold is reached, the TPM will initiate the directory attack logic to prevent any more guesses.
So, how do all these fit into your operating system, and why has Microsoft made TPM 2.0 a system requirement for installing Windows 11?
Protects unencrypted text
All the data that we send from our system are not encrypted, especially the ones sent as plain text. Still, your data must be protected, especially if it involves confidential data like passwords or encryption keys.
TPM uses both hardware and software to protect this unencrypted data, even when it’s sent as plain text.
Detects system compromise
TPM chips quickly sense when a malicious piece of code has compromised your system and strives to fix the problem right away. Some chips even scan the BIOS at the time of startup to detect any unauthorized changes.
Such measures reduce the chances of a system compromise.
Safe storage place
TPM is a safe storage place for your encryption keys and passwords, as it’s not easy to access these chips without authorization.
For example, you have a username and password to access your device. These credentials are stored on a TPM chip rather than on the hard drive because you can generate cryptographic keys to protect your login credentials. Also, you don’t lose them when your hard drive crashes.
Microsoft believes that such a safe storage place is critical in the future, as there’s greater adoption of digital security through cryptographic keys.
Essential for all users
Microsoft has made it a system requirement for all versions of Windows 11 because it contends that security is crucial not just for enterprises but also for individual users, as there’s a greater push for decentralized identity.
But the good news is, you don’t have to do anything much as most laptops and desktops have TPMs since 2016. Still, it could be a good idea to quickly check this requirement before installing Windows 11.
Windows 11 and TPM: Next step in Microsoft security
For these reasons, Microsoft has set a trend for built-in security in each device by making TPM a system requirement for its Windows 11 OS.
What do you think of TPM? Do share your thoughts in the comments section.
Featured image: Shutterstock / TechGenix photo illustration



