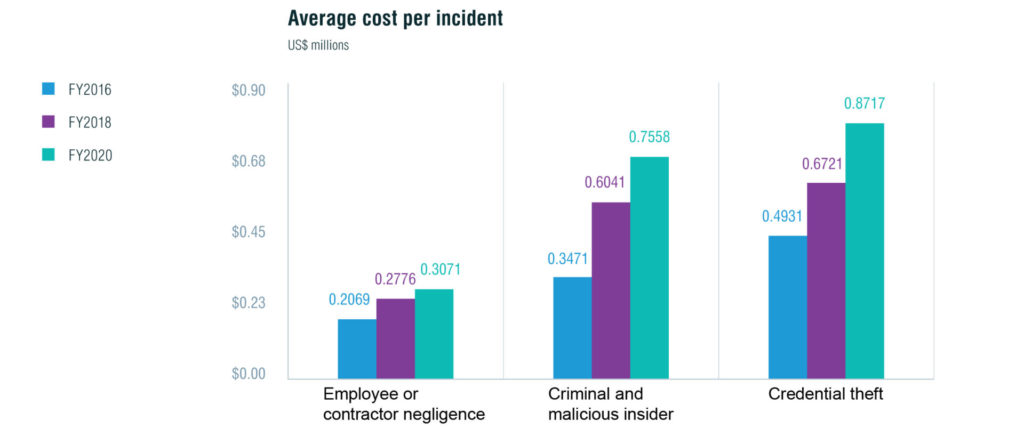
Do you know that between March and July 2020, a whopping 43 percent of security incidents reported were by malicious insiders? So, why do they do it? For a variety of reasons, ranging from financial to fun! Regardless of the motive or reason of employees to indulge in a security incident, the costs that come from it are huge for any organization. As the chart below shows, the cost of security incidents has been steadily increasing over the last few years and is expected to follow this trend for the upcoming years as well. All these sure look scary. So, what can you do as an organization to avoid this threat? Well, many strategies must be used in tandem, and one such strategy we’ll explore in this article is Zero Trust.
What is a Zero Trust?
At the heart of this strategy is the elimination of trust from the organization. In other words, it is based on the belief that an organization should trust no one and must verify the credentials of every entity that tries to access its resources.
Here, an entity includes not just individuals but also devices and IP addresses, regardless of where they are located.
This is a stark contrast to the traditional castle and moat approach used by organizations to implement security. In this traditional system, it is hard for outsiders to enter the network, but entities within the “castle” or network can access the resources.
But obviously, this is a flawed concept given the growing number of insider attacks. So, John Kindervag, a principal analyst at Forrester, created this Zero Trust model in 2010. Today, many organizations have adopted it to beef up their networks and resources because it effectively reduces insider attacks.
Implementing Zero Trust
So, now comes the big question — how to implement Zero Trust in your organization?
Well, there is no single tool, and it relies on a combination of many technologies and tools to secure the IT environment. To a large extent, the choice of tools and technologies depends on the existing system’s size and architecture.
That said, let’s look at some of the technologies used for implementing this Zero Trust.
Zero Trust and multifactor authentication
A common technology used across organizations is multifactor authentication, which uses more than one piece of evidence to verify the identity of a user and allow appropriate access to the required resources.

Most times, the user is asked to enter a password and a code sent to the associated email address or mobile number. This way, there is a minimum of two pieces of evidence to identify the entity requesting access.
User access control
Another important pillar of Zero Trust is restricting access to devices. In other words, the organization has to implement controls on user access and must track the number of devices accessing a network and the number of devices or resources accessed by individuals at any time.
An organization has to implement security policies that restrict both the above aspects to just the resources required.
There are many ways to implement this user access control, and they are:
- Mandatory access control.
- Role-based access control.
- Discretionary access control.
Microsegmentation
Microsegmentation is a helpful way to reduce lateral movement of access. When you establish micro-perimeters within the system, they act as borders to prevent unauthorized access to the resource.
This segmentation can be done based on groups, location, or even a logical arrangement of applications. The advantage of this technology is that it moves as the segment moves.
Monitor the network
Monitor the network continuously using the right monitoring tools, so you can catch unauthorized access and threats before they impact your network or resources.
Put in place tools that can continuously inspect, analyze, and log all the traffic that passes through your network.
Least privilege principles
This principle revolves around giving the least access to the most critical resources. So, identify the critical resources first, and reduce the access you give to devices and individuals.
Encryption
We all know what encryption is and its benefits, but not every organization implements it completely. A report by Skyhighnetworks shows that only 9.4 percent of cloud providers are encrypting the data at rest, and this could explain why one in three networks have exposed passwords while 72 percent have poor control over access privileges.

To avoid this problem, make sure to encrypt your data, both during transit and at rest.
Scoring
Another good way to prioritize securing the resources is to use scoring. A trust engine leverages data from multiple sources to compute a risk score, a number similar to a credit score, for authorization purposes.
Obviously, entities with a low score have more restricted access than those with a high score. Also, this score is continuously evaluated and monitored.
Analytics
Analytics is a central part of any monitoring system, and more so for Zero Trust because you must monitor and analyze the resources at all times to ensure that they are within your security policy. In fact, it can tell you what’s wrong where, so you can fix it right away before it balloons into a major threat.
Identity access management
Identity access management (IAM), which has become a hot field in cybersecurity, is a central part of implementing Zero Trust as it gives users access to the right resources that can be accessed from anywhere while maintaining tight and controlled security. This way, employees have more flexibility to work from anywhere while organizations still have complete control over security.
Policies and procedures
Needless to say, policies and procedures are the heart of Zero Trust implementations as they define the who, why, when, what, and where aspects of accessing a resource.
You can use one or more of these strategies to implement a Zero Trust policy in your organization.
While this is not an exhaustive list, it is sure to give you an idea of how to implement Zero Trust in your organization.
Using these tools, you can come up with a broad strategy for implementation that includes,
- Identifying the sensitive information or the resources you want to protect.
- Understanding the flow of information or the use of resources within your organization.
- Defining the Zero Trust strategy with its micro perimeters.
- Using the right tools and technologies to implement your strategy.
- Continuously analyzing and monitoring for potential threats and loopholes.
- Using automation and other safety orchestration measures to identify and handle threats.
Challenges
As you have guessed, many challenges come with implementing Zero Trust within your organization. While the exact challenges may vary depending on the pertinent factors, here are a broad set of challenges to expect.
- The presence of legacy apps and devices may impede the use of modern technologies to implement a Zero Trust policy.
- It can be expensive to implement, especially if you have to make huge changes to the underlying architecture.
- Some regulations have not adopted Zero Trust, so if your organization has to comply with any of these regulations, it may be difficult to implement Zero Trust.
- It is extremely difficult to establish fine control and visibility over every resource, and this challenge exacerbates with size. In general, the larger the organization, the lower could be the control and visibility. As a result, implementing Zero Trust may be a challenge.
- Requires continuous and ongoing effort that requires more time, effort, and money.
- Involves a change in mindset across the entire organization for effective implementation.
Tips and tricks
Here are some tips and tricks to implement a Zero Trust policy in your organization.
- As a first step, assess the existing policies in your organization to get an idea of the implementation. Specifically, do an inventory of the different resources and the access controls associated with each.
- Make a list of the most critical and vulnerable resources, and ensure strict access controls are maintained for them.
- Create a directory of all the resources to make it easy for you to map the transaction flows that happen among them.
- Use a combination of strategies, and don’t rely on a single tool or technology to implement Zero Trust security.
- Monitor continuously and improvise as needed.
- Educate your employees on the need for such stringent measures.
Zero Trust: A crucial security strategy
A Zero Trust strategy is becoming an essential part of every organization as it tries to balance remote working with a robust security framework. At its heart is the concept of trusting no one to access a resource and checking and authorizing every user or device.
Since it is fairly complex and involves many layers, it is best implemented with a combination of strategies that are monitored continuously for pitfalls, so it can be beefed up to provide top-notch security for an organization’s resources.
Featured image: Pixabay



