It is almost impossible to find a company that does not have at least one social media platform. Facebook, Twitter, Instagram, and LinkedIn, especially, are key for most businesses and they are the way that many companies present themselves to the public. But the security on those social media sites should be high for any company. Larger organizations, where more than one person has the right to publish information on social media, must be very vigilant about what is posted and who can post. In this article, we are going to show you how to protect your enterprise social media using Azure Active Directory SSO. This can help you provide your employees with access to your social media sites without sharing the actual password, and we are going to tie them to Active Directory accounts.
Taking advantage of Azure Active Directory, you can protect your enterprise social media accounts and get these following benefits out of the box:
- Ability to enable multi-factor authentication.
- Provide conditional access (if license permits).
- Never share the real password of your social media sites with employees.
- Employees come and go, and we can handle that with Active Directory accounts.
- A new employee can be associated with your social media accounts and start working right away.
- Monitor and track logon access to social media access.
- We can enable social media for an entire department without sharing passwords.
Our scenario
Our company Infralab.org is building its social media base on the Internet, and we have the on-premises Active Directory synchronizing with Azure Active Directory. We have a marketing department with a few users who are responsible for managing all media content of our organization.
First, we are going to create a mailbox with a strong password. We will associate the email [email protected] with this mailbox. We will use this email to create a secure password on all social media sites (we are going to use the most complex passwords available for each social media site), and this account should be accessible (if necessary) only by a few users who need access to emails on that mailbox.
Second, we will create a group called MyApps-Social and add the members who require access the social media, who will be a member of that group.
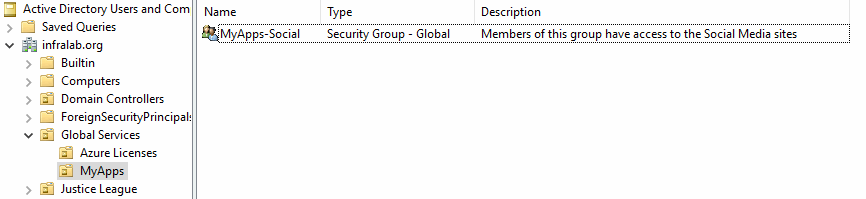
After completing this article, we are going to save all those complex passwords and their sites on a piece of paper and we are going to place it in a sealed envelope, which should be left in a corporate vault or given to the business owner. The goal here is to forget about those passwords and only rely on Azure Active Directory to access that social content.
One thing we should be aware of is that social media allows reset of passwords, so we should add telephone numbers and other ways to validate the social media accounts. In the case of a larger company, we can use data from a director or vice president-level executive to guarantee that a regular user does not reset the password and use that credential to post information.
Managing Facebook, Twitter, Instagram, and LinkedIn
All these applications require the same level of configuration, so we are going to configure Facebook. We need to apply the same steps for the other social media sites.
Protect your enterprise social media accounts: Let’s begin
Logged on to Azure Portal, click on Azure Active Directory, and on the new blade click on Enterprise Applications. In the blade on the right side, click on New Application.
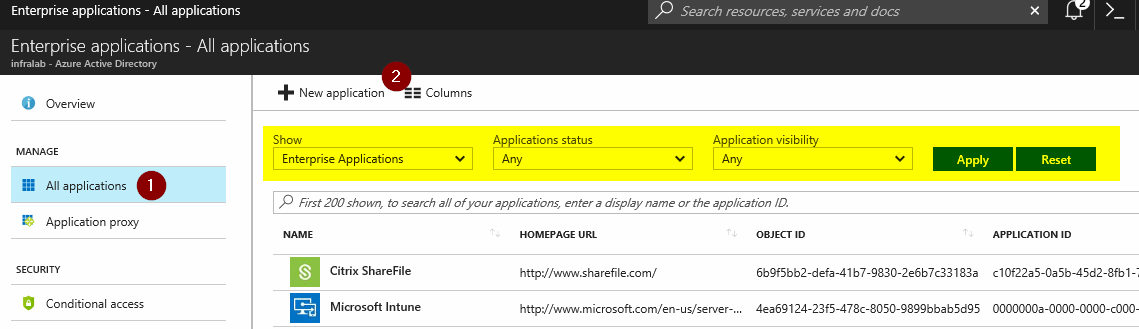
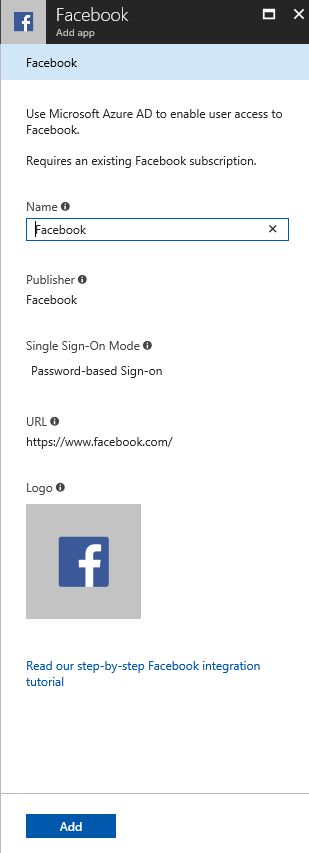
In the new set of blades, on the right side we can select by category, however, we are going to type in Facebook and select from the list below. A new blade with basic information about the app is going to be listed. We need to pay attention to the Single Sign-On Mode. That definition dictates what we can configure for that given app. Click on Add.
After adding the Facebook App, we will have a blade just to configure Facebook and we will be redirected to the Quick Start item, which containes the sequence of steps that we should perform to get the app up and running.
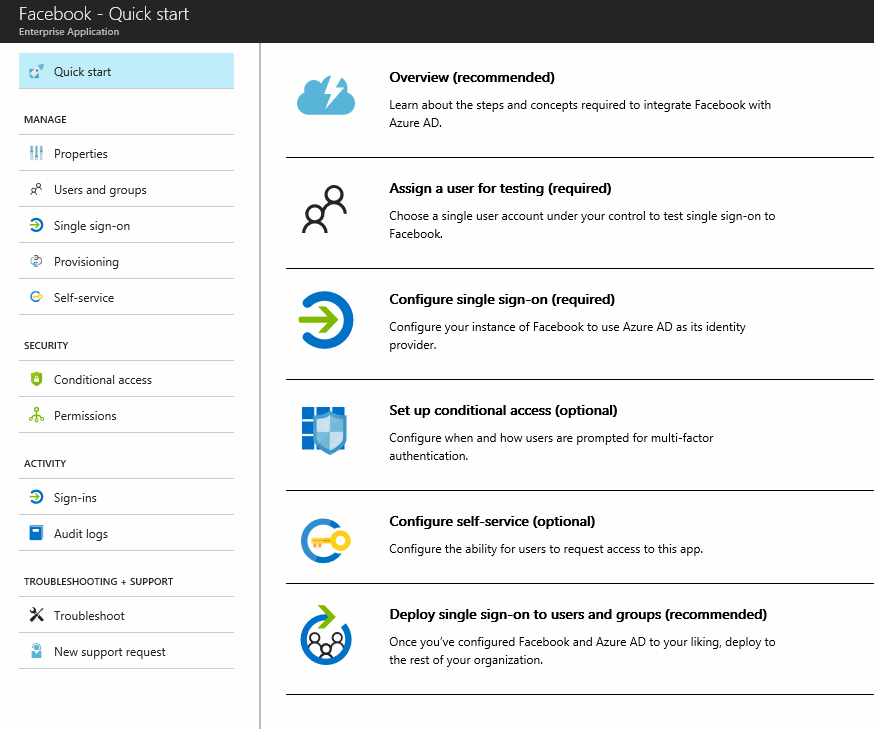
The first step is to click on Single Sign-On, and then select Password-based Sign-on, and then click Save.
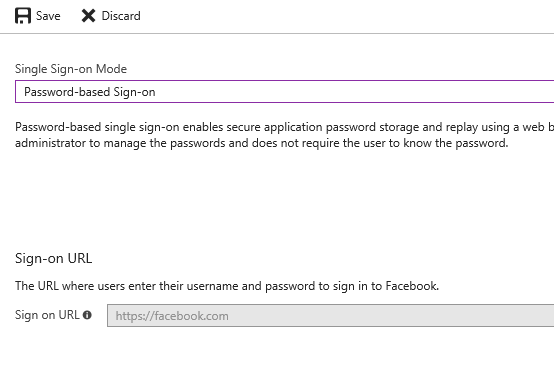
You may have noticed that we haven’t entered credentials yet, so at this point, there is no way for this app to understand that it needs to connect with our company’s social credentials. Let’s click on Users and groups item on the left blade, and then click on Add user.
In the new blade, the administrator must define two options: first Users and Groups, and here we will select the Active Directory group that we created at the beginning of this article, which is the group called MyApps-Social.
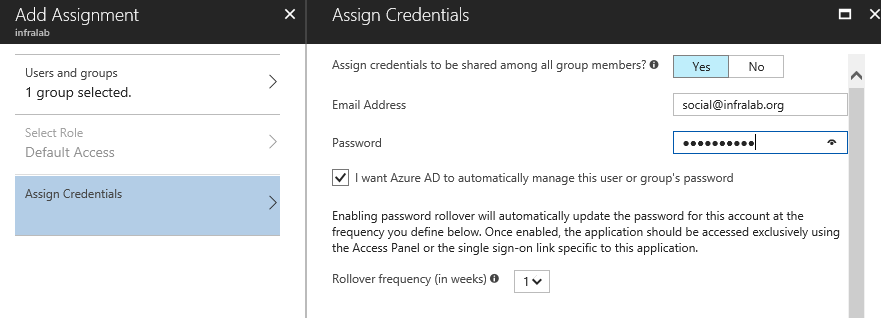
As soon as we select the group from the list, Assign Credentials will appear on the left side. Click on it, click on Yes, and that will make that credential available to all members of the group (not the password, just the credential — the user will not know the password to access Facebook or any given application).
We have a nice security feature here: We can force Azure AD to manage the password on the application, and we can define the number of weeks to update the password on the given application. In this example, we are configuring every week. Click on OK and then Assign.
Note: For this specific application, the password saved on the envelope won’t be used because it will be changed by Azure AD.
End-user experience
For now, we have a single user as part of the group MyApps-Social, and when that user logs on, we will have an icon for each one of the apps that we have just published.

Let’s use Instagram, for example. After clicking on the icon, the authentication process will happen behind the scenes and for the end user the experience will be direct access to the Instagram account, and the same experience is valid for all other applications.

It will also be the same experience when using MyApps app on a mobile device, and from there the user can open the apps and publish social media content.

Managing users on the social media portals
If we have a new person in the department who needs access to social media, then our only tasks would be to add the new user to the AD group.
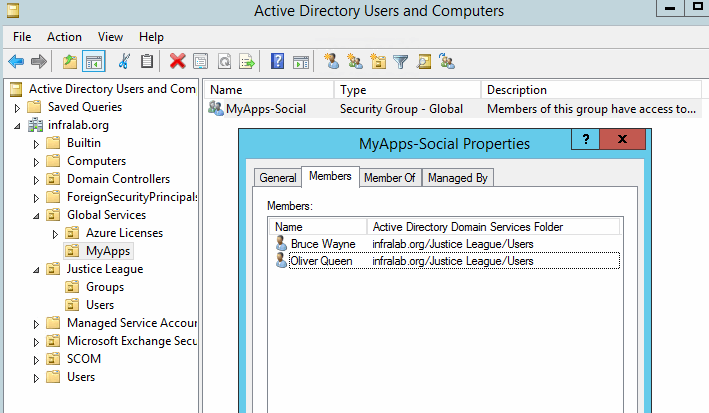
If we need to revoke access to the social media to any given user, just remove the user from the same group. After that, he or she won’t be able to connect to any site. The same applies if the user is disabled from Active Directory; the access to the social apps will be disabled as well.
Managing audit, sign-ins, and app usage
When using Enterprise Applications, the administrator has great visibility on the usage of the application. On the Overview item, we can see the total number of users/groups using the application, a graph with the usage of the app for the last month, and how many sign-ins happened within that period.
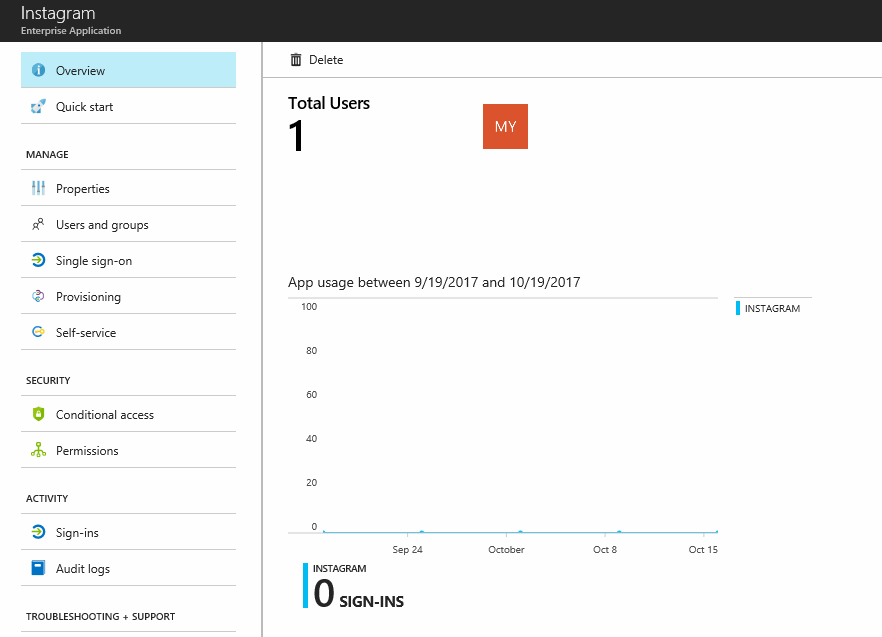
The administrator can check all log-in processes by clicking on Sign-ins item on the left side, and audit any modifications to the app. Data information can be queried in several ways to narrow the results. The results can be downloaded and shared with your audit team in case you have that requirement.
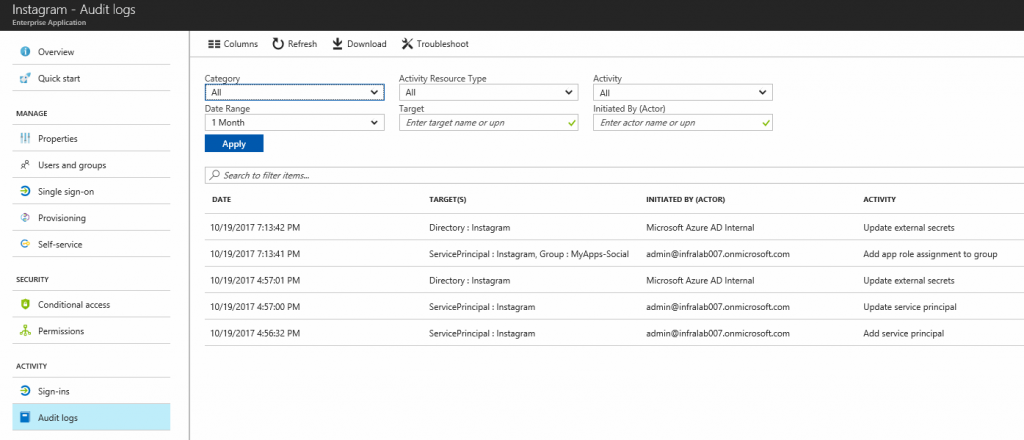
By applying these simple steps, your company can take advantage of Azure AD Enterprise Applications and protect your enterprise social media accounts from a central location. And, at the same time, improve security and measure the utilization of those apps.
Photo credit: Shutterstock



