We IT pros rely on a variety of tools to keep our networks secure, but have you ever thought about using Google Search as a security tool? I’m not talking about searching for information on how to better secure your network, but rather using Google as an actual security tool. The idea isn’t quite as crazy as it sounds. Let me explain.
Not long after Google began to gain mainstream acceptance, I started hearing people talking about Google hacking. Back then, the widespread commercial use of the Internet was relatively new, and not surprisingly the websites of the time often had gaping security holes. It didn’t take long before someone realized that Google had the ability to do pattern searches (such as looking for numbers that match a certain pattern) and that pattern searches could be exploited in an effort to gain access to sensitive information that had been accidentally exposed on the Internet.
Early on, I heard stories of people using pattern-matching techniques within Google to search the web for credit card numbers. The same technique was also used in an effort to find Social Security numbers and other types of highly sensitive personal information.
Of course it didn’t take long for Google to catch wind of these techniques, and to take measures to try to keep the search engine from being used for illicit purposes. So that’s the end of the story, right? Not quite.
Although most people simply enter a short phrase into the Google Search engine whenever they need to find something online, Google searches can actually include filters and commands that are intended to help you to perform searches that are more targeted. However, these same commands can also be put to work as a tool for helping IT professionals to make sure that they aren’t accidentally exposing backend resources to the Internet.
Using Google to detect resources that have been accidentally exposed to the Internet can be a complicated process, and it isn’t an exact science. Searches that are well-aligned to one organization’s needs might not be exactly right for another organization. Even so, I want to give you some pointers to help you to get stated.
Google Search as a security tool: Focus on your own domain
If your goal is to use Google to see what resources are exposed to the Internet, then the first thing that you will need to do is to cut through the clutter by filtering out any search results that are not directly related to your own organization. Thankfully, Google makes this really easy to do.
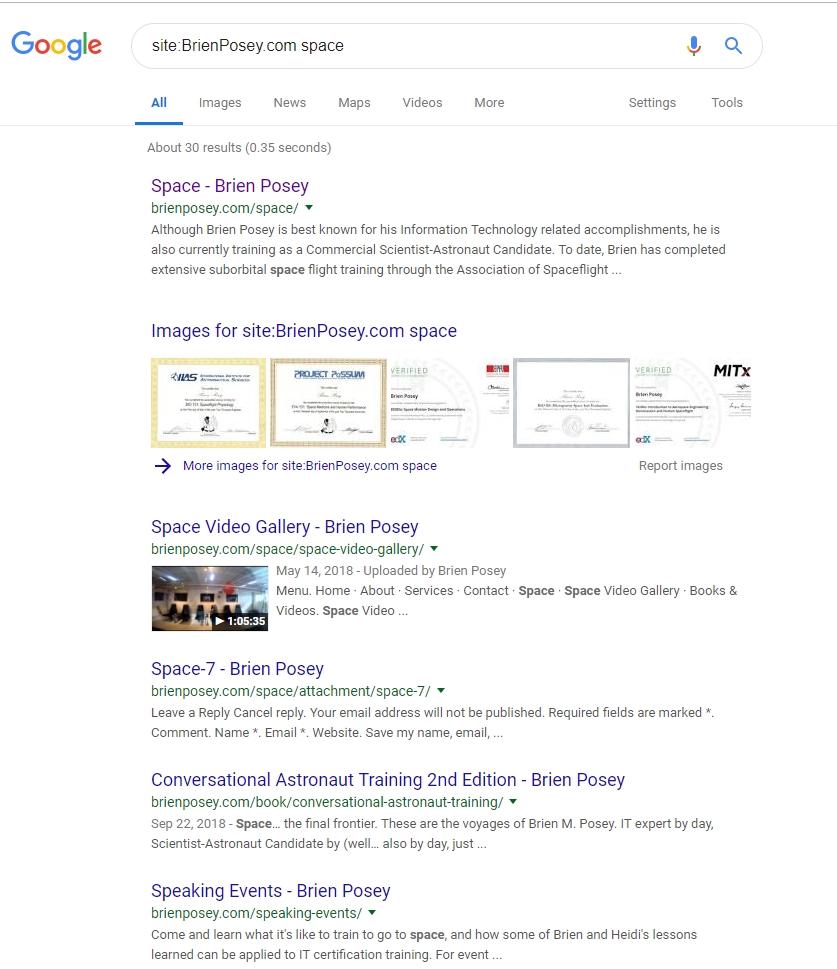
If you want to limit a Google search to a single domain, then you can do so by leveraging the site command. Simply enter the word site followed by a colon, and the name of the domain that you want to search. From there, you can enter your search terms. If you look at the figure below for example, you can see that I searched my own domain (BrienPosey.com) for the word Space, by entering the following search query:
Site:BrienPosey.com space
What else can you find?
So now that I have shown you how to search your own domain, it’s time to begin figuring out what types of commands might be used to discover sensitive resources that might have been accidentally exposed to the Internet.
As I mentioned before, the nature of these queries is going to vary widely from one organization to the next. However, there is a basic strategy that you can use as a starting point. Rather than trying to pattern-match credit card numbers and Social Security numbers as has been done in the past, consider instead the types of resources that might realistically have been exposed by accident. For example, you might employ Google Search as a security tool to do a series of searches intended to expose any backend web management consoles that may have been exposed to the Internet by accident. This could be anything from your payroll app to the VMware Web interface.
Formulating the search queries
It will, of course, be up to you to come up with queries that can determine whether or not Google has indexed any of your backend resources. Fortunately, there are some resources that are available to help you.
I recommend starting out by familiarizing yourself with the Google’s search operators. There is a full list of these operators here. Knowing which operators are available will go a long way toward helping you to develop effective queries.
The other thing that I recommend doing is to check out the Google Hacking Database. As its name implies, the Google Hacking Database is a web page that lists thousands of Google queries that can be used in an attempted hack. You can see an example of what this page looks like in the figure below.
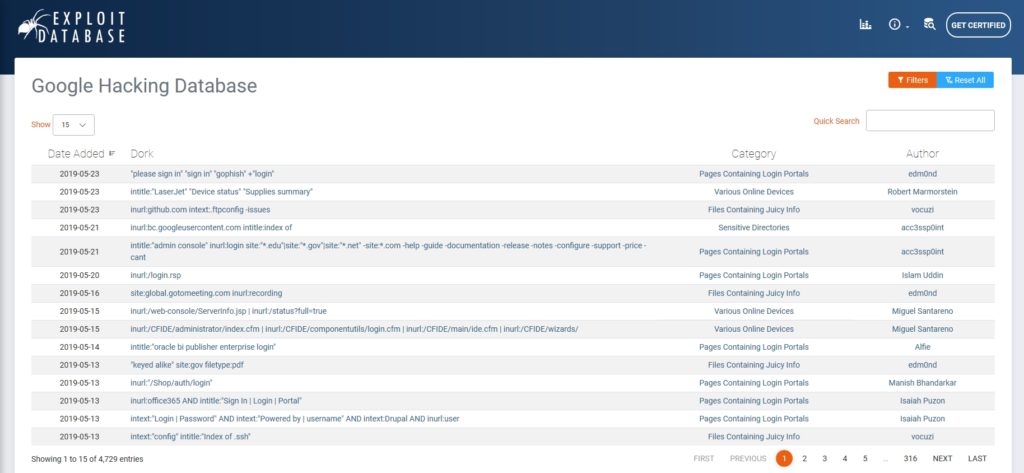
As you look at the screenshot above, you will notice that the various search queries are all categorized. There are queries designed to detect pages containing login portals for example, as well as queries to detect online devices. These category names are all clickable, thereby allowing you to see the queries that fall into each category. These queries can be highly varied. The Various Online Devices category for instance contains queries designed to detect everything from HP printers to 3CX phone systems.
The individual queries are also clickable. Clicking on a query does not cause the query to be executed however, but rather causes a page to be displayed that provides information about what the query is intended to do.
Somewhat ironically, the Google Hacking Database also contains its own search interface that you can use to look for specific types of queries. Searching on the word VMware, for instance, reveals queries designed to detect the VMware login portal and various files (Excel, Word, and PDF) that have been exposed within a VMware environment. You can see what this looks like in the screenshot below.

Google Hacking Database: Good, but only a start
As helpful as the Google Hacking Database may be for helping you to come up with Google Queries to reveal what resources Google may have detected within your own domain, the queries that are listed within the Google Hacking Database typically cannot be used as-is. If you were to perform the Intitle:“VMware Management Interface” query listed in the previous screen capture, for instance, Google would display any detected instances of the VMware Management Interface across the entire Internet. That’s great if your goal is to hack someone else’s VMware deployment, but it isn’t exactly helpful if you are trying to evaluate your own security. As such, you will typically have to combine the queries found in the Google Hacking Database with the Site: command and the name of your domain. That way, you can limit the query to your own organization’s resources.
One more thing that you should pay attention to is the date on which the various queries were added to the database. Google changes over time, as does other software. The last query listed in the previous screen capture was added to the database way back in 2005. This query might still be valid from Google’s prospective, but it may or may not be relevant to the version of VMware that your organization is running. The point is that some queries may have to be adapted to account for differences between one software version and another.
Featured image: Shutterstock



