
Increasing internet connectivity and cloud storage bring many security vulnerabilities. Cybercriminals often exploit these vulnerabilities to steal, expose, or destroy information from network systems. While many organizations have cybersecurity protocols to avoid cyberattacks, this isn’t enough to stop cybercriminals from attempting to gain unauthorized access. It’s important for you to understand that these attempts are often successful. Cybercriminals rely on attack vectors to launch their cyberattacks, and you have many different types of them to look out for!
In this article, I’ll explain what attack vectors are, how they work, what their different types are, and how to defend against them. First, let’s begin with a definition.
What Is an Attack Vector?
An attack vector is a cybersecurity term that describes a method used by a cybercriminal to gain unauthorized access to your network. Once they do gain access, they install malicious code that allows them to control your infrastructure or steal valuable data remotely.
Thus, cyber attack vectors allow cybercriminals to exploit your system’s vulnerabilities, cause a data breach, and steal sensitive and personally identifiable information (PII). This also results in significant financial and reputational loss.
Malware, viruses, malicious emails, pop-up pages, and text messages are common attack vectors that cybercriminals exploit to gain access to your network. Cybercriminals are becoming more creative and are constantly trying to explore every vulnerability in your system.
Let’s explore in detail how cybercriminals utilize attack vectors so that you can prevent future attacks!
How Do Cybercriminals Utilize Attack Vectors?
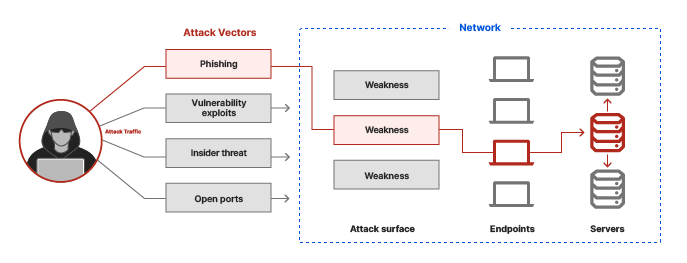
Different people exploit cyberattack vectors and for various purposes. For example, a disgruntled former employee may take advantage of vulnerabilities they’re aware of to get back at you, or your business competitor may want to launch attacks to derail your services, etc.
The 6-step process by which any of these people exploit attack vectors is generally the same, as given below:
- Identify the system they wish to target, in this case, yours.
- Collect necessary data about your system.
- Determine the most vulnerable attack vector for your system.
- Create tools to break through your system.
- Use the tools designed to break into your system and install malicious code.
- Install malware to monitor your network, steal or destroy your sensitive data, or crash your system, depending on their goals.
You generally have 2 forms in which cybercriminals may launch their attack, and they’re known as passive attacks and active attacks. Let’s discuss those 2 forms in more detail, starting with passive attack vectors.
1. Passive Attack Vectors
Passive attack vectors are methods by which a cybercriminal monitors your system for vulnerabilities and accesses your data without making any changes to your system. The cybercriminal’s main goal is to compromise the confidentiality of your data rather than cause any damage to your systems. Passive attack vector exploits are often difficult to detect by security systems since they don’t involve any changes to your system.
Cybercriminals can exploit passive attack vectors in 2 ways:
- Passive reconnaissance: The cybercriminal uses tools like Session Capture to monitor your system without engaging with it.
- Active reconnaissance: Here, the cybercriminal engages with your system through port scanning. Port scanning involves a cybercriminal sending messages (packets) to various ports on your system and then using the responses to find vulnerabilities in your system.
2. Active Attack Vectors
Unlike passive attacks, active attack vectors cause modifications in your system’s data and resources. In an active attack, cybercriminals use the information about your system to compromise it. Network security tools like antivirus software can detect these attacks, but you must also detect them as soon as possible to avoid any significant damage.
Cybercriminals will typically use a combination of passive and active attack vector exploits when they want to infiltrate your system. The best way to avoid these attacks is to know the common types of attack vectors. I’ll give a detailed explanation of these types next!
Common Types of Attack Vectors
Cybercriminals use a variety of attack vectors to target firms, as well as individuals. The following are some of the most common attack vectors:
Brute-Force Attacks
Brute-force attacks are a form of cryptogenic hack in which cybercriminals try to guess a user’s login details. Automated programs and botnets allow attackers to rapidly try various password combinations until they strike the right combination to log into your system.
Distributed Denial-of-Service (DDoS) Attack
A DDoS attack occurs when a cybercriminal uses several machines, commonly known as a botnet, to overload a server with internet traffic. This attack may cause an organization’s website to crash, meaning that the site can’t handle legitimate messages and traffic requests.
Insider Threats
Insider threats occur when employees of an organization leak confidential information to cybercriminals. Although this leak may be totally accidental, it’s often a coordinated attack from malicious insiders. Your employees may sell sensitive information to cybercriminals to hurt the organization from the inside.
Countering insider threats is often tricky since the malicious personnel usually have authorized access to various vital systems. One solution to counter an insider threat is to continuously monitor network access for any unusual activity.
Malware
Malware is short for malicious software and refers to programs that exploit your device. Typically, cybercriminals will embed the malware on a malicious link. Then, they’ll ask you to click on it to download a file.
After doing this, the malware infiltrates your system. It can then block access to specific files, alter or transfer sensitive data to an off-site device, or even derail your system’s functionality. Types of malware include ransomware, trojan horses, and spyware.
Phishing
One of the most common attack vectors for cybercriminals is the use of malicious emails, text messages, or calls. This social engineering attack, known as phishing, is fully designed to deceive unsuspecting individuals into giving up sensitive data, including login credentials and credit card information.
In phishing, the cybercriminal will typically pose as a genuine organization, seeking ways to help you solve a significant issue. In the process, they’ll ask you to provide certain sensitive data. Cybercriminals typically carry out a more specific and direct form of phishing, known as spear-phishing, after acquiring enough personal information about the target.
Unpatched Applications or Servers (Zero-Day Attack)
Another type of attack that happens is a zero-day attack. This occurs when cybercriminals find and exploit a vulnerability in a system before the IT security team is even aware of it. These vulnerabilities often come from unpatched software or servers.
Those are the most common types of attack vectors. Now, I’ll discuss how you can defend against them!
How You Can Defend Yourself against Attack Vectors
Protecting your devices against cybercriminals entails understanding the common cyber attack vectors. After that, you’ll know what countermeasures you can use against them. Below, I’ll explain some of these countermeasures:
- Adopt strong password policies, ensuring that usernames and passwords are the right mixes of length and randomization. Also, make sure your users don’t use the same credentials for different applications and systems.
- Confirm that you have cybersecurity software that monitors, identifies, alerts, and locks down vulnerable attack points. I’ll discuss some of these software solutions later on in the article!
- Use strong data encryption on devices containing sensitive information. AES and other advanced data encryption technologies are conveniently available for your use, so take advantage of them!
- Update all systems and services regularly. Once an update for hardware, software, or firmware gets issued, make certain that you install it immediately. These updates often come with security patches that protect your device from newfound vulnerabilities.
- Audit and test IT resources for vulnerabilities regularly. Internal IT vulnerability testing should get carried out quarterly, and you should perform external IT security audits annually. Also, you should also quickly modify security rules, methods, and prevention techniques in light of any important findings.
- Confirm that physical spaces are always secure. Even though most cyberattacks occur online, some attacks require offline access to get to data centers or servers. Make sure that these physical access points are fully secure, and that they’re only accessed by authorized personnel.
Trying to enforce and regularly monitor these cyber attack vector countermeasures can be rather difficult since you also have to focus on other operations. Thus, it’s imperative that you get a software solution that can handle all your cybersecurity needs while you focus on other tasks. I’ve reviewed some top security software solutions for you below.
Top 3 Best Software Options to Defend Against Cyberattacks
While you’re trying to protect your systems from an attack, cybercriminals are constantly seeking vulnerabilities and thinking up sophisticated methods to get into your system. Thus, you need to stay ahead of them. And one of the surest ways to ensure this is by using cybersecurity software. I’ll discuss 3 cybersecurity software solutions below, starting with GFI Software’s LanGuard.
1. GFI LanGuard

GFI LanGuard is a network security monitoring and vulnerability management software that’s compatible with multiple operating systems, applications, web browsers, and device networks. LanGuard also works on the simple principle of “Scan, Analyze, and Remediate.”
This solution helps you to easily identify high-priority vulnerabilities in your domains. It also helps to initiate proper mitigation of these vulnerabilities. Additionally, LanGuard provides a detailed description of the findings, their impact, and the steps for remediation. GFI LanGuard further improves your infrastructural security by remediating any flagged vulnerabilities.
Here are some more features of GFI LanGuard:
- Improves business process outcomes
- Improves compliance & risk management
- Drives innovation
- Creates operational efficiencies
GFI Languard has a simple, easy-to-use user interface. It’s available on a free trial and is easy to implement. Lastly, it fully supports many methods for vulnerability identification.
2. Cloudflare

Cloudflare is a multifaceted software solution that offers various services to secure your Internet connectivity. This solution provides excellent anti-DDoS services, such as DDoS detection and mitigation. This helps protect your network from all DDoS attacks, which will allow you to focus on business knowing that your website is fully secure.
Other services provided by Cloudflare include:
- A privacy-friendly DNS resolver to help speed up and secure your DNS requests by supporting DNS over HTTPS and DNS over TLS
- CDN service that allows your website to run faster
- API protection and bot management services to protect against malicious attacks on your API and regulate which bots have access to your web assets
Cloudflare is relatively cheap and is one of the best security software solutions to put in place if you’re running a website .
3. Check Point

Check Point is a cybersecurity software solution that protects users from various cyber threats, including malware. Check Point’s services ensure that you run your business seamlessly, with the assurance that your security needs are fully covered.
Here are some of Check Point’s services:
- Cloud protection services including container security and application security
- User and access security including endpoint security, anti-ransomware, and anti-phishing features
- Network security services, including Zero Trust security and Internet of Things (IoT) security
You’ve learned much in this article, haven’t you? Let’s wrap up now.
Final Words
Protecting yourself from cybercriminals requires that you recognize all the ways through which they can hurt you. This means you must know about all the attack vectors they can exploit to gain access to your system. You must also put in place effective measures to block off cybercriminals’ access. Using cybersecurity software solutions like GFI LanGuard can efficiently help you protect your system, giving you the peace of mind to run your business without having to worry about what goes on in cyberspace.
I hope this article gave you an insight into attack vectors and their types and how you can protect yourself from getting exploited through these vectors.
Do you have more questions about attack vectors? Check out the FAQ and Resources sections below!
FAQ
Why do cybercriminals exploit attack vectors?
Cybercriminals exploit attack vectors in order to steal valuable information. Then, they can use this information for monetary gains. In other cases, these cybercriminals seek to destroy your reputation, so they exploit these vectors to retrieve sensitive information which they can release to the public. Cybercriminals may also exploit attack vectors to derail your business operations so they can gain an advantage.
How can I detect attack vectors?
Attack vectors are directly linked to security vulnerabilities in your system. The more vulnerabilities you have, the more attack vectors exist in your system. Regular vulnerability assessments can help you locate all attack vectors in your system. However, the easiest way to identify all existing and new attack vectors is by using cybersecurity software with an attack surface monitoring solution.
What can I do if an attack vector gets exploited?
If an attack vector on your system has gotten exploited, then you may have experienced a data breach. Once you experience such a breach, you should conduct a detailed IT security audit. The security audit will assess the breach and all the information stolen. After that, it’ll determine the best course of action. You might also have to report the breach to regulatory authorities.
Are people also considered as attack vectors?
Yes, human beings also can be attack vectors. A type of cyberattack known as social engineering, relies on human psychology to deceive people into revealing login credentials to cybercriminals. Disgruntled employees may also act as attack vectors by helping cybercriminals gain access to company data centers and servers.
Can my system be completely free of vulnerabilities?
It’s important that your system achieves a high degree of protection. Deploying effective countermeasures to all known attack vectors can significantly derail attacks against you. However, cybercriminals are persistent and are constantly seeking vulnerabilities that you might be unaware of. Using cybersecurity software can help ensure that new vulnerabilities are immediately flagged and mitigated before cybercriminals get a chance to exploit them.
Resources
TechGenix: Newsletters
Subscribe to our newsletters for more quality content.
TechGenix: Article on Credential Harvesting
Read more about how cybercriminals conduct credential harvesting.
TechGenix: Article on Data Leaks
Learn more about data leaks and how you can prevent them.
TechGenix: Article on Operational Security
Learn about operational security and how to manage security risks.
TechGenix: Article on DNS Hijacking
Read about how DNS gets hijacked and how you can protect yours.



