In difficult times like this, we need to ensure security and remote access to our users. Unfortunately, I see a spike in the number of security incidents, which means that there are a lot of people out there using this as an opportunity to hack systems. As cloud administrators, we must enforce our security posture to ensure that our workforce can connect securely to our environment and keep the bad guys out of our environment. When enabling Azure Premium P1 or P2, we may see additional screens when a regular user tries to log on using Azure Active Directory. That is great from the security perspective. However, to avoid panicking our remote users, we should understand what introducing new MFA changes means, and it must be supported by communication. We will cover how to enforce MFA to your users in an upcoming article, but for now, we will identify where we can manage the behavior that is shown in the image below.

Logged in the Azure Portal, click on Azure Active Directory, Security, and then click on the Identity Protection item on the left. In the new blade, click on the MFA registration policy, and we will notice that we have assigned to All users, and we can change that to accommodate a phased rollout or testing purposes.
Click on Select a control in the Controls area.
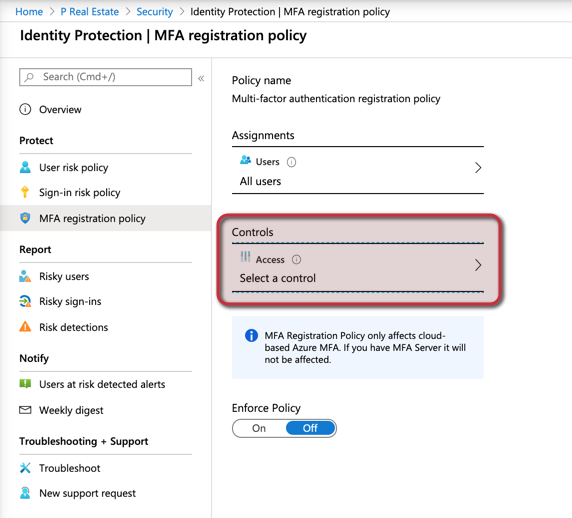
Here is the configuration that is triggering that new dialog box when the users are authenticating with Azure Active Directory.




