Server message block signing, or SMB signing for short, is a Windows feature that allows you to digitally sign at the packet level. This security mechanism comes as a part of the SMB protocol and is also known as security signatures.
Why is this signing necessary?
It is needed simply because digital signing helps recipients to confirm the origin and authenticity of the incoming packet. In the process, it eliminates any kind of tampering and “man-in-the-middle” kind of attacks. Overall, it makes your packets more secure during transmission.
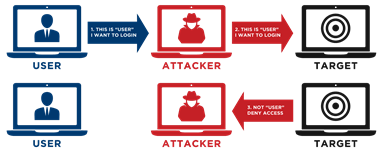
This feature was introduced in Windows 2000 and since then, it’s being supported by all versions of Windows operating systems. However, it’s enabled by default only on domain controllers. If you’re wondering why it’s enabled on domain controllers, it’s because SMB is the protocol used by clients to download group policy information, and SMB signing ensures that this information is from a genuine source and authentic.
SMB signing versions
There are two versions of SMB signing. The first version, referred to as SMB1 signing, applies to Windows 98, Windows NT 4.0, Windows 2000, and Windows 2003 servers. The second version, called SMB2 signing, was introduced for Windows Vista and Windows Server 2008 and beyond.
We’ll see how to configure in each of these versions.
Configuring Windows SMB1 signing
All Windows versions support SMB signing, so you can configure it on any version. However, SMB signing should be enabled on both the computers in the SMB connection for it to work. By default, SMB signing is enabled for outgoing sessions in the following versions.
- Windows Server 2003
- Windows XP
- Windows 2000
- Windows NT 4.0
- Windows 98
By default, SMB signing is enabled for incoming sessions in the following versions.
- All Windows Server 2003-based domain controllers
- All Windows 2000 Server-based domain controllers
- All Windows NT 4.0 Server-based domain controllers
So, you’ll have to configure those versions where SMB signing is not enabled by default.
Group policies are a good and recommended way to configure SMB signing because a local registry value change doesn’t work well if it is different from the overriding domain policy. This is why we don’t recommend changing the registry value directly.

Let’s now look at the group policies you’ll have to change.
Policy #1
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\LanManWorkstation\Parameters
- Group policy name — Microsoft network client: digitally sign communication (if server agrees).
- Value name — EnableSecuritySignature
- Data type — REG_DWORD
- Default values — 0 is disable and 1 is enable. In Windows Server 2003, Windows XP, and Windows 2000, it is enabled by default.
Policy #2
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\LanManWorkstation\Parameters
- Group policy name — Microsoft network client: digitally sign communication (always)
- Value name — RequireSecuritySignature
- Data type — REG_DWORD
- Default values — 0 is disable and 1 is enable. In Windows Server 2003, Windows XP, and Windows 2000, it is disabled by default.
Policy #3
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\LanManServer\Parameters
- Group policy name — Microsoft network client: digitally sign communication (if client agrees).
- Value name — EnableSecuritySignature
- Data type — REG_DWORD
- Default values — 0 is disable and 1 is enable. In Windows Server 2003, Windows XP, and Windows 2000, it is enabled by default. In Windows NT 4.0, it’s disabled by default.
Policy #4
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\LanManServer\Parameters
- Group policy name — Microsoft network client: digitally sign communication (always)
- Value name — RequireSecuritySignature
- Data type — REG_DWORD
- Default values — 0 is disable and 1 is enable. In Windows Server 2003, Windows XP, and Windows 2000, it is enabled by default while in Windows NT 4.0, it’s disabled by default.
In addition to these parameters, you have to create a new registry value in Windows 2000-based computers to connect them to Windows NT 4.0 through SMB signing. The parameter is: All of these above settings should be set to “enabled” for SMB signing.
Value: enableW9xsecuritysignature
Data type — REG_DWORD
Data: 0 is disable and 1 is enable.
There is no group policy associated with this value.
Configuring SMB2 signing
SMB2 signing is a greatly simplified version of SMB1, as it uses a new hashing algorithm called HMAC SHA-256 that replaces the old one called MD5. So, you’ll have to configure only one setting, and that’s whether the signing is required or not. You can configure this either through group policy or registry setting on both SMB2 clients and servers.
SMB signing scenarios
After you change the above configuration values, here are the possible scenarios.
To start off, if SMB signing is enabled and required in both the client and server or if the SMB is disabled both in the client and server computers, then the connection is successful. This is also what you need for a successful signing session. Of course, there’s no signing if the values are disabled in both the client and server.
On the other hand, if the signing is enabled and required at the client side, but disabled on the server, or if the signing is disabled in the client, but enabled and required in the server computer, then the connection will fail. In the first scenario, the client gets a “ERROR_LOGIN_WKSTA_CONNECTION” error while in the latter scenario, the client gets a “STATUS_ACCESS_DENIED” scenario.
You’ll have to change the statuses according to the message for SMB signing to work.
SMB signing behavior
The client and server communicate during an SMB signing, and in case of incompatibility, it throws up the above errors.
This signing behavior is slightly different if you’re using an old version of SMB1, and that’s because older versions like Windows 98, Windows 2003 server, and Windows XP, had a different signing behavior. This behavior, however, was changed in 2008 to keep it in tune with the behavior in Windows 2008 and Vista.
So, if you have an older version, you should patch or update it to remove misconfiguration.
This could bring up an interesting question, which is, can anyone change the SMB signing behavior?
In general, keep the default SMB signing settings. But you can also reconfigure this signing setting in certain situations, like the ones below.
- Since SMB signing requires extra processing resources for hash calculations, you can choose to disable the “required” setting on domain controllers, especially if you’re running low on resources. However, this could open your group policy to possible tampering.
- You can also disable the “required” setting on your domain controllers if you want to use WAN optimization devices to speed up traffic between offices located in different cities or countries.
- You can enable the “required” setting on all SMB clients and servers, so all your SMB traffic is signed. However, this is also not recommended because it’ll decrease SMB performance as more resources are needed.
When you change the default behavior, it’s best to do it through group policy settings instead of changing the registry values.
Overall, SMB signing adds an extra layer of security as it eliminates the possibility of tampering or man-in-the-middle attacks during a communication. It’s also easy to implement since all Windows version support it in some form.
Have you used SMB signing? Please tell us your experience in the comments section.
Photo credit: Pixabay




Are you just republishing a 15 year old article? There is no mention of any OS beyond Windows 2000 or of SMB3.
P.S.: A quick note on SMB3
While there are changes in the crypto used in SMB3 for signing (SMB3 uses AES-CMAC for signing instead of HMAC SHA-256 in SMB2), the overall SMB2 behavior described in this blog also applies to SMB3.
Source: https://blogs.technet.microsoft.com/josebda/2010/12/01/the-basics-of-smb-signing-covering-both-smb1-and-smb2/
i think its good to read it again as many organization dont implement it in their environment.
if we dont have win xp/2003 and want to implement on whole domain should we apply it on default domain policy under computer configuration ?
@movi, then you don’t need to do anything. Read the article, all modern Windows operating systems will default to using SMB signing.
Peter, i dont think its default to use smb 2 signing. We need to enable them to use it.