Everyone is talking about “Zero Trust” these days, but what does it mean? If you’ve been struggling to understand this concept the way I have been, then the explanation below by my colleague Sasha Kranjac may be helpful. The explanation is tailored especially around Microsoft’s implementation of Zero Trust within the context of Azure Active Directory, but it’s also a good primer generally on the subject of what Zero Trust is all about. Sasha has a lot of expertise in this area as he is an Azure and security specialist, consultant, and cloud architect who helps companies and individuals embrace the cloud and be safe in cyberspace. Sasha is CEO and cloud security architect at Kloudatech and he delivers Microsoft, EC-Council, and his own custom Azure and Security courses and PowerClass workshops, consulting and architecting cloud solutions internationally. He is also a Microsoft Most Valuable Professional (MVP), Microsoft Certified Trainer (MCT), MCT Regional Lead, and a Certified EC-Council Instructor (CEI). To learn more about Sasha, you can follow him on Twitter: @SasaKranjac.

What is this Zero Trust everyone is talking about these days? Under what rock has this term been hiding all the time? What does Zero Trust mean anyway?
The Zero Trust concept, or the concepts that Zero Trust encompasses, is not new at all. During the Jericho Forum in 2003, the term deperimeterization was discussed — ways to protect an organization’s data and systems’ boundary by removing a boundary between outside networks and an organization and protecting it on multiple stages by using a combination of secure protocols, encryption, and multiple authentication levels.
Vendors other than Microsoft have adopted Zero Trust as well, and this principle is not exclusive to cloud providers, either.
Not so many years ago, we had data residency on-premises only, where little or an insignificantly small amount of data left protected organizational networks. Today, the security landscape is completely different, where data is no longer stored on file servers and desktop computers but on laptops, tablets, mobile phones, in workers’ pockets and backpacks, roaming outside what was once perceived as security of organizational boundaries.
In the Zero Trust model or concept, instead of believing that everything behind a corporate firewall is safe, we believe that every access request is not safe and is not trusted. We act as if every request originates from an untrusted, uncontrolled network, regardless of where the request originates from or what resource it accesses. We utilize segmentation and least privileged access to mitigate lateral movement, ensure that every access request is authenticated, authorized, and reviewed.
Nowadays, we need a security model that can effectively adapt to modern environment complex architecture, including mobile, roaming data, and users, that protects every entity wherever it is located, whoever it might be. Data, applications, devices, people — Zero Trust strategy is designed to question all and to protect all.
There are three main principles of the Zero Trust strategy:
- Assume a breach. Verify that all sessions and requests use end-to-end encryption. Use access segmentation for devices, networks, and users to prevent or reduce lateral movement. Implement threat analytics to gain insight and have greater visibility.
- Verify explicitly. Implement comprehensive authentication and authorization on all datapoints, comprising user identity, user and sign-in risk, device status and health, data classification, and location.
- Use least privileged access. Restrict user access and privileged access using just-enough administration and just-in-time administration (JEA, JIT), conditional or risk-based policies, and data protection policies and technologies.
What is more important, the Zero Trust approach includes automated security policy enforcement to ensure compliant behavior throughout the entire organization. This diagram by Microsoft illustrates the Zero Trust Security components. You can view the original page here.
Microsoft defines several components in the Zero Trust model that deserve our security focus. Each of these parts is foundational to the security approach and are sources of signals and a security control plane:
- Identities. Today, identities are not just people but devices and services.
- Endpoints. Continuous monitoring of device health and security is crucial, from personal and IoT devices to servers and desktops.
- Applications. Cloud or on-premises applications and APIs need access controls, usage analytics, monitoring, and secure configuration.
- Data. Securing data is fundamental. We need to ensure data is secure when in motion or at rest, on devices, or when it leaves infrastructure and applications.
- Infrastructure. On-premises or cloud infrastructure deserves proper security too. Restricting and controlling access using just-in-time and just-enough administration monitoring for anomalous behavior, or using automation to shorten response time to risky behavior.
- Networks. Segmenting networks using subnets, multiple networks, user-defined routes, end-to-end encryption, monitoring, and analytics.
This diagram by Microsoft illustrates the concept of Zero Trust Security policy enforcement. You can view the original page here.
So, which Microsoft products should we use to establish a Zero Trust strategy? Well, different organizations will have different approaches to implementing Zero Trust methodology to security simply because no organization is the same, does not use the same products, and does not have the same infrastructure architecture. But the principles are still the same. Let us take a look at one approach.
A Zero Trust approach should start with protecting identities, where each access request is equally treated and verified using strong identity authentication. Microsoft Azure Active Directory (Azure AD) is an identity and secure access management solution (IAM) that supports multifactor authentication (MFA), where adding a second factor in the authentication process can reduce lost or leaked passwords problems. To make authentication even stronger, we can use passwordless authentication using a mobile authenticator app or FIDO2 token for even better protection. This diagram by Microsoft explains how Azure AD Conditional Access works. You can view the original page here.
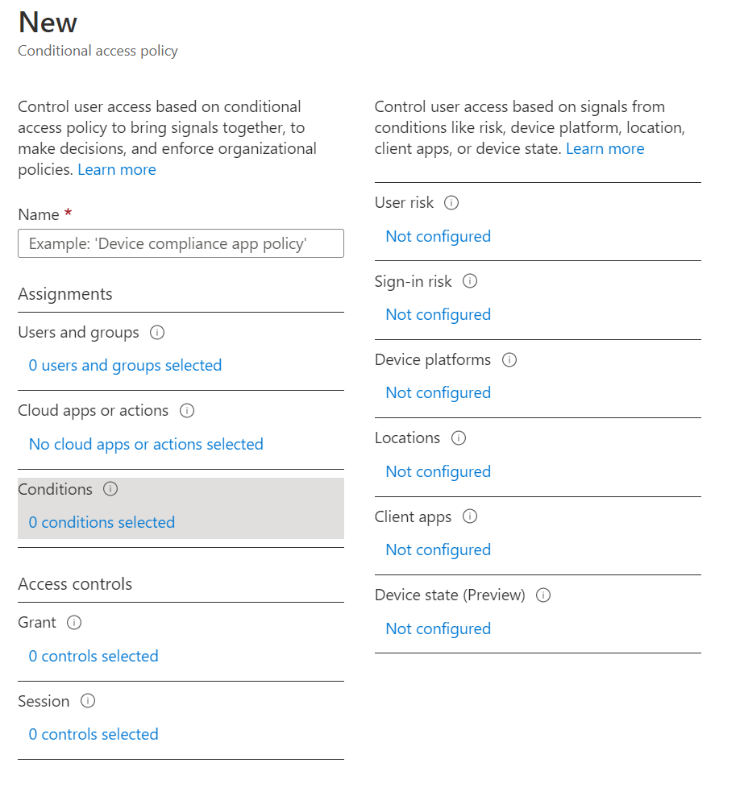
Azure Active Directory not only enables strong authentication, it provides Conditional Access to analyze signals, or conditions of users, devices, locations and automate and enforce resource access policies across the entire organization. Here is a screenshot showing the Azure AD Conditional Access Policy wizard:
User access control is based on evaluations of several factors, such as user risk, sign-in risk, type of devices and platforms used, locations from where access is requested, or device condition. After evaluating all signals, Azure AD Conditional Access can grant access, allow access on specific conditions, or block access to requested resources.
In case a legitimate user is requesting access to corporate resources — but the request originates from a compromised device or user sign-in risk signalizes impossible travel activity — a multifactor authentication challenge can be requested or user access can be denied.
The Azure AD Conditional Access is perhaps the most direct and picturesque example of the “do not trust anyone,” “verify explicitly” Zero Trust approach to security.
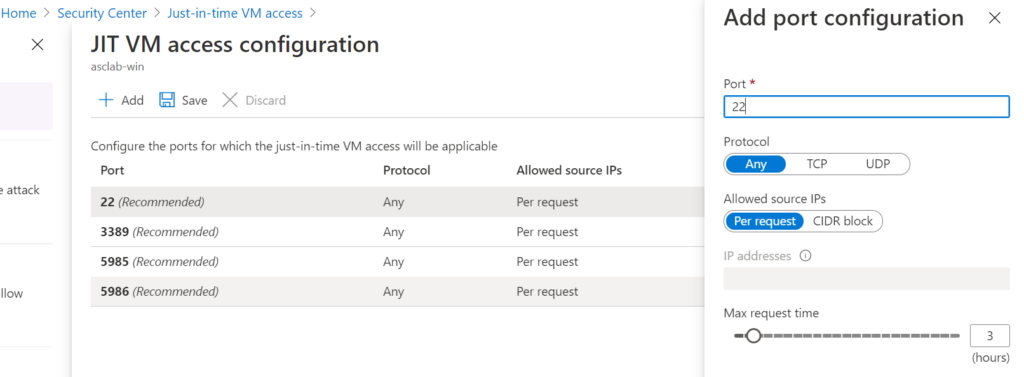
Just-in-time and just-enough administration are not reserved solely for the infrastructure Zero Trust approach but in protecting identities as well. Here is a screenshot showing how to configure ASC just-in-time VM Access:
Azure Security Center is a unified infrastructure security management system that provides security posture insight and actionable advice across Azure, on-premises, and third-party cloud workloads. Azure Security Center’s Cloud Workload Protection (CWP), or Azure Defender, enables intelligent workload protection across hybrid workloads and offers just-in-time virtual machine access. Customizable options include port, protocol, source IP addresses or CIDR blocks, and maximum request time allowed to access a virtual machine.
Azure AD Privileged Identity Management (Azure AD PIM), in contrast, controls JIT and JEA settings for Azure AD identities. It enables security administrators to limit users’ access to privileged roles, discover users with privileged role assignments, and perform privileged access reviews. Azure AD PIM provides just-in-time privileged access to Azure AD and Azure resources, enforces MFA to activate a role, use justification to follow and understand user activations, provides audit history, and more.
To protect endpoints and devices, to detect and remediate advanced attacks on endpoints, Microsoft Defender for Endpoint supports Microsoft Windows operating systems from Windows 7 to Windows Server 2019, Android, macOS, and Linux.
Many organizations struggle with shadow IT and with unknown and unsanctioned cloud applications. To discover applications used in corporate networks and to fight “the invisible and unknown enemy” — that is, attempt to control access to third-party applications or “shadow” cloud applications — IT departments need a cloud app security broker (CASB). Fortunately, Microsoft Cloud App Security is a CASB solution that tightly integrates with other products in the Microsoft portfolio. Its risk catalog contains more than 16,000 applications that are assessed over 80 risk factors that help IT departments and security professionals make the right decisions when assessing applications risk.
The products and features mentioned here are just the tip of the iceberg in a massive, possible Zero Trust security scenario. You might be using some or all products cited and, of course, you might use some others too, like Microsoft Endpoint Manager, Microsoft Defender for Identity, Microsoft Defender for Office 365, Data Loss Prevention (DLP) policies, BitLocker, Azure Policy, Azure Sentinel, Azure Blueprints, ARM templates, Azure DDoS Protection, Azure Web Application Firewall, Azure Firewall, Network Security Groups or Application Security Groups.
No matter what you use, ensure you follow the three basic Zero Trust principles: Assume breach, verify explicitly, and use least privileged access.
Featured image: Pixabay