Cybersecurity is one of the major issues organizations face these days. While organizations spend precious IT dollars to ensure business services are operating normally in case of any disaster, they often fail to pay attention to the controls and mechanisms that are required to protect business assets from insider threats. Every organization has deployed highly available IT infrastructure to ensure business interruption is minimized in the case of any disasters. While you can implement highly available infrastructure to minimize interruption in the business services and make sure business services are available in case of disasters, you cannot prevent cybersecurity attacks unless you work on cybersecurity methods and mechanisms. Open network shares, for example, have become targets of attackers who under the right circumstances can load them with ransomware and encrypt files. But the real threat with open network shares is a current or past rogue employee who can find and steal important company data.
While it doesn’t take much effort to avoid risks related to cybersecurity, it’s an effort that must be made. When it comes to working on cybersecurity for your organization, your first task is to implement the necessary policies, controls, and mechanisms to detect and prevent threats. While you can take necessary steps to ensure company information is not stolen or is not taken out of the company premises, your efforts cannot ensure that all information is protected from every insider threat unless all security protocols and standards are followed. You will be required to follow a steady cybersecurity approach to ensure your organization is protected from both nontechnical and technical threats.
The damages that a threat can cause to your organization is painful, and you can lose business if not protected. We have written this article to help you understand why it is important to search for open network shares on every computer that is joined to the Active Directory. We also provide a PowerShell script that can be used to search for open network shares so you can take appropriate action.
Gaining access to open network shares
Any employee who has access to the IT environment and has a username and password to log on to the systems can gain control over the systems. For example, an employee who is a domain admin can gain access to the Active Directory environment, which, in turn, allows them access to valuable information. Similarly, any employee who works on valuable company information can copy data to a USB stick and have it distributed for monetary purposes.
If a user gets a new role in an organization and if the user is a qualified IT expert, they can easily search through the entire network or Active Directory to find systems that host company data such as servers hosting company documents and network shares to which everyone has been assigned full control permissions. For example, an attacker can run a PowerShell script that can check for network shares that are open and then try to steal or collect information from these network shares. Once an attacker obtains this information, it becomes easier to copy the data from the network shares. This PowerShell script can check how many network shares are open on a given computer.
$TestCSVFile ="C:\Temp\NetworkShares.CSV"
Remove-Item $TestCSVFile
$STR = "Computer Name, Total Shares, Final Status"
Add-Content $TestCSVFile $STR
$CompList = "C:\Temp\Computers.TXT"
$AnyGap = "No"
ForEach ($Computer in $CompList)
{
$TotalShares=Get-WmiObject -class Win32_Share -computer $Computer
$TotSCount = $TotalShares.Count
$FinStatus = "Ok"
IF ($TotSCount -ne 0)
{
$FinStatus = "This computer has $TotSCount Please check."
$AnyGap = "Yes"
}
$STR = $Computer+","+$TotSCount+","+$FinStatus
Add-Content $TestCSVFile $STR
}
IF ($AnyGap -eq "Yes")
{
$TestText = " "
$SumVal = ""
$TestStatus="High"
}
else
{
$TestText = " "
$SumVal = ""
$TestStatus="Passed"
}
Once the script has finished executing, you will have a report generated under C:\Temp\NetworkShares.CSV, which contains the computer name and the total number of network shares as shown in the screenshot below.
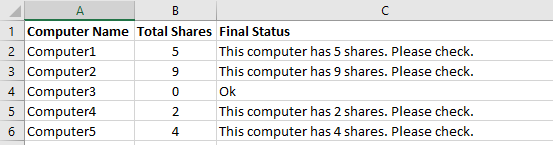
The above script was retrieved from DynamicPacks IT Scanner, a tool designed to perform cybersecurity assessment in production environments. The DynamicPacks IT Scanner can perform 45 cybersecurity checks and generate a report with affected objects. All you need to do is create an assessment profile and add all Cybersecurity Dynamic Packs. Once you have a report on the affected objects you can take action to prevent data loss in your company.
Featured image: Freepik / Business photo created by bedneyimages



