Introduction
In order to manage and protect the data in the Exchange server a number of different administrative permissions are required. Exchange uses both the Windows access control model, made up of Access Control Lists (ACL) and a hierarchal permission structure.
Exchange Hierarchal Levels
Exchange provides three levels at which you can apply Access Control Lists (ACL’s) and administrative permissions. The three levels are:
- Organization Level – Includes all Exchange Administrative Groups and the Exchange servers they contain. This is the top level and users with administrative permissions at this level can manage the entire Exchange organization.
- Administrative Group Level – This level includes all Exchange servers in the Administrative group. An administrative group can be compared to an Active Directory domain, where the domain is the administrative boundary.
- Server Level – The lowest level is the server level and restricts administrative control to the specified server.
With this approach, permissions flow from top to bottom and allow for fine tuning of permissions on all objects. Through the use of ACL’s permissions can be applied granularly allowing, or denying, access to specific objects.
Access Control Lists
Older versions of Exchange server (5.5 and earlier) used its own method for access control using permissions that were stored in the Exchange directory store. With the release of Exchange 2000, access control was updated to use the Windows access control method. Now all objects such as mailboxes and public folders have an ACL to link Access Control Entries (ACE) and Security Identifiers (SID). The major benefit to this model is more granular control and the ability to control inheritance of permissions from parent containers. Figure 1 shows a typical ACL for an Exchange server.
Figure 1: Exchange Server ACL
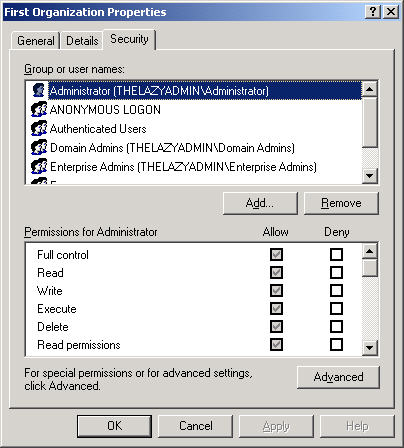
One thing to note is that by default, the ACL for the Exchange organization and Administrative Groups are not displayed. In order to change this, you need to edit the following registry key.
HKCU\Software\Microsoft\Exchange\ExAdmin
Create a REG_DWORD called ShowSecurityPage and set the value to 1 and restart the Exchange System Manager (ESM). You will now see the Security tab when viewing the properties of the Exchange Organization or an Administrative Group (see Figure 2).
Figure 2: Organization Security Tab
Administrative Delegation
In addition to ACL’s, there are also three predefined administrative roles you can apply to a user account. Each role is a set of rights required to perform specific actions on an Exchange server. These roles are assigned with the Delegation of Control Wizard. Before we take a look at that wizard, let’s review each role.
- Exchange Full Administrator
- Exchange Administrator
- Exchange View Administrator
The Exchange Full Administrator is the most powerful of the administrative positions and should be assigned with great care. The first time you run Forest Prep you are prompted to select an account that will become the first Exchange Full Administrator (see Figure 3). This permission allows for full control over all objects as well as the right to delegate control to other users. This level of rights is required to install the first Exchange server into the organization and remove a server running Site Replication Service (SRS). Accounts with this role should also be added to the Local Administrators group on the Exchange server.
Figure 3: Create Exchange Full Administrator
The Exchange Administrator position is similar to the Exchange Full Administrator with the exception that these users cannot delegate control over any objects. They can still mount and dismount stores, add or remove servers from an Administrative Group, or install an Exchange service pack. Accounts with the Exchange Administrators permissions must also be made Local Administrators on the server and this position is best assigned to users performing the day to day management of the server.
Lastly the Exchange View Administrator is the lowest level of the three. This position does not have any rights to change anything and only allows for viewing of objects in ESM. You might assign this permission to junior admins who need to monitor the server, but would refer any changes that need to be made to higher level administrative staff. The following chart describes which level of permissions is required for certain tasks.
Task
Permission Level
Initial run of ForestPrep
Enterprise and Schema Administrator
Subsequent runs of ForestPrep
Exchange Full Administrator for the Exchange Organization
Run DomainPrep
Domain Administrator
Install/Upgrade first Exchange server in Organization
Exchange Full Administrator for the Exchange Organization
Install/Upgrade first Exchange server in domain
Exchange Full Administrator for the Exchange Organization
Install/Upgrade first Exchange server in Administrative Group
Exchange Full Administrator for the Exchange Organization
Install/Upgrade additional Exchange servers in domain or Administrative Group
Exchange Full Administrator for the Administrative Group
Install Exchange virtual server when clustering
Exchange Full Administrator for the Exchange Organization
Upgrade Exchange 2000 Bridgehead Server to 2003
Exchange Full Administrator for the Exchange Organization
Add or Remove Exchange 2003 SRS
Exchange Full Administrator for the Administrative Group
Table 1
Delegation of Control Wizard
The Delegation of Control wizard can be run at the organization level, or at the administrative group level and your first step would be to determine which level you wish to delegate access to. To start the Delegation of Control Wizard, right click on the organization or the administrative group and select Delegate Control. Click next to get past the welcome screen and begin delegating control.
The first screen will show a list of users and the role they hold. By default, only the account specified during the ForestPrep will be listed and it will hold the Exchange Full Administrator role. To delegate control to other accounts, click Add and browse for the user account in Active Directory. Figure 4 shows a listing of user accounts with various roles delegated.
Figure 4: Delegated Control
It is best practice to create security groups and delegate control to the security group. This makes management much easier and ensures that the user accounts have the proper administrative rights. A little knowledge is a dangerous thing, and even more dangerous is a little knowledge with too much control!
The last screen of the Delegation of Control wizard will allow you to verify the tasks that are about to be performed and allow you to go back and make any changes. If you need to remove a user account or a group, or change the rights delegated to a user or group, simply highlight the user or group and press the Edit or Remove button. Once you click finish, the permissions are applied.
As with the ACL’s, delegated permissions also flow down to the administrative groups in the organization. If you delegate control at the organization level, those permissions will trickle down to the administrative groups in the organization, and when you run the Delegation of Control wizard at the administrative group level, you will see the users and groups that have been delegated control, the role they have been delegated and if they inherited the rights from the organization (see Figure 5).
Figure 5: Inherited Delegation
The Delegation of Control wizard is the preferred way to assign permissions to manage Exchange. Best practice would be to use this wizard and not modify the ACL’s but this is not always possible. If you must change the permission on an object, do so with caution and be sure to document any changes.
The following chart shows the permissions each role assigned by the Delegation of Control wizard.
Rights
Exchange Full Administrator
Exchange Administrator
Exchange View Administrator
Read Properties
Allow
Allow
Allow
Write Properties
Allow
Allow
–
List Objects
Allow
Allow
Allow
Create Top Level Public Folder
Allow
Allow
–
Create Public Folder
Allow
Allow
–
Add Public Folder to Administrative Group
Allow
Allow
–
Modify Public Folder ACL
Allow
Allow
–
Modify Public Folder Deleted Items Retention
Allow
Allow
–
Modify Public Folder Expiration
Allow
Allow
–
Modify Public Folder Quotas
Allow
Allow
–
Modify Public Folder Replicas
Allow
Allow
–
Remove Public Folder from Administrative Group
Allow
Allow
–
Read Metabase
Allow
Allow
–
Open Send Mail Queue
Allow
Allow
–
Administer Information Store
Allow
Allow
–
View Store Status
Allow
Allow
–
Create Named Properties in Store
Allow
Allow
–
Change Permissions
Allow
–
–
Take Ownership
Allow
–
–
Send As
Deny
Deny
–
Receive As
Deny
Deny
–
Table 2
Once you have delegated control over an organization or an administrative group you can view the ACL and see that these permissions have been applied. Figure 6 shows the ACL for the Exchange Administrators group which has been delegated the Exchange Administrator role.
Figure 6: Delegate Permissions
Conclusion
As you can see controlling administrative permission is quite easy in Exchange 2000 and 2003, much easier and more powerful than previous versions of Exchange. The granularity that ACL’s bring, as well as the ease of assigning permissions with the Delegation of Control wizard should allow you to control who has access to what.
How to Regain Access to an Exchange Server 2003 Organization
http://www.msexchange.org/tutorials/Regain-Access-Exchange-Server-2003-Organization.html
ForestPrep and DomainPrep Explained in Detail
http://www.msexchange.org/tutorials/Forestprep-Domainprep-Explained.html