In this issue
ASK OUR READERS: Windows 10 screen lock settings not working (more responses). ASK OUR READERS – WFH security and USB flash drives (new question). MAILBAG. Extreme surveillance of tech workers. DocuSign phishing scam? Time servers hit by DDoS attack. TIP: Safeguarding your most precious passwords. FACTOID: Is a university diploma worth the paper it’s printed on? Plus lots more — read it all, read it here on WServerNews!

Big Brother may be watching you as you work at the office. Photo by Gerax Sotelo on Unsplash
Ask Our Readers: Windows 10 screen lock settings not working (more responses)
Two issues ago in WServerNews we published the following question from reader named Andrey who works as the Director of Technology for a company:
I’m having a heck of a time with Windows Screen Lock settings. Tried just about everything I can think of. Power Settings, etc. It’s very inconsistent. It appears that “too much’ activity is happening for the Windows 10 1909 OS to lock the screen. I updated the machine to Windows 10 20H2 and it locks as long as no one is touching the mouse or keyboard unlike the 1909… Basically the computer will not lock on the usual 10 minute timer. This is a Win 10 1909 OS. We determined that it appears that Microsoft defines an IDLE Lock as CPU and GPU have to be under a certain threshold. In the past it seemed that it would be triggered simply from no keyboard or mouse activity. I tried updating to Win 10 20H2 OS on this same laptop and it started locking very consistently even with high CPU usage as long as the mouse or keyboard isn’t touched. The other issue is we tried adjusting the power settings to force the lock and it appears to trigger the network disconnect at the same time when it locks, dropping connections to applications, etc. Essentially, it appears that the simply Screen Lock settings don’t work in Windows 1909.
In our last issue we published a few suggestions from our readers and since then several more readers have contributed their thoughts on the matter. Jan Hedström from Sweden provided the following recommendations:
If the problem is showing on a standalone PC, try this:
- Run gpedit.msc as administrator
- Choose Computer configuration – Windows Settings – Security Settings – Local Policies – Security Options – Interactive logon: Machine inactivity limit – X seconds (in the “Local Security Setting” tab)
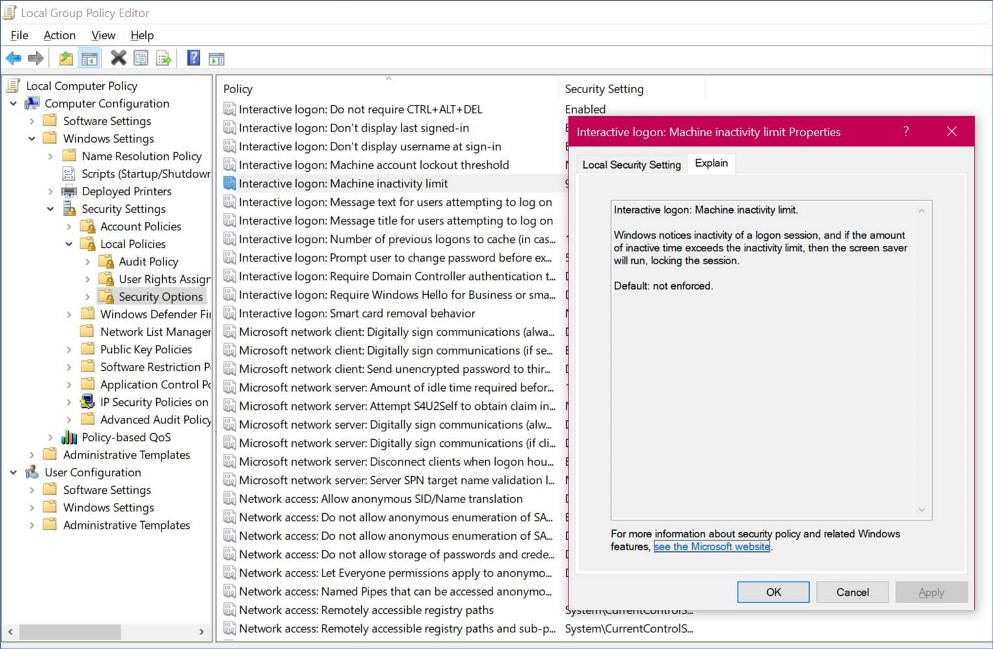
Hopefully this will override all other screen lock settings
If the suggested solution above doesn’t help, check Computer configuration – Administrative Templates – System – Power Management (screenshot from Sleep Settings, but check all settings under Power Management and disable or enable as needed to make sure all users settings will not have undesired effects on the screen lock and continuous operation):
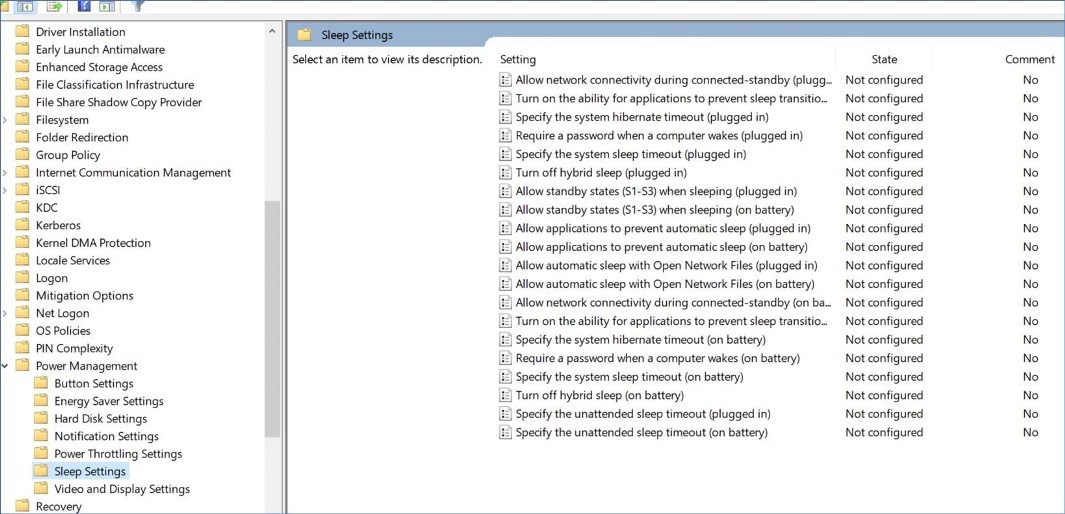
Screenshots are from Windows 10 Enterprise 21H1 Build 19043.1023.
Another reader named Don Kiiskila shared his own experience with enforcing lock screens on Windows computers:
Regarding the “1909 lock screen” issue, I’m a system admin for some casinos, and I can definitively tell you that on *any* version of Windows 10 (or 7), Group Policy item “Machine Inactivity Timeout” will enforce it. It can be a local as well as domain level policy. I know, because I implemented it due to government regulations and recommendations. I have hundreds of machines on 1909 that lock properly even with high cpu usage from virus, patch, and vulnerability scans going on all the time. They are correct however that mouse and keyboard activity will stop the inactivity timer (which is what it looks for), but high cpu/gpu will not affect inactivity timer.
If any other readers have thoughts on this matter please email us your suggestions.
Ask Our Readers – WFH security and USB flash drives (new question)
A reader named Manoj Gawankar sent us the following questions asking for help from our readers:
Hi All. What is the best practice you’re applying to protect USB access to PC and Laptop in WFH situations? Also can you help to get the best tool to provide USB Pen drive encryption with password protection that we can provide the user rather than allowing USB access to the laptop in a cost effective way.
I asked Manoj to clarify whether by “USB access” he meant keeping the computers of WFH employees secure against attacks through corrupted USB flash drives, and whether his question about encryption concerns companies that give USB sticks having sensitive business data stored on them to their employees who are working from home. He replied and confirmed as follows:
Yes Mitch. Like some time user not connect VPN so policy not get updated on user laptop for USB Device Blocking.. And for exceptional use we can provide them USB pen drive to move data so how can we do Encryption on pen drive and password protect when it connect to other laptop.
What do our readers recommend and/or use for these purposes? Email us your suggestions, thanks!
Got questions? Ask our readers!
WServerNews goes out bimonthly to almost 200,000 IT pro subscribers worldwide! That’s a lot of expertise to tap into. Do you need help with some technical problem or are looking for expert advice on something IT-related? You can Ask Our Readers for help by emailing us your problem or question. Do it today!
Mailbag
In our last issue I mentioned a solution called MIRACL that replaces passwords and 2FA with SMS with a simple PIN that apparently provides secure passwordless authentication. This drew a couple of comments from our readers.
PIN # is probably a weak point. Most people will choose a PIN # that is something known to them that they can remember easy, such as part of their phone number, a birthday, an anniversary (now you can tell people not to do that and choose a random number, but many or even most, wont. And they still might write it down somewhere). For MFA (e.g. for M365/AzureAD/Hybrid join or other purpose like VPN) then use push notification. Never ever use SMS. Better than PIN is to use biometrics to login. FIDO2 devices is very secure option. –Darren Lewis
Well I guess there’s always an element of user education needed for any form of authentication solution.
One of the most interesting “do away with passwords” idea I’ve read recently is no password at all! Safe? Yes! Secure, Quick, Reliable Login (or SQRL) by Gibson Research Corp, and Steve Gibson, author of the wonderful SpinRite 6 disk analysis and repair tool. A website operator deploys a SQRL login on their page, and by scanning or clicking on the QR-Code, you’re logged in, with the minimal amount of information necessary for you to use the service. After authenticating, the website operator may choose to ask for more information to perform business-related tasks, but for simple “are you a human” and “are you unique”, that’s all that is required! Steve gives a better primer on his site, but it’s really well thought-out, and it’s starting to gain traction. –Daniel Bragg
Have any of our readers tried SQLR or are using it? We’d love to hear from you about it.
And in our last issue the lead photo showed robots assembling an automobile and the caption under it said: “Automation can make your life easier. Unless you’re a robot of course, in which case you’re forced to work 24x7x365. What a life.” This drew the following comment from Bruce Anderson:
So… what day every four years do the robots get off? Is that when we can use our defense against SkyNet?
Hmm, another “rights of robots” advocate. Hmph.
And shouldn’t it be 24x7x365.25?
It’s a little more complicated that than that (Wolfram).
Editor’s Corner
The latest ruminations on tech from our cud-chewing Editor…
Extreme surveillance of tech workers
An article in Nikkei Asia really grabbed my attention this morning:
China’s tech workers pushed to limits by surveillance software (Nikkei Asia)
The writer talked with an IT engineer for a gaming company based in Shanghai and described how the company was using software called DiSanZhiYan or “Third Eye” to continually monitor the browsing activity and record chats of employees. The software then generated weekly reports of suspicious behavior which were sent to managers. You can find more info about the capabilities of this software here (in Chinese) or using Google Translate (for English).
How many of our readers who work in corporate environments experience (or implement if you’re a manager) some measure of workplace surveillance? How do you feel about it? I’m somewhat undecided.
On the one hand, I think I would feel stressed if I was watched constantly to make sure I perform. And I think such stress would cause me to perform more poorly instead of better. On the other hand, surveillance in the workplace of course is as old as “going to work” is itself. Egyptian pharaohs likely had their priestly class oversee slave workers constantly, urging them on with whips. Factory workers used to punch their timecards when they entered and leaved the building. And security cameras are used not just to monitor workers but to deter break-ins and theft.
One issue that I think may be behind the increase in use of workplace surveillance software like Third Eye is the increasing mobility of tech workers allowing them to move between jobs easily. The whole idea of employee loyalty seems to be a thing of the past nowadays, so it’s no surprise that the boss will want to know when a worker has been browsing job boards or chatting with recruiters during lunchtime instead of playing Candy Crush. One can argue that declining employee loyalty is caused by the increasing exploitation of workers, especially in the tech industry. But I don’t think it’s that simple, there seems to be a certain karma in the universe concerning give and take in loyalty.
Anyways, this issue has got me thinking again about the blessing and curse that modern computing technology brings us as individuals, as societies, and as inhabitants of this planet. I’m increasingly leaning towards believing that technology is *not* simply neutral, that it doesn’t just depend on the character of the person using it. Some scientific and technological advances may be inherently helpful (mostly) but some others may actually be intrinsically harmful. Even something as pure as Mathematics has its dark side. In fact I remember reading once somewhere that the ancient Babylonians developed mathematics primarily as a tool for keeping close track of their workers — and making sure that taxes were paid.
What do our readers think about all this? Email me.
DocuSign phishing scam?
It’s getting harder and harder to recognize phishing emails when they end up in your Inbox. I’ve used DocuSign as an electronic signature mechanism many times in the past, but I haven’t had occasion to use it for several years now. But last week I received the following email:
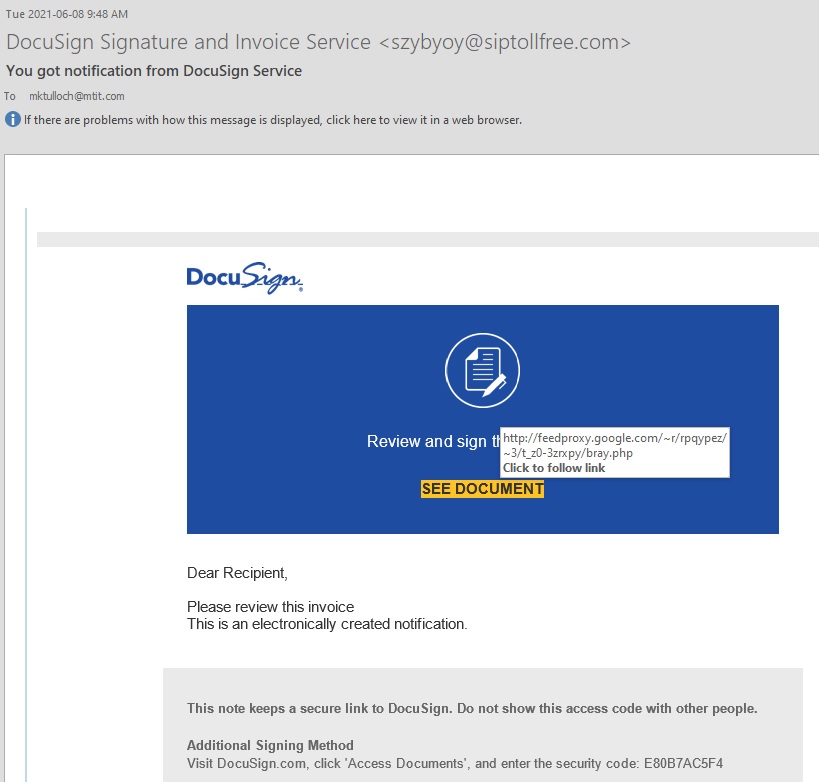
There are several “tells” that this is a phishing email, the most obvious being the weird address of the sender near the top. A whois search immediately indicated that siptollfree.com is a domain parked free of charge with NameSilo.com. And hovering my mouse pointer over the See Document link shows a suspicious URL.
But it almost fooled me when I first saw the email. Have any other newsletter readers been receiving similar emails like this? What steps do you take when you think an email you receive might be a phishing attempt? Email me your comments so we can benefit from the collective experience of our IT pro community.
Time servers hit by DDoS attack
Accurate network time is important for enterprise software environments that use Active Directory. Many of us utilize time.nist.gov as our authoritative source of network time simply because this NTP source is hard-coded in our network time appliances. In light of this you should know that it appears that the name servers of nist.gov seem to have been indirectly under DDoS attack earlier this week. This was first alerted to me by a colleague who runs an ISP who noticed that the NIST RPKI Monitor site mostly couldn’t be reached for several days, apparently because the NIST name servers were being flooded with DDoS packets. This not only prevented domain controllers from receiving time from time.nist.gov but also ended up causing problems for recursive DNS lookups.
For a recent TechGenix article I wrote concerning the importance of network time for your datacenter, see here. And for a helpful source of info about how to protect your organization from a DDoS attack, see this article on Senki.
Got comments about anything in this issue?
Email us! We love hearing from our readers!
Please tell others about WServerNews!
Enjoy this issue of WServerNews and feel free to send us feedback on any of the topics we’ve covered — we love hearing from our readers! And please tell others about WServerNews! It’s free and always will be free — and they can subscribe to it here. Thanks!!!
Tip of the Week
>> Got any IT pro tips you’d like to share with other readers of our newsletter? Email us at [email protected]
Safeguarding your most precious passwords
While many of us in IT use a password manager to keep track of the many different passwords we need to remember for working and living in our online world, there are sometimes a few passwords you want to do a bit more to protect against compromise. Like the password for accessing your bank account or your investing portfolio for example. One interesting trick that was suggested to me by a colleague for managing such passwords is to split each password into two parts and store one half of them in your password manager while memorizing the other half of each password. That’s a pretty cool trick! What do / you think?
Admin Toolbox
>> Got any admin tools or software you’d like to recommend to our readers? Email us your recommendations!
MailStore Server is an email archiving solution that keeps business-critical information residing in emails available and retrievable over the long-term:
Conquer the best of both worlds with RavenDB 5.2, a NoSQL Document Database. Enjoy OLTP ACID Transactions, OLAP ETL for Analytics, and Grafana integration for visualization. Set up a live demo today.
dtSearch®-Instantly Search Terabytes. Doc. filters for popular file types, emails, databases & web data; 25+ search options; Win/Lin/Mac C++/Java/.NET Core APIs; Azure/AWS FAQs.
Simplenote is a simple cross-platform note taking app with cloud-based syncing:
GPU-Z -is a free all-in-one GPU monitoring tool:
https://www.techpowerup.com/gpuz/
HWMonitor is a hardware monitoring program that reads PC systems main health sensors : voltages, temperatures, fans speed:
https://www.cpuid.com/softwares/hwmonitor.html
Factoid – Is a university diploma worth the paper it’s printed on?
Our previous factoid and question was this:
Fact: FTP is 50 years old.
Question: How many of our readers still use FTP? When was the last time you used it, and for what?
We received several responses to this including the following:
We still use FTP for our offshore developers to transfer code. –Bruce Anderson from Minnesota, USA
FTP is alive, well and my livelihood as printer/mailer depends upon it. We haven’t used Windows ftp proper for decades, rather relying upon Progress/Ipswitch ws_FTP server to power our available SFTP/SSH (port 22) and FTPS (port 990) connections. We dropped plain text port 21 ftp only a few years ago, after introducing the product’s WebTransfer module (https) for the more graphically and less technical users. –Ramon Abad from New York, USA
I still use FTP, but only in a tightly controlled network. Because of a corporate GPO, my work laptop doesn’t support older versions of TLS, and my old home NAS can’t be upgraded to 1.2, so file sharing between that particular laptop and the NAS is done via FTP. It’s a mixed environment – I do have an office in our data center, but I can work from home half the time. My NAS serves both sides of my life – it’s my main backup for all the computers at home, streams media to my entertainment center, and acts as the second backup for my work laptop (the only device in my network with the TLS issue). And since I’m a belt and suspenders kinda guy, it gets backed up to a couple of large drives that are air gapped when they’re not actively involved in a backup. One of these days I’ll modernize and replace the old NAS hardware, but I’m kinda like the mechanic who keeps an old clunker running with duct tape and baling wire. –Jim Ruby
I think most of us who work in IT are “belt-and-suspenders” kinda guys and gals.
Now let’s move on to our next factoid:
Fact: Google plans to disrupt the college degree-granting mill.
Source: https://www.inc.com/justin-bariso/inside-googles-plan-to-disrupt-college-degree-exclusive.html
Question: How many readers who hold university degrees if you could go back in time and become 18 again would NOT go to university? Is there any real value today in getting a university degree? Email us your answer and we’ll include it in our next issue!
Subscribe to WServerNews!
Subscribe today to our WServerNews newsletter and join 200,000 other IT professionals around the world who receive our newsletter! Just go to this page and select WServerNews to receive our monthly newsletter in your inbox!
Conference Calendar 2021
NOTE: Conference dates and locations (real/virtual) are subject to change
Microsoft Inspire — July 14-15 (virtual)
https://partner.microsoft.com/en-US/inspire
Black Hat USA — Jul. 31-Aug. 3 in Las Vegas
https://www.blackhat.com/upcoming.html#usa
Open Source Summit — Aug. 4-6 in Vancouver, Canada
https://events.linuxfoundation.org/open-source-summit-north-america/
DEF CON 29 — Aug. 5-8 (location TBA)
European Cloud Summit — Sept. 27-29 in Frankfurt, Germany
https://www.cloudsummit.eu/en/
Open Source Summit — Sept. 29-Oct. 1 in Dublin, Ireland
https://events.linuxfoundation.org/open-source-summit-europe/
VMworld — Oct 5-7 (virtual)
https://www.vmworld.com/en/index.html
Black Hat Europe – Nov 8-11 (virtual)
https://www.blackhat.com/upcoming.html#europe
Podcast Corner
Backing up PowerApps with April Dunnam (RunAsRadio)
The Future Of Networking With Nick McKeown (Heavy Networking)
https://packetpushers.net/series/weekly-show/
Spectrum Analysis (Clear To Send)
Banks to embrace Yubikeys for customers (Risky Business)
https://risky.biz/netcasts/risky-business/
Microsoft Taking Down Hackers and Some News (Microsoft Cloud Show)
http://www.microsoftcloudshow.com/podcast
New on Techgenix.com
How to create and use the Microsoft 365 apps inventory feature
The new Microsoft 365 apps inventory feature is a powerful tool to help admins gain valuable insight into their Office 365 deployments.
https://techgenix.com/microsoft-365-apps-inventory-feature/
AWS’s serverless strategy has containers front and center
AWS’s blending the worlds of serverless and containerization has resulted in a dazzling array of options for every use case from simple to complex.
https://techgenix.com/aws-serverless-strategy-containers/
Review: CodeTwo Email Signatures for Office 365
CodeTwo Email Signatures for Office 365 is a powerful tool allowing you to centrally manage email signatures across an organization. Here’s our review.
https://techgenix.com/review-codetwo-email-signatures/
Concerned about Kubernetes security? Check out these free tools
Worried that your Kubernetes clusters could suffer breaches because of over-permissive states and security misconfigurations? These free tools can help.
https://techgenix.com/free-kubernetes-security-tools/
Email defense: Fighting continuous compromises, endless challenges
Organizations are under constant barrage from cybercriminals on numerous fronts, but an email defense policy is a good start to keeping you secure.
https://techgenix.com/email-defense/
Fun videos from Flixxy
Worlds Biggest Mountain Bike Jumps
Nico Vink pushes the limits of freeride mountain biking at the Darkfest 2020 in Stellenbosch, South Africa.
https://www.flixxy.com/worlds-biggest-mountain-bike-jumps.htm
‘CopterPack’ Backpack Helicopter
The CopterPack – an electric backpack helicopter with a self-levelling autopilot.
https://www.flixxy.com/copterpack-backpack-helicopter.htm
Breathtaking Drone Flying Through The Mall Of America
This video of a drone flying through the Mall Of America in Bloomington, Minnesota really is a masterclass in cinematography.
https://www.flixxy.com/breathtaking-drone-flying-through-the-mall-of-america.htm
Snow Cloud Avalanche
A ‘cloud avalanche’ near the Kapuche Glacier Lake in the mountains of Nepal. That scene is extremely rare, it’s lucky enough to see it once in a lifetime.
https://www.flixxy.com/snow-cloud-avalanche.htm
More articles of interest
Run Kubernetes at the edge with these K8s distributions
The idea of edge computing is not as far off as it once was. Evaluate several ways to bring Kubernetes to the edge, and when an organization should use each approach.
How to fix 8 common remote desktop connection problems
When the connection between a desktop and its host fails, it’s time to do some remote desktop troubleshooting. Check firewalls, security certificates and more if a remote desktop is not working.
Explore multiple Office 365 PowerShell management options
Why use PowerShell for Office 365 and Azure? In some instances, it’s the only way to tap into some of the hidden management settings in these Microsoft cloud products.
Colocation in disaster recovery: Everything you need to know
Colocation is an important DR strategy and it’s a vital resource for ensuring mission-critical systems and data files can be securely protected and available when needed.
Send us your feedback!
Got feedback about anything in this issue of WServerNews? Email us!
