In this issue
Modern Security: What is the value of a unified XDR and SIEM solution? (Guest editorial by Rodney Buike). ALERT: Malware protection on Big Sur. Factoid – This space for rent. Plus lots more — read it all, read it here on WServerNews!
Enjoy this week’s newsletter and feel free to send us feedback on any of the topics we’ve covered — we love hearing from our readers! And please tell others about WServerNews! It’s free and always will be free — and they can subscribe to it here. Thanks!!!
Got questions? Ask our readers!
WServerNews goes out each week to almost 200,000 IT pro subscribers worldwide! That’s a lot of expertise to tap into. Do you need help with some technical problem or are looking for expert advice on something IT-related? Ask Our Readers by emailing your problems and/or questions to us at [email protected]
Editor’s Corner
This issue features a guest editorial by my friend and colleague Rodney Buike. Rodney is currently the National Lead for Identity and Cybersecurity at Microsoft Canada focused on enhancing the security and compliance practices of Microsoft clients worldwide. I know Rodney from way back around in when, while working as sysadmin for an SMB here in Winnipeg and an active member of our local IT pro user group, he started a popular site called TheLazyAdmin.com that was dedicated to helping busy IT pros find ways to do their work more efficiently and with the least possible effort.
Anyways, I hope you enjoy reading Rodney’s article and learn something useful you can use to help you better protect the IT infrastructure at your business or organization.
Modern Security: What is the value of a unified XDR and SIEM solution? (Guest editorial by Rodney Buike)
Rodney Buike is the National Lead for Identity and Cybersecurity at Microsoft Canada focused on enhancing the security and compliance practices of Microsoft clients worldwide.
If you have been following the recent security announcements from Microsoft, you have been seeing a lot about SIEM and XDR, on top of recently announced features under the Microsoft Defender banner. All too often, organizations become comfortable — and complacent — with their security solutions; but in today’s landscape, it is more imperative than ever to stay on top of solutions, lean on automation, and help your solutions do more for you.
Evolving Landscape
The treat landscape is constantly evolving and even more so in today’s climate. Advanced Persistent Threats (APTs), nation states, organized crime and mischievous individuals continue to increase their level of sophistication and the complexity of attacks. To combat this, organizations and security professionals need to evolve their strategy. We cannot solely rely on disparate solutions that protect the endpoint, the email system, identity and so forth. We need an intelligent, automated, and integrated security solution that works across platforms, cloud services and on-premises. An innovative approach of Extended Detection and Response (XDR) has been defined by the industry analysts to deliver this capability but what exactly is this?
Microsoft Defender
Microsoft Defender and Azure Sentinel make up Microsoft’s XDR solution and there are a few components. First is Microsoft 365 Defender. Microsoft 365 Defender is the XDR solution that delivers intelligent, automated, and integrated security solution for identities, endpoints, email, cloud applications, and documents. Microsoft Defender (formerly known as Microsoft Threat Protection) is made up of the following technologies:
- Microsoft Defender for Endpoints (formerly known as Defender ATP (Advanced Threat Protection)
- Microsoft Defender for Identity (formerly known as Advanced Threat Analytics/Protection)
- Microsoft Defender for Office 365 (formerly known as O365 ATP)
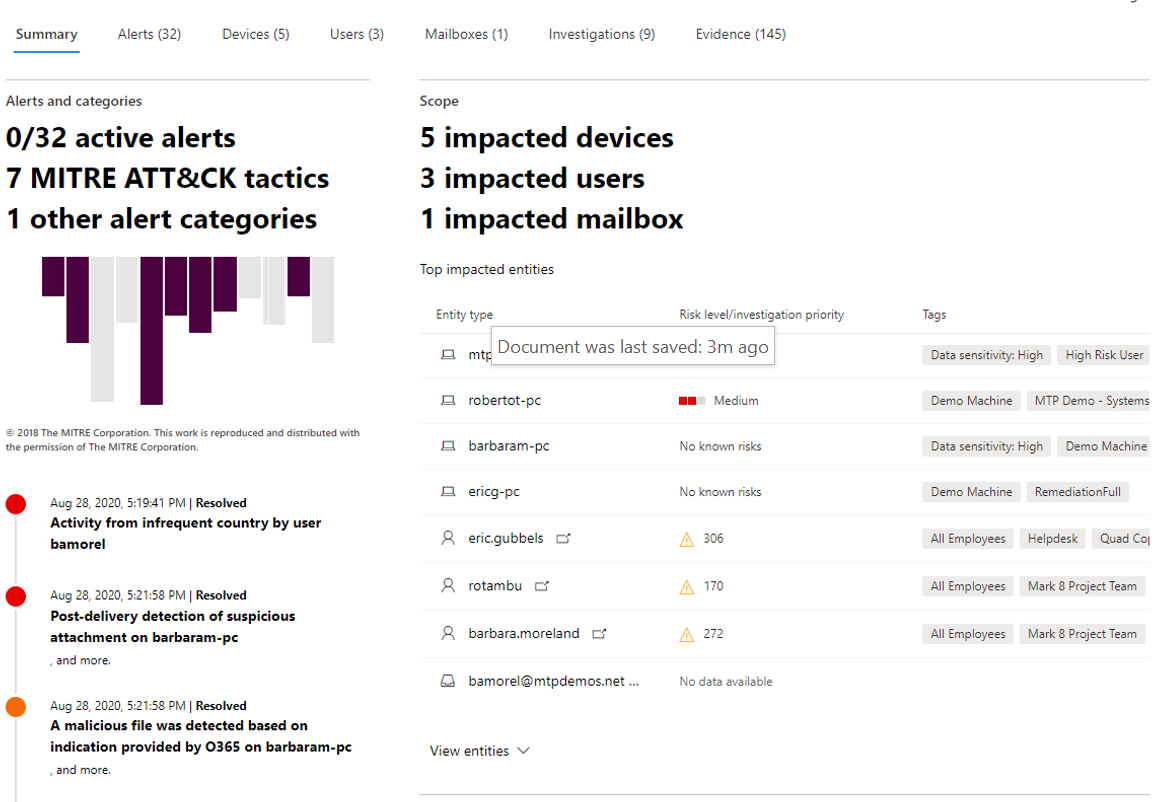
Another part of the solution is Azure Defender. Azure Defender is the XDR solution that protects cloud, multi cloud, and hybrid workloads from virtual machines to IoT (internet of things) solutions, databases and more. Azure Defender is made up of the following technologies:
- Azure Defender (formerly known as Azure Security Center Standard)
- Azure Defender for IoT (formerly known as Azure Security Center for IoT)
- Azure Defender for SQL (formerly known as ATP for SQL)
Having spoken to many customers over the past few years, some of the big challenges most of them face are the sheer number of disparate solutions and the lack of integration of those solutions. Surveys have shown that most organizations with over 1000 people have up to 70 different security solutions from 35 different vendors. This increases costs and requires an immense number of human resources to manage. By simplifying your security infrastructure and using ML (machine learning) and AI you can decrease costs, decrease your risk, and increase your ability to respond to issues promptly.
Cloud Based SIEM
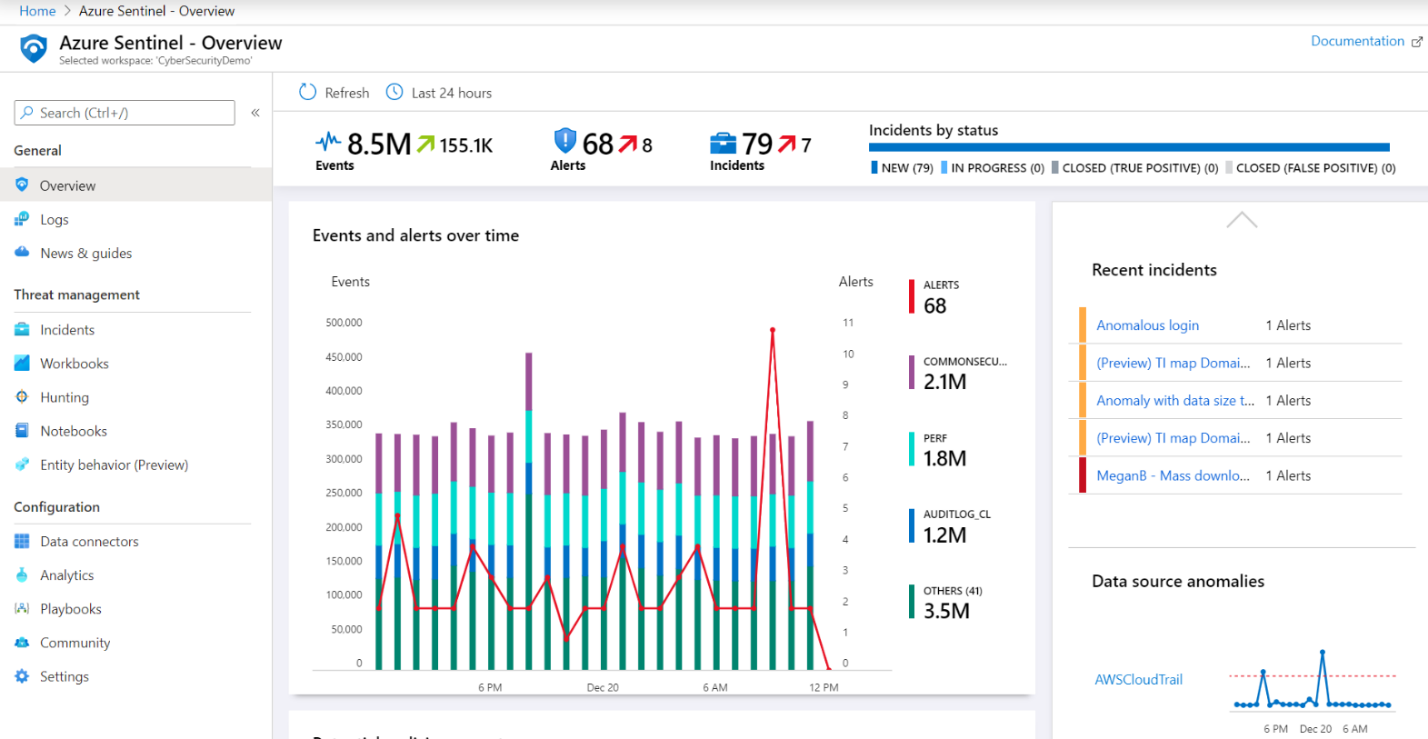
The XDR solution delivered by Microsoft supplies an intelligent, automated, and integrated security solution that works across platforms, cloud services and on-premises that I previously mentioned. However, to truly extend the capabilities, organizations need a solution that can add visibility from other security solutions such as your firewalls, proxies, endpoints, and third-party security solutions. This allows you to have the threat signals from multiple entry points combined into one view that correlates the alerts into incidents and leverages AI (artificial intelligence) to automatically mitigate and remediate the base level issues allowing you and your SOC (security operations centers) team to focus on the more complex tasks.
Azure Sentinel is a cloud-based Security Information and Event Management (SIEM) solution that combines the alerts and insights from Microsoft 365 Defender and Azure Defender with the intelligence gathered from its log collection and analytics to supply a deeply integrated XDR solution that can span all your endpoints, datacenters and cloud services bringing all your security intelligence into one unified protection solution. Again, more data means more exact machine learning algorithms and more exact identification and correlation of alerts into incidents.
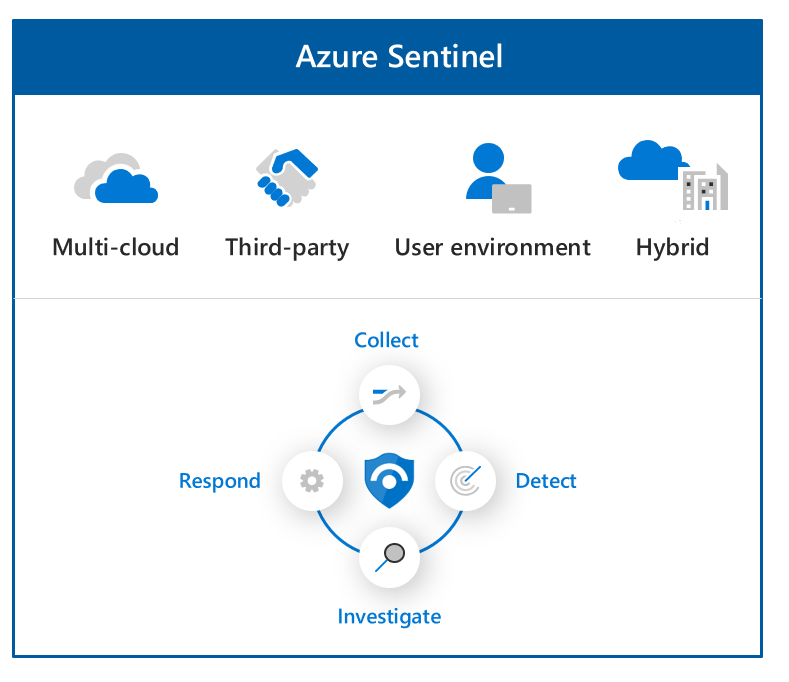
Unified Protection
While there are several XDR solutions in the market and even more SIEM solutions, no one vendor supplies as deeply integrated solutions than Microsoft. Microsoft’s solutions give you the full end-to-end visibility needed to supply actionable insight into your complete enterprise landscape. This integration supplies leading-edge machine learning and artificial intelligence capabilities to add one more phase to the Collect, Detect, Investigate and Respond lifecycle which is to Protect.
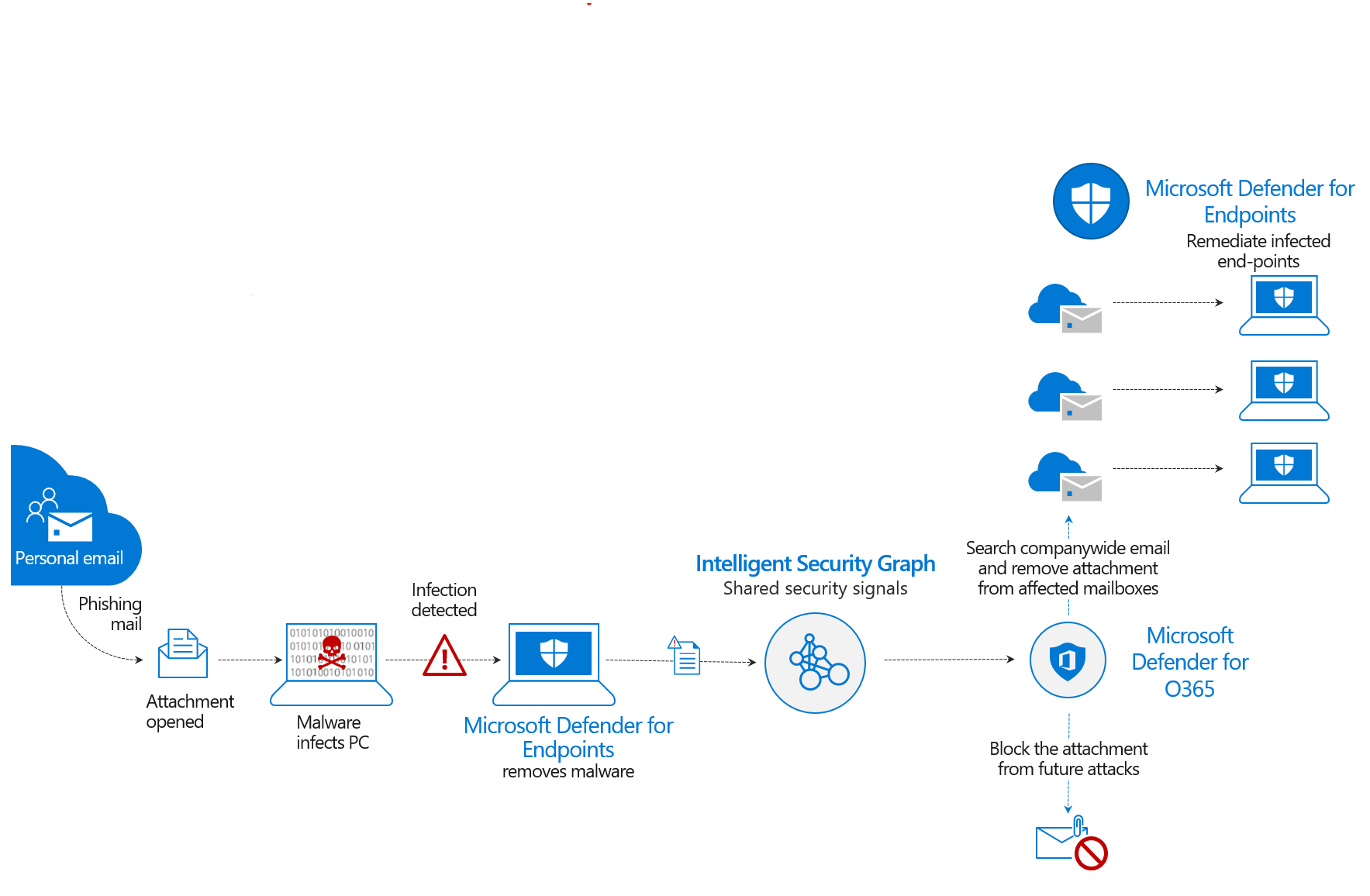
In the protect phase the intelligence gathered in the first phases can be used by AI to reach into the integrated solutions to stop an attack before it happens. An example of this is a user opening an attachment from their email service and having their machine compromised. While Microsoft Defender for Endpoints and your SOC remediates that system, the intelligence is shared with Office 365 to soft delete any attachments with a matching file hash. While at the same time, the solution is automatically blocking that file from making its way into your environment and thanks to the power of the cloud blocking attachments with that same file hash from other Office 365 tenants. That is the power of a unified XDR and SIEM solution.
To keep up to date with our announcements around security, please visit our blog website here: https://www.microsoft.com/security/blog/
Got more thoughts about anything in this newsletter?
Email us at [email protected]!
Tell all your friends about WServerNews!
Please let all your friends and colleagues in the IT profession know about our newsletter. Tell them our latest issues can be found at wservernews.com while older issues dating back to 1997 can be found in our archive. And let them know also that they can receive WServerNews each week in their inbox by subscribing to it here. Thank you!
Tip of the Week
>> Got any IT pro tips you’d like to share with other readers of our newsletter? Email us at [email protected]
ALERT: Malware protection on Big Sur
If you plan on upgrading your Apple systems to macOS version 11.0 code-named Big Sur, you need to consider how to keep your system from malware. My IT colleagues who work with Macs in their environment tell me they recommend Integro for endpoint protection of Macs in enterprise environments. He said that the changes Apple has made to macOS in Big Sur have impacted the ability of much older antimalware software to work properly because of direct calls to the OS that are now blocked in Big Sur. And another colleague whose company is a Sophos Partner has already received warnings that Sophos Endpoint protection isn’t compatible with Big Sur. Things may have changed by the time you’re reading this tip, but be sure to check with your antimalware vendor before upgrading your machines to Big Sur.
Admin Toolbox
>> Got any admin tools or software you’d like to recommend to our readers? Email us at [email protected]
Does your company need to meet compliance requirements? If so, you should consider having a look at email archiving to keep your emails available and retrievable in the long run. We recommend MailStore Server:
DNSQuerySniffer is a tiny network sniffer which detects and displays DNS queries as they’re sent on your system:
http://www.downloadcrew.com/article/30341-dnsquerysniffer_64-bit
FluentFTP is an FTP and FTPS client for .NET & .NET Standard, optimized for speed:
https://github.com/robinrodricks/FluentFTP
Homedale is a portable free tool which detects nearby wireless access points, displays their details, and plots signal strength over time:
http://www.downloadcrew.com/article/32173-homedale
Factoid – This space for rent
Our Factoid section will return in January after the Holiday Season break.
Subscribe to WServerNews!
Subscribe today to our WServerNews newsletter and join 200,000 other IT professionals around the world who receive our newsletter each week! Just go to this page and select WServerNews to receive our monthly newsletter in your inbox!
Conference Calendar 2021
>> Got an IT conference or event happening that you’d like to promote in our newsletter? Email us at [email protected]
NOTE: Conference dates and locations (real/virtual) are subject to change
Microsoft Ignite — March TBD (virtual)
https://myignite.microsoft.com/home
Microsoft MVP Global Summit — March TBD (virtual)
https://mvp.microsoft.com/summit
Black Hat Asia — May 4-7 (location TBD)
https://www.blackhat.com/upcoming.html#asia
RSA Conference — May 17-20 in San Francisco
https://www.rsaconference.com/usa
Black Hat USA — Jul. 31-Aug. 3 in Las Vegas
https://www.blackhat.com/upcoming.html#usa
DEF CON 29 — Aug. 5-8 in Las Vegas
VMworld — Aug 30-Sept 1 in San Francisco
https://www.vmworld.com/en/index.html
Black Hat Europe – Dec 7-10 (virtual)
https://www.blackhat.com/upcoming.html#europe
Cisco Live Melbourne — Dec 7-10 in Melbourne, Australia
https://www.ciscolive.com/apjc.html
Podcast Corner
Our Podcast Corner section will return in January after the Holiday Season break.
New on Techgenix.com
Deploy Windows from the cloud to on-premises hardware? Yes, you can
Wouldn’t it be nice if you could deploy Windows from the cloud while sipping an iced cinnamon dolce latte at your favorite Starbucks?
https://techgenix.com/deploy-windows-from-the-cloud/
SmartDeploy: A simple solution for deploying Windows from the cloud
The cloud is now ubiquitous, and soon deploying Windows from the cloud will also be ubiquitous. This is where SmartDeploy comes in.
https://techgenix.com/smartdeploy-deploying-windows/
Creating bootable ISO files for Windows 10 the easy way
Microsoft has simplified the process of creating bootable ISO files, and we show you the easiest ways to create them for Windows 10 and Windows PE.
https://techgenix.com/creating-bootable-iso-files/
Deploying fully patched Windows 10 computers: A guide for IT pros
Every IT pro has at one point deployed Windows PCs. But deploying fully patched Windows PCs is another issue. Here are some ways to do it
https://techgenix.com/deploying-fully-patched-windows-10-computers/
Always On VPN configuration in Windows 10 using Microsoft Intune
If your organization is looking for advanced security features and modern management support, Windows 10 Always On VPN is something you should consider.
https://techgenix.com/always-on-vpn-configuration/
Fun videos from Flixxy
World’s Deepest Swimming Pool
Free-diving world champion Guillaume Néry exploring the world’s deepest swimming pool – “NEMO 33” in Brussels.
https://www.flixxy.com/worlds-deepest-swimming-pool.htm
Fake Swimming Pool
Fake swimming pool installation by artist Leandro Erlich at the 21st Century Museum of Art, Kanazawa (Japan).
https://www.flixxy.com/swimming-pool-art.htm
Funny Japanese Olympic Swim Team Commercial
The Japanese swim team has come up with a new strategy to win the gold medal in the Summer Olympics.
https://www.flixxy.com/funny-japanese-olympic-swim-team-commercial.htm
Family Of Bears Play In Backyard Swimming Pool Home Daily Popular
A mother bear and her five cubs decided to beat the sweltering heat by taking a dip in a backyard swimming pool in Rockaway Township, New Jersey, USA.
https://www.flixxy.com/family-of-bears-play-in-backyard-swimming-pool.htm
More articles of interest
Infrastructure as code examples for DevOps, cloud deployments
Administrators can use infrastructure as code to consistently manage a distributed set of resources. Follow these four examples to get started and explore common IaC tool choices.
How to calculate VDI costs and keep them to a minimum
When the true cost of VDI is hazy, it’s a good idea to make a comprehensive calculation. Determine how to factor in costs related to hardware, infrastructure, licensing and more.
5 WSUS alternatives for patch management
Compare the features and functionality of five prominent patch management tools for Microsoft and third-party applications to find the right option for your organization.
Compare AWS CloudEndure vs. Azure Site Recovery services
Learn how DRaaS heavyweights AWS CloudEndure and Microsoft Azure Site Recovery compare when it comes to architectures, features, integrations, pricing and other considerations.
Send us your feedback!
Got feedback about anything in this issue of WServerNews? Email us at [email protected]