It seems like almost a daily occurrence that I get an email or a phone call from someone who has either been victimized by a phishing attack or is seeing something unexpected on their computer and is not quite sure what to do about it. For IT pros, this trend should be deeply concerning. Even if you know how to avoid a phishing attack, chances are that at least some of your users do not. That being the case, I wanted to take the opportunity to talk about how these scams work and how to spot fraudulent messages.
What’s the end game?
There are countless varieties of phishing scams, with just as varied objectives. Some seek to drain bank accounts. Some scammers want to receive untraceable bitcoins or iTunes gift cards. Still other scammers want to steal identities, credit card numbers, or who knows what else. The one thing that most of these scams have in common is that they start by attempting to get the victim to click on something that they shouldn’t. I will show you some examples in a moment. For right now though, I want to talk about what happens when a user baited by a phishing attack clicks on a malicious link.
Clicking a bad link
In many cases, clicking on a malicious link causes malware to be installed. What many people do not realize, however, is that sometimes malicious activity does not inflict any harm to the victim’s computer whatsoever, but rather targets other resources such as bank accounts. Let me show you how this works.
Setting the trap
Let’s pretend for a moment that a criminal wanted to steal bank account login credentials, and wanted the crime to go undetected for as long as possible. The first step in doing so, even before creating malicious links, would be to build a Web resource that could collect the account information. Here is how it works.
The first thing that a scammer might do in advance of launching a phishing attack is to register a domain name that is similar to the one used by the resource that they want to compromise. For the sake of example, I am going to use Bank of America, but what I am about to show you would work for just about any online bank. I have nothing against Bank of America. I just needed a real bank in order to show you how this particular exploit works, and that was the first bank to come to mind.
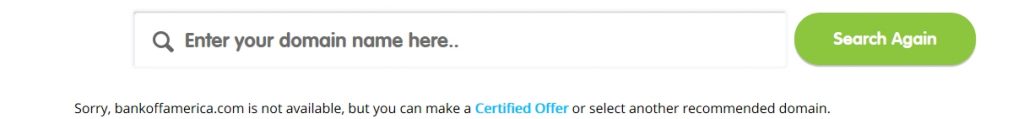
So if a criminal wanted to intercept Bank of America logins, the first thing that they might do is to register a domain name that looks a lot like the legitimate domain name. Instead of bankofamerica.com for example, the criminal might go with bankoffamerica.com. Notice the extra F in the domain name?
If this sounds completely theoretical, then check out the screen capture below. Someone has actually registered this domain name. I have no idea who owns the domain name, or if it is being used for illicit purposes or not. I’m not about to try visiting the URL to find out. Sorry. In many cases, criminals will register domain names that are similar to the domain names being used by their targets. In other cases, a bank might register similar domain names itself, just to prevent criminals from being able to register those domain names. Hence, it is entirely possible that bankoffamerica.com is owned Bank of America. It’s also possible that the domain names are being used by a third party for legitimate purposes.
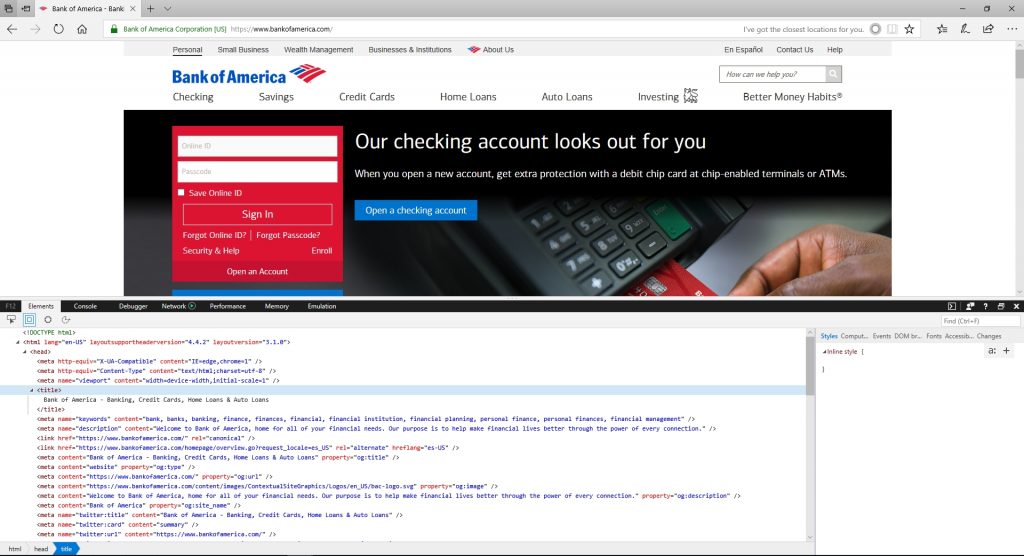
The next thing that the criminal in this example would need to do is to convince potential victims that they are indeed Bank of America. This is ridiculously easy to do, because many people do not bother checking digital certificates. If you look at the figure below, you can see the real Bank of America website. You can also see the HTML code that makes up the page. This isn’t the same as the backend code that performs login authentication, but the criminal does not need that code.
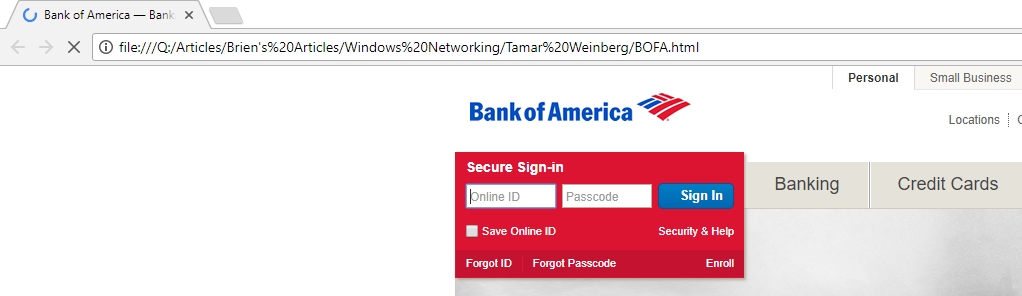
The criminal can download the HTML code, page graphics, etc. to their own Web server, and essentially host a duplicate of the bank’s sign-on page. Check out the figure below. In the interest of time, I didn’t bother to set up a Web server, but as you can see I have saved everything necessary to reproduce the Web page to my own computer. The URL indicates that I am accessing the page from a local drive.
So now our imaginary criminal has a Web server that is configured to use a URL that is similar to Bank of America, and whose home page looks a lot like the Bank of America home page, but the page does not do anything yet. In order to make the phishing attack work, the criminal has to do two things.
First, the criminal has to modify the code on their own copy of the Bank of America sign-in screen. Typically, this would mean adding some code to capture any login credentials that are entered, and then save those credentials to a backend database. After capturing this information, the fake login page might even silently redirect the victim to the real Bank of America sign in page so that the victim does not realize that their credentials have been compromised. I do not want to encourage criminal activity, so I am not going to provide code for completing this process, but developing the code is quite simple to do.
The other thing that the criminal would have to do is to trick the victim into visiting the phony site. Some people will inevitably make a typo and end up on the criminal’s fake site by accident, but rather than relying on chance, the criminal will commonly send out email messages to large numbers of people in hopes that someone will click on a link within the message.
Elements of a phishing attack email
As previously mentioned, there are an infinite variety of phishing attack messages, but there are definitely some things to look for. Let’s take a look at some real messages and the telltale signs that those messages might not be on the up and up. For this section, I will stop using Bank of America as an example, and talk about phishing messages in a more general way.
‘Your account is pending cancellation’
Here is an email that makes it seem that one of my domains is about to expire. A closer look, however, reveals that the message isn’t from the domain registrar, but rather from someone who is trying to trick me into signing up for SEO services. The sender tries to create a sense of urgency by saying that my account is pending cancellation, even though I do not have an account with this SEO provider.

Grammatical errors
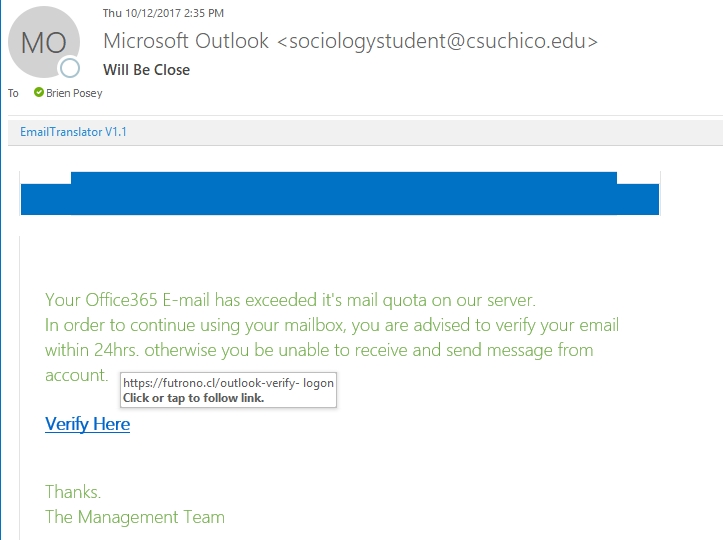
Here is another one. This one appears to be from some sort of Office 365 tech support service, even though the return address is from Sociology Student. Like the previous message, this one tries to create a sense of urgency by saying that my mailbox has exceeded its limit, and that pretty soon I won’t be able to use it.
One big giveaway is that the message is jam-packed with grammatical errors. Notice that the subject line says that my mailbox “will be close.” Really? Close to what? And of course, this message contains the dubious Verify Here link. As you can see in the screen capture, hovering over the link displays a URL that is suspect, to say the least.
Missing relevant details
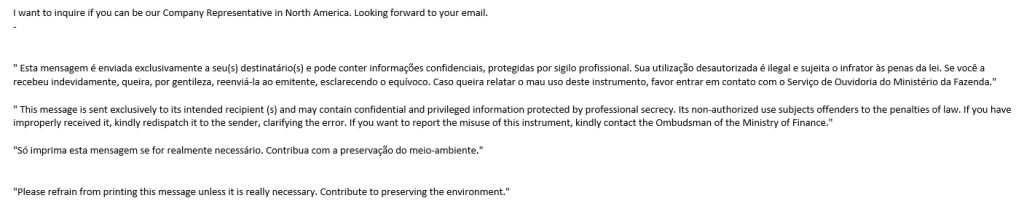
Here is another one. It looks like this person wants me to be their company representative in North America. There’s just one problem… They never say what the company is, who they are, what they do, or why they think I should be their company representative. I did, however, get a kick out of the environmental statement at the end of the message. It’s so rare to see a scammer who cares. Wow, this could be a great new career for me!
Legal advice
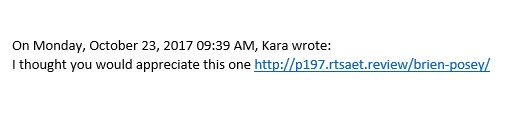
Another email, which lists a law firm as the sender, simply says, “I thought that you would appreciate this one.” I can only imagine what would happen if I were to click on the link. Incidentally, you will notice that this message contains none of the elements that you would normally expect in a message from a law firm, such as a message signature, a confidentiality notice, or a logo.
Let’s get serious
OK, I will admit that I was probably having way too much fun going through those phishing messages. Those messages are so obviously fraudulent that it is hard not to laugh at them. But let’s look at some that are a bit more convincing.
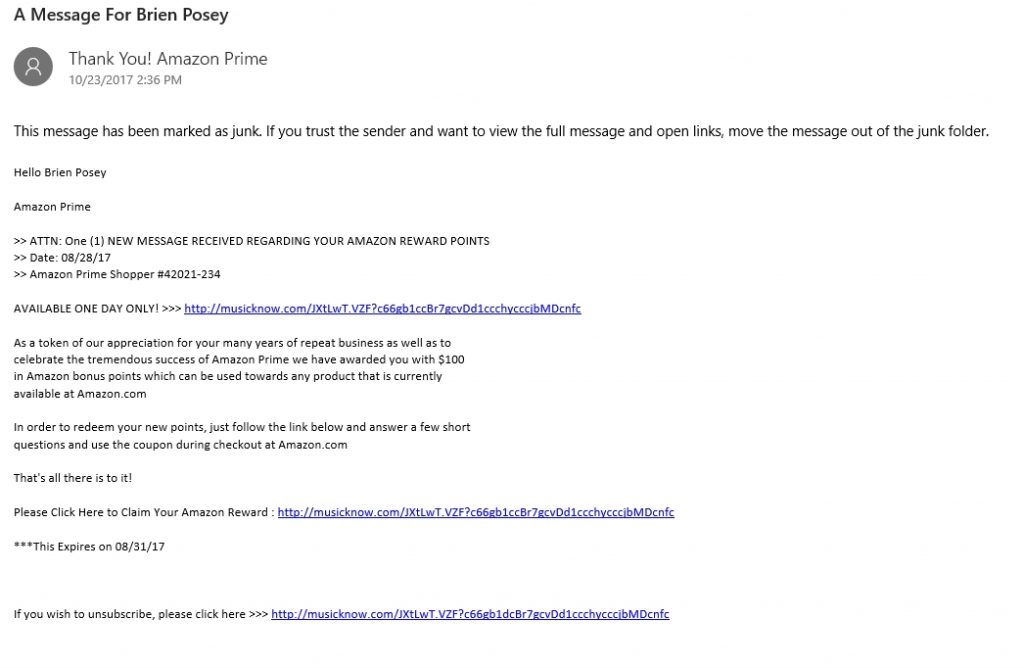
Here is one claiming to be from Amazon Prime, telling me that I have received a $100 credit as a reward for being a loyal customer. The problem with this message, aside from the fact that I don’t have an Amazon Prime account, is that the URL does not point to an Amazon site. Never mind that it does not contain the graphical elements that are normally included in legit messages from Amazon.
Here is another one. This message claims to be from Tesco Bank. Not only do I not have an account at Tesco Bank, but Outlook even identified this message as a phishing attack. Let’s pretend for a moment, however, that I do have an account and that there was no warning from Outlook. Let’s also pretend that the Tesco Bank logo was displayed correctly. How would we determine that this is a phishing message?
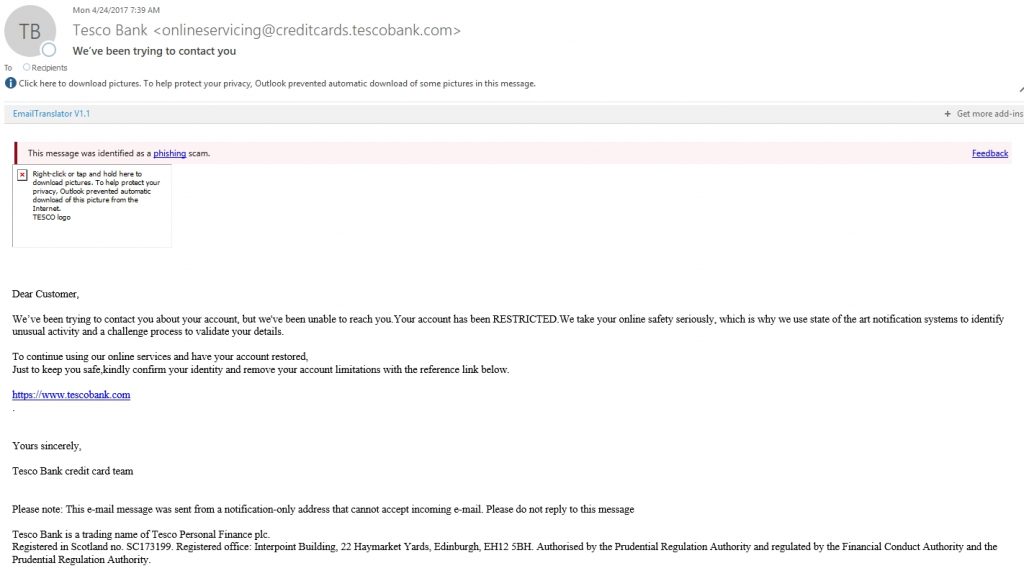
There are a few things about this message that stand out, although it is one of the more convincing phishing messages. For starters, the message says that my account has been restricted, but does not say what that means. Another sign that this message is not legit is that the second paragraph starts with a sentence fragment, and is followed by a really convoluted sentence. A legitimate bank is not going to send out a message containing such poor grammar. The message also implies that the recipient can undo the restrictions (whatever those restrictions might be) by simply clicking on a link. No bank does that. If an account is locked out, the account is locked for a reason.
The real giveaway that this message is fraudulent, however, is what happens when you hover over the link. Even though the link claims to point to www.tescobank.com, hovering over the link reveals that the link actually points somewhere quite different.
Non-email links
One more thing that I want to point out is that even though I have been talking primarily about malicious links within email messages, phishing is not confined to email. Perhaps the common phishing attack is a tech support scam in which a window pops up and tells you that something is wrong with your computer and that you need to call a support phone number. There are countless varieties of this message, and some of these messages even speak in a robotic sounding voice. Here is what one such message looks like.
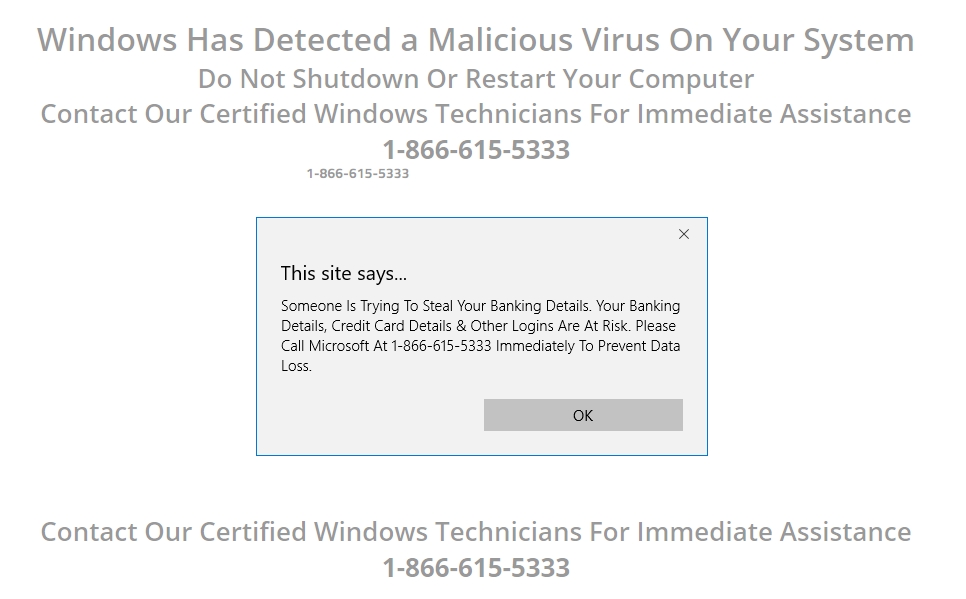
One of the things that seem to cause people to fall for this scam is that the warning can appear on legitimate websites. It’s possible that scammers buy ads on the site, and then upload code to display these types of warnings rather than an ad. Based on my own experiences, these types of warnings are never real. In fact, it becomes pretty obvious that the message is not real when you begin to objectively parse the message’s contents. Here’s an example: In one part of the message, the victim is told to call Microsoft. In two other places, however, the message says “contact our certified Windows technicians.” As the creator of Windows, does Microsoft really need to tell people that its employees are certified Windows technicians?
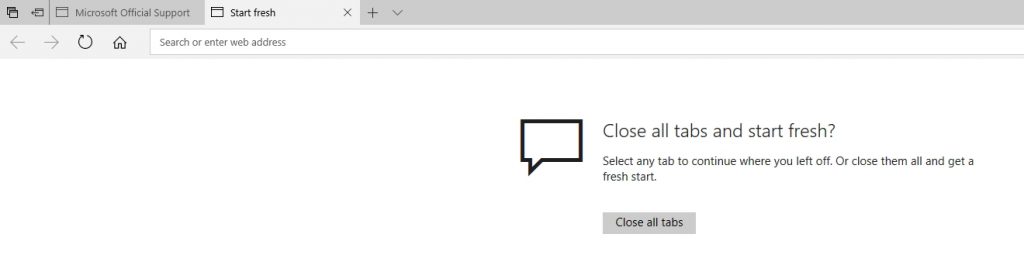
The best thing to do when you receive such a warning (in Windows) is to press Ctrl+Alt+Delete and then open Task Manager. When Task Manager opens, close the browser. In the case of the Edge browser, the next time that you launch the browser, you will have an option to close any open pages and start fresh. This will get rid of those annoying browser popups (assuming that they are not being generated by an infection on your PC).
Scams and laughs
I know that I have covered a lot of ground, but my sincere hope is that I have given you some insight into the way that a phishing attack works, and maybe helped you to have a few laughs along the way.
Photo credit: Shutterstock



