The web application firewall (WAF), available as part of the WAF SKU section of the Azure Application Gateway, lends protection to web applications against common exploits and vulnerabilities. This web application firewall is set up based on the rules from OWASP core 2.2.9 or 3.0.
Web applications are common targets for several types of malicious attacks that exploit many commonly known vulnerabilities. Some of the most common among these attacks are cross-site scripting and SQL injection. It can be an extremely challenging task to prevent these kinds of attacks in the application code itself.
Such kind of prevention may need rigorous monitoring, patching, and maintenance in several layers of the application. When we deploy a central web application firewall, it helps to make security management quite simple and it also provides a better sense of assurance to application administrators that the application is well protected against intrusions or threats.
It is also true that a WAF-type solution can act much quicker against a security threat by being able to patch a known vulnerability at one central location as against securing each web application individually.
Any existing application gateway may be converted into an application enabled by a WAF rather easily.

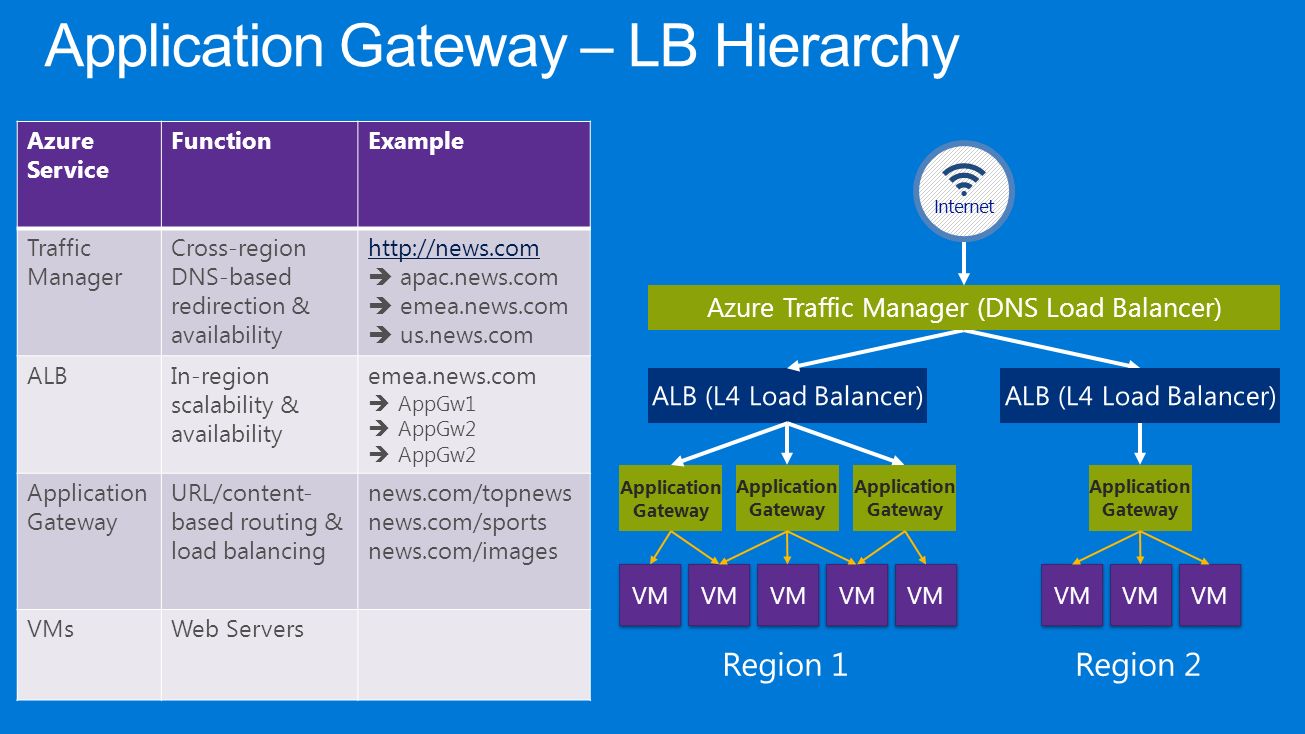
How does an application gateway operate?
An application gateway functions as an application delivery controller. It offers cookie-based affinity for sessions, round-robin distribution of loads, SSL termination, content-based routing, security enhancements, and the ability to host several websites. Some of the security-related enhancements offered by the application gateway include end-to-end SSL support and SSL policy management.
Given the fact that the WAF is now directly integrated into the ADC offering, application security is now incredibly enhanced. This creates a central location that is easy to configure, which can be used to protect your web applications against common vulnerabilities. No, it will not be able to protect you from the sugar bug the next time you see a glazed donut or a slice of carrot cake! How do you get that type of protection?!
Benefits of application gateway and WAF
These are the core benefits provided by the application gateway and WAF:
Protection
- Your web application is protected from attacks and web vulnerabilities without requiring any modifications to the backend code.
- Multiple web applications are protected at the same time from behind a gateway. The application gateway supports the hosting of up to 20 websites from behind one gateway all of which would be protected with the WAF in the event of web attacks occurring.
Monitoring
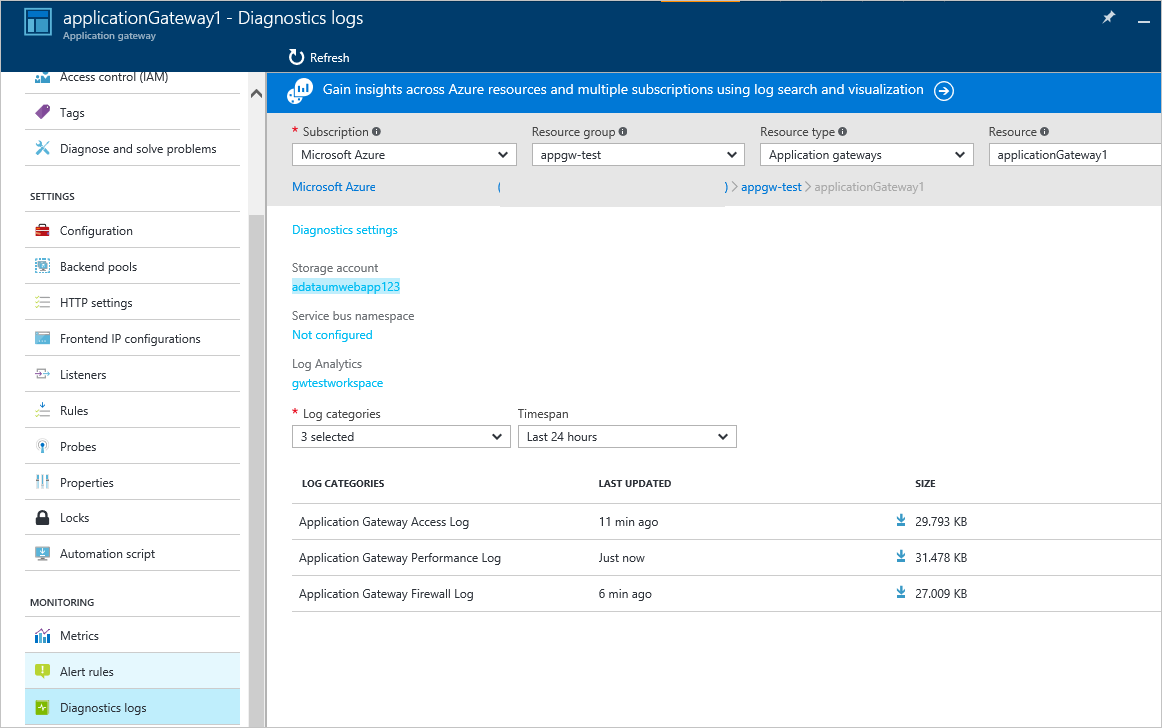
- Your web application is monitored against attacks using a real time WAF log. This log is actually integrated with the Azure monitor in order to track WAF logs and alerts, and monitor trends with ease.
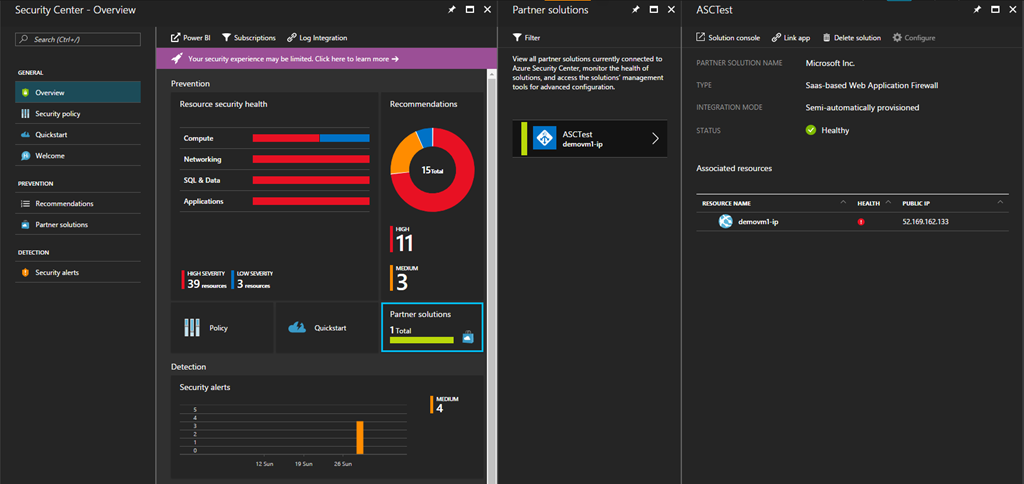
- Soon, what you are going to see happening is that the Azure Security Center will be integrated with WAF. Azure Security Center gives you a single place from where to get a central view of the complete security state of all of your Azure resources.
Customization
- WAF rules and rule groups can be customized to match your application requirements plus eliminate false positives.
Features
The Web application firewall comes preconfigured by default with CRS 3.0, or you may choose to use CRS 2.2.9. The greatest benefit of CRS 3.0 over CRS 2.2.9 is that it offers a much-reduced rate of false positives. Also, you get the ability to customize the rules to suit your specific needs. These are some of the most common vulnerabilities, attacks, violations, and attacker programs against which the web application firewall protects you:
- SQL injection.
- Cross-site scripting
- Common web attacks such as HTTP request smuggling, command injection, HTTP response splitting, and remote inclusion attacks(files).
- HTTP protocol violations.
- HTTP protocol anomalies including missing host user agent and accept headers.
- Bots, scanners, and crawlers.
- Common misconfigurations (IIS, Apache, etc.).
Core rule sets
The application gateway provides support for two rule sets: CRS 2.2.9 and CRS 3.0. These rule sets are both collections of rules that are designed to protect all your web applications from malicious activity.
OWASP_3.0
The core rule set in 3.0 that is provided has 13 different rule groups as displayed in the below table. Each of these rule groups contains several different rules, all of which can be individually disabled.
| Rule Group | Description |
| REQUEST-910-IP_REPUTATION | Rules to protect against malicious activity or known spammers |
| REQUEST-911-METHOD-ENFORCEMENT | Rules used to lock down (PUT, PATCH < ..) methods |
| REQUEST-912-DOS-PROTECTION | Protection against Denial of service attacks |
| REQUEST-913-SCANNER-DETECTION | Protection against environment and port scanners |
| REQUEST-920-PROTOCOL-ENFORCEMENT | For protection against encoding and protocol issues |
| REQUEST-930-APP-ATTACK-LFI | For protection against path and file attacks |
| REQUEST-931-APP-ATTACK-RFI | For protection against Remote File Inclusion |
| REQUEST-932-APP-ATTACK-RCE | For protection against Remote Code Execution |
| REQUEST-933-APP-ATTACK-PHP | For protection against PHP injection attacks |
| REQUEST-941-APP-ATTACK-XSS | For protection against cross scripting |
| REQUEST-942-APP-ATTACK-SQLI | For protection against SQL injection |
| REQUEST-943-APP-ATTACK-SESS-FIXATION | For protection against Sessions Fixation attacks |
OWASP_2.2.9
The core rule set in 2.2.9 that is provided has 10 different rule groups as displayed in the below table. Each of these rule groups contains several different rules, each of which can be individually disabled.
| Rule Group | Description |
| crs_20_protocol_violations | For protection against protocol violations such as GET with a req body, invalid characters etc. |
| crs_21_protocol_anomalies | For protection against incorrect header information |
| crs_23_request_limits | For protection against files or arguments that exceed limitations |
| crs_30_http_policy | For protection against restricted headers, methods and file types |
| crs_35_bad_robots | For protection against scanners and web crawlers |
| crs_40_generic_attacks | For protection against generic attacks such as PHP injection, remote file inclusion and sessions fixation) |
| crs_41_sql_injection_attacks | For protection against SQL injection attacks |
| crs_41_xss_attacks | For protection against cross site scripting |
| crs_42_tight_security | For protection against path traversal attacks |
| crs_45_trojans | For protection against backdoor Trojans |
WAF modes
The application gateway WAF may be configured to operate in two different modes:
- Detection mode: When WAF is configured to run in this mode, the gateway WAF logs and monitors all the threat related alerts into one log file. For this, logging diagnostics need to be turned on by using the diagnostics section. It also needs to be ensured that the WAF log is selected and kept turned on. When run in this mode, the firewall will not block any incoming requests.
- Prevention mode: When run in this mode, the gateway blocks attacks and intrusions as detected under its active rules. A 403-unauthorized access exception is returned back to the attacker and the connection is terminated. Such attacks continue to get logged in the WAF logs.
Secure your web applications from any malicious access with web application firewall. It’s the way forward.
Photo credit: Pexels



