Security is a top priority for any cloud provider, and it must have the same priority for any IT department when moving their applications and infrastructure to the cloud. When using Microsoft Azure, you will be presented with a variety of security features in all shapes and forms. In today’s article, we are going to cover a basic one called network security groups (NSG for short). They are essential to protect the traffic in any given subnet within a virtual network (VNet from this point on in this article) and virtual network interfaces (vNIC).
An NSG comes with some default rules to allow the essential services to run on the new VMs, and the cloud administrator is responsible for managing all other traffic required. All rules will be evaluated based on their priority using these following five types of information: source, source port, destination, destination port, and protocol.
We will be managing the network security groups feature using PowerShell. There are two distinct cmdlets to associate an existent network security group to either a vNIC or VNet, and we will cover both of them in this article.
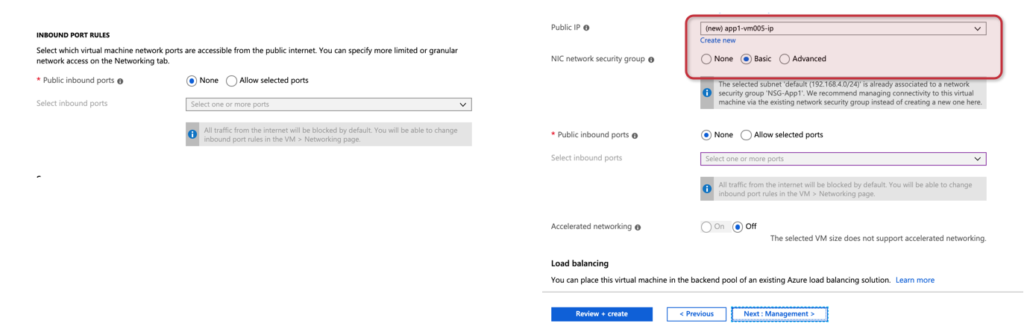
You can always create your network security groups during the provision of your VMs. Their presence can be seen on the very first page of the provisioning process, and then again on the Networking page of the wizard. In that last page, we can define if we don’t want an NSG at all by selecting None, and use a Basic or Advanced interface to customize the security rules.
Understanding the basic PowerShell cmdlets
Before diving into the cmdlets to configure either a VNet or vNIC, we need to get acquainted with some basic PowerShell cmdlets that are required when managing NSGs.
These cmdlets will help you to list the resource group names (first one), list the network interfaces (second line), and list the network security groups (the third one). We can always list the VMs running and their vNICs using the fourth cmdlet. Keep in mind that they are using the parameter ResourceGroupName, which was used in the first cmdlet.
- Get-AzResourceGroup | Select ResourceGroupName
- Get-AzNetworkInterface -ResourceGroupName “<ResourceGroupName>”
- Get-AzNetworkSecurityGroup | Select Name,ResourceGroupName,Location
- Get-AzVM | select Name,ResourceGroupName,Location -ExpandProperty NetworkProfile | fl
Note: If you want to save time, you can always use a variable instead of typing in the resource group name every time.
Managing network security groups at the virtual network interface level
If you want something more specific and are applying an NSG at the VM level, in this case, the Set-AzureRMNetworkInterface cmdlet will be your tool of choice to perform this task.
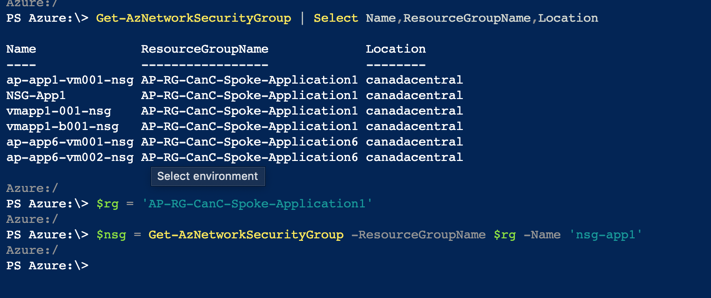
The first step is to retrieve the network security groups and save the specific NSG into a variable. These two cmdlets are required:
Get-AzNetworkSecurityGroup | Select Name,ResourceGroupName,Location $rg = ‘ResourceGroupName’ $nsg = Get-AzNetworkSecurityGroup -ResourceGroupName $rg -Name ‘<NSGName>’
The second step is to list all vNICs available. First, find the vNIC attached to the VM that you want to apply the NSG. Then, we need to add the vNIC to a PowerShell variable.
Get-AzVM | select Name,ResourceGroupName,Location -ExpandProperty NetworkProfile | fl $vNIC = Get-AzNetworkInterface -ResourceGroupName $rg -Name ‘ap-app1-vm001268’

The final step is to use the variables that we created in the previous step and apply the changes. We are going to do that using the $vNIC variable that we have just populated and configured the network security group. We are going to use the $nsg variable that we defined in the first step of this section. The process to apply the changes is to run the Set-AzuresNetworkInterface as an output of the $vNIC variable.
$vNIC.NetworkSecurityGroup = $nsg $vNIC | Set-AzNetworkInterface

The result of the PowerShell cmdlet can be easily checked in the Azure Portal. Click on Networking (Item 1) of the VM that we have chosen to apply the network security group. The network interface will be displayed on the right side (Item 2) next to the network/subnet, public IP, and private IP information. In Item 3, we can check that the network security group is associated with the interface.

Managing NSGs at VNet level
The recommendation is always to reduce the number of network security groups, and by doing that, we can have smaller building blocks applied to a subnet instead of a specific VM.
To assign network security groups to a VNet/Subnet level is using the Set-AzureRMVirtualNetworkSubnetConfig cmdlet, which associates an NSG to a virtual network (VNet).
Get-AzNetworkSecurityGroup | Select Name,ResourceGroupName,Location $nsg = Get-AzNetworkSecurityGroup -ResourceGroupName $rg -Name ‘<NSGName>’

Get-AzVirtualNetwork | select Name $VNet = get-azvirtualnetwork -Name ‘<VNet-Name>’
Get-AzVirtualNetworkSubnetConfig -VirtualNetwork $VNet | select Name,AddressPrefix $VNetSubnet = Get-AzVirtualNetworkSubnetConfig -VirtualNetwork $VNet -Name default

Set-AzVirtualNetworkSubnetConfig -Name $VNetSubnet.Name -VirtualNetwork $VNet -AddressPrefix $VNetSubnet.AddressPrefix -NetworkSecurityGroup $nsg $VNet | Set-AzVirtualNetwork
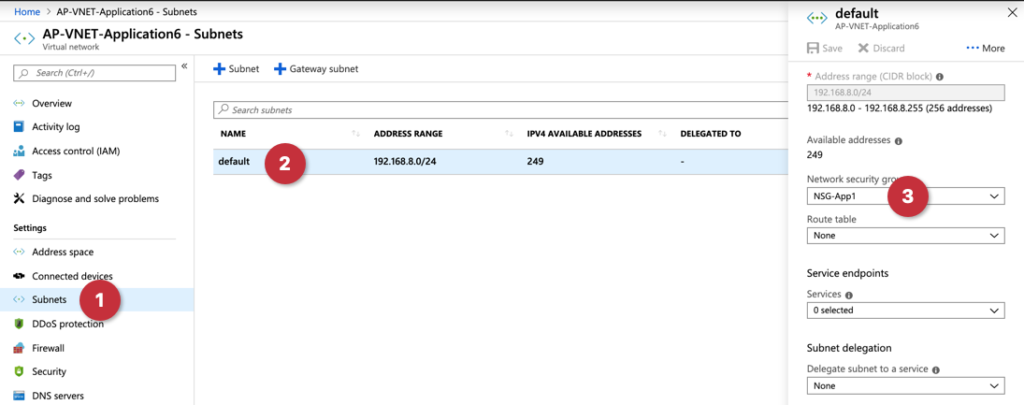
The results can be seen in the Azure Portal. Logged on to the portal, click on the VNet, click on Subnets (Item 1), select the desired subnet (Item 2), check the network security group to see if there is an NSG associated to the subnet.
Featured image: Pixabay



