Introduction
In my previous article I explained about implementing the Exchange Server 2010 Edge Transport Server in the DMZ as a means to fight the amount of spam that will enter your Exchange organization. And I have to say, the Edge Transport Server is quite effective in doing this. But when you have a larger organization you probably need multiple Edge Transport Servers. This means additional investments in hardware and software, and the Edge Transport Servers need to be managed as well.
Personally I think the anti-spam and anti-virus solution is a perfect candidate to host “in the cloud” and Microsoft has an offering for this. In the past this was known as “Exchange Hosted Services” but it is rebranded to “Forefront Online Protection for Exchange” or FOPE.
How does FOPE work?
In a traditional environment the MX records in public DNS point to your Edge Transport Server (or any other anti-spam and anti-virus solution of course) where the inbound messages are screened for spam or viruses. The remaining messages are sent to the actual Hub Transport Server and from there the messages are delivered into the various mailboxes.
When using FOPE, your MX record no longer point to your on-premise solution, but they point to the Microsoft Datacenters. Yes, as in plural because Microsoft has multiple datacenters for handling FOPE. And because of these multiple datacenters, Microsoft can achieve an uptime of 100%! The servers in the datacenters now do the anti-spam and anti-virus. When finished the messages are delivered to your on-premise Exchange environment.
When FOPE is not 100% sure that the message is really spam, it can place the message in quarantine. The intended recipient receives an e-mail from FOPE about the quarantine with the option to logon to the quarantine area. It’s now up to the user to decide whether or not the message is really spam. If not then the message can be delivered to the mailbox.
Besides e-mail filtering Microsoft offers message encryption, archiving, journaling and (intermediate) storage of messages. For example, when your on-premise Exchange Servers are not available for some period of time, the inbound messages will be stored in the Microsoft datacenters.
But the most interesting part in FOPE is (in my modest opinion) the anti-spam and anti-virus solution. It’s not only from a technical perspective, but also from a licensing perspective. When you have an Enterprise Client Access License (eCAL) for Exchange Server 2010, you automatically have a license for Forefront Online Protection for Exchange as well. So, you don’t have to invest in additional Exchange 2010 (Edge) servers and licenses and maintain the Edge Transport Servers, everything is taken care of!
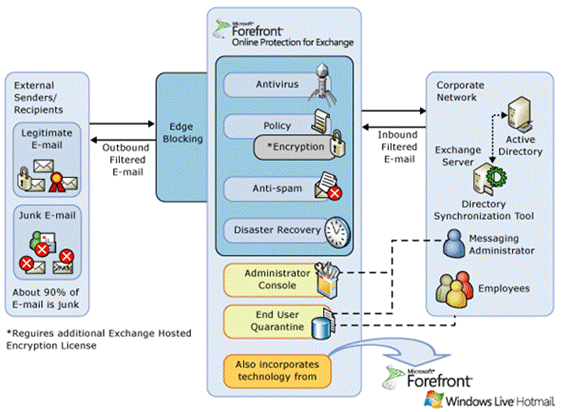
Figure 1: Overview of Forefront Online Protection for Exchange offering
The first step in setting up FOPE is the Management Tool. This is tied to your licensing environment, to activate FOPE you have to activate it in the license portal. You have to create a passport account (I usually use something like [email protected]) and connect this to the FOPE account in your license portal. As a consultant or a system administrator, this is the most difficult part.
For more information on how to activate this take a look at the Microsoft presentation that can be found here.
When activated (which can take a couple of days) you can logon to the FOPE portal.

Figure 2: The FOPE Administration Portal
In this management portal you can configure all components, like the IP address of the on-premise Exchange Servers (both sending and receiving), the accepted domains, quarantine options etc.
Suppose we want to add a domain, Exchangelabs.eu to the FOPE environment. The IP address of the sending and receiving Hub Transport Server is 83.161.229.15. The first step is to add this IP address to the FOPE portal for inbound traffic (where FOPE has to send mail to) and for outbound traffic (where the on-premise traffic is coming from).
The next step is to add our domain to FOPE. Click on Domains and select Add Domains in the action pane (on the right hand side). It is possible to enter multiple domains at one go, but we’ll add only one. Enter the domain name in the Add New Domains window and click Save.

Figure 3: The new domain needs to be validated first
Before the new domain can be activated it has to be validated. You can enter any domain you want in the FOPE portal, but the domains have to be validated before usage. And to be validated you need to use the Public DNS. Click on the Click here to validate this domain link. A pop-up appears with the DNS settings. You have to create a new CNAME record in the Public DNS that point to the Microsoft Online environment. FOPE uses this CNAME record to validate the authenticity of the new domain.

Figure 4: Enter a CNAME record which points to the Microsoft Online environment
After adding the CNAME record you can continue by clicking the Start button. But you have to check the TTL of your public DNS. It take from a couple of minutes up to few days (24 hours typically) for the change to take effect. So, now the new domain is validated but not yet activated.

Figure 5: The domain is validated, but not yet activated.
Next enter the IP Address of the on-premise Exchange environment. Click Edit in the IP Address Settings field and enter the IP Address. You can select the profile that was created in the first step – the so called Multi-SMTP profile. Strangely enough, you have to add the IP Address again for the Outbound IP Address, but here you cannot select the Multi-SMTP profile.
Now that everything is in place the domain can actually be activated. Click on the This domain is currently disabled message to activate the domain.

Figure 6: The domain is activated.
The domain is now ready for use, but you have to be careful. The changes need to be replicated across all Microsoft datacenters and this can take some time. I always use a couple of hours before changing the DNS settings.
So, after this time the public MX records can be changed, and the MX record now points to mail.messaging.microsoft.com. Microsoft takes care about load balancing between the different servers, so this is the only line we have to add.
When FOPE is used for outbound messaging (i.e. SMTP messages are sent from on-premise Exchange to FOPE and then delivered) the SPF records need to be changed as well. For SPF the following record can be used: v=spf1 include: spf.messaging.microsoft.com –all
To use FOPE for outbound messaging, the Send Connector needs to be changed from DNS to “Smart Host”, where mail.messaging.microsoft.com can be used as the Fully Qualified Domain Name (FQDN) to send the messages to.

Figure 7: The Exchange Send Connector now uses FOPE as smart-host
For additional security, the receive connector on the on-premise Exchange servers can be changed to accept SMTP messages only from FOPE. Since the MX records point to the Microsoft datacenters, no messages from other SMTP hosts should enter the on-premise environment directly. If they do, there’s something wrong.
Conclusion
Forefront Online Protection for Exchange (FOPE) is a perfect candidate for cloud integration. When using FOPE all messages are delivered to the Microsoft datacenters, they are scanned for malware and the clean messages are delivered to your on-premise Exchange environment. No need anymore for implementing Edge Transport Servers or any other 3re party anti-malware solutions. Not only will it save you money, it also lowers you administration costs. My personal opinion: I always recommend using FOPE instead of an on-premise anti-malware solution. It’s perfect. In my next article I’ll discuss more about the integration between FOPE and on-premise, the reporting possibilities and the quarantine options of FOPE.
If you want to give it a try, navigate to the Exchange Hosted Services website and request a 60 day trial license!

