If you would like to read the next part in this article series please go to Protecting System Files with UAC Virtualization (Part 2).
When a standard user is logged into a Windows based computer, there are certain activities and actions that need to be protected. This protection is not always successful, as some versions of Windows do not protect the overall system as much as anyone would hope. Actions that need to be protected is the modification or writing to system folders and system locations in the Registry. This is essential to protect the overall stability and security of the operating system. Windows Vista provides an excellent solution to help protect these key system areas. Vista uses User Account Control and Virtualization to accomplish the security and protection. This article discusses and exposes how UAC uses Virtualization to protect the system.
Historical Line of Business Application Behavior
The Program Files directory (typically located at C:\Program Files and referred to as %ProgramFiles%) is where most LOB applications store the executable files for the application. The settings for the LOB application are stored under the HKEY_LOCAL_MACHINE\Software key in the Registry in most cases. Both of these locations are protected by the operating system by only allowing the system and administrators write access, where users have read and execute access only.
LOB applications should be designed to write to the user specified application data folder, which is located under the user profile. This is typically located at C:\Users\<username>\AppData and referred to as %AppData%. If there are user specific settings that need to be stored, these should be located in the Registry at HKEY_CURRENT_USER\Software. Both of these locations are created on a user by user basis and are protected such that only that user has access to the data that is written by default.
However, many (might I say MOST) LOB applications are not designed to work this way. Instead, they are designed to store user specific data under %ProgramFiles% and HKEY_LOCAL_MACHINE\Software. Unfortunately standard users do not have access to write to these locations, which has caused many companies to add standard users to the local Administrators group in order to run these applications. Of course, this is not ideal, as the user now can modify anything on the computer, not just the LOB application specific changes to these locations on the system.
UAC Virtualization Specifics
Since the LOB applications are not easily changed and users must still run these applications, Vista takes a different approach to fix the problem. Within Vista, UAC lends a helping hand by virtualizing the file system and Registry namespace. UAC will virtualize legacy applications, allowing standard users to remain a “standard user”, but still run the application. The definition of legacy in this case includes processes that are 32-bit, not running with administrative privileges, and does not include a Windows Vista manifest file. If a process or operation does not meet these criteria it is not virtualized. Additionally, the following processes and operations are not virtualized:
- Default Vista applications
- Files with executable extensions, such as .EXE, .BAT, .VBS and .SCR. You can add additional file extension exceptions in HKLM\System\CurrentControlSet\Services\Luafv\Parameters\ExcludedExtensionsAdd
- 64-bit applications and processes
- Applications with a requested Execution Level directive in their executable manifest, like most Vista executables
- Processes or applications running with administrative rights
- Kernel mode applications
- Operations not originating from an interactive log-in session, like file sharing
- Applications modifying a registry key marked with the Don’t_Virtualize registry flag
Virtualization of the file system and Registry is not system wide, of course. There is a limited number of locations that are virtualized, all of which are essential for the operating system to run and to be kept secure. Here is a near-complete list of locations that are virtualized:
- \Program Files and subfolders
- \Program Files (x86) on 64-bit systems
- \Windows and all subfolders, including System32
- \Users\%AllUsersProfile%\ProgramData
- \Documents and Settings (symbolic link)
- HKLM\Software
Verifying UAC Virtualization
When an action is virtualized, the resulting content is stored within the users’ profile as mentioned above. However, how do you really know that the information has been virtualized? Depending on which content has been virtualized, there will be some indicators within the different interfaces to help you see the virtualization.
The first indicator will be within the Windows Explorer GUI. Depending on which folder and files have been virtualized, you will see additional menu options within Windows Explorer. Figure 1 illustrates what Windows Explorer shows when you have Virtualized files under the C:\Windows folder.
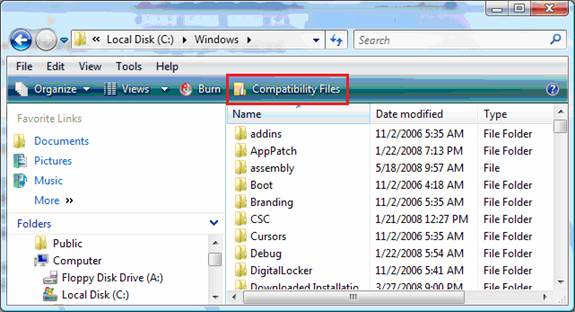
Figure 1: The highlighted red box indicates that there are virtualized files
The “Compatibility Files” menu addition to Windows Explorer only appears when there are files that have been virtualized. The new menu option appears only for those folders which have virtualized files or folders.
When the Compatibility Files menu option is selected, it will direct the Windows Explorer window to the virtualized files and the containing folder. Figure 2 illustrates what the contents of this virtualization of files and folders looks like.
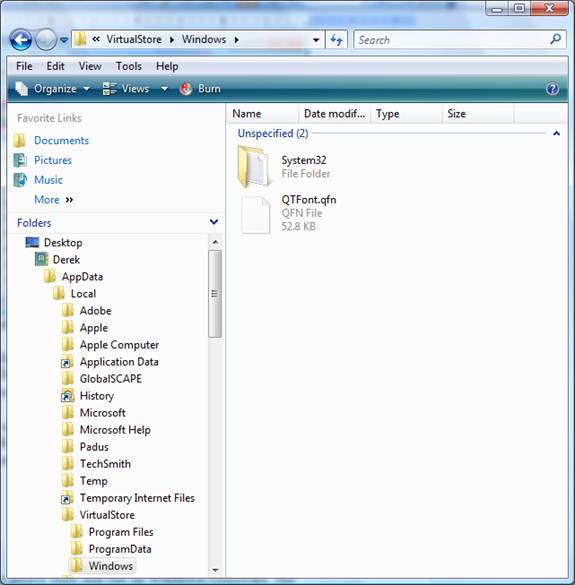
Figure 2: The Compatibility Files menu option is stored under the VirtuaStore folder
As you can see, the Compability Files menu option opens up the VirtualStore folder, which is located under the users’ profile. As you can see in the Figure 2, it is <username>\AppData\VirtualStore.
Summary
Everyone knows that applications are poorly built that run on Windows computers. The main reason for this is that applications write to protected system files, folders, and Registry locations. This requires users to be local Administrator or for another solution to be put in place. Placing user accounts into the local Administrators group to have the user successfully run their applications is not a good solution in any way. Depending on how the application is designed, UAC virtualization of files and Registry is an excellent solution. The files and Registry entries that are meant to go into these protected system locations are just virtualized, being placed in the user’s own personal profile. This helps protect the system, the network, and still allows the user to run the application.
If you would like to read the next part in this article series please go to Protecting System Files with UAC Virtualization (Part 2).





Hello, in the latest windows 10, version 1909, UAC Virtualization does show up in the Task Manager but in that column, everything shows up as blank, or disabled, or not allowed. In the windows file explorer, things have changed so much that I could not figure out how to do what you did. Could you update this for windows 10? I would appreciate it.