Data breaches are occurring everywhere, from the smallest companies to giant enterprises to even presidential elections. And not only are they becoming more frequent, they are becoming more expensive. A Ponemon Institute report estimated that the average cost of a data breach rose from $3.8 million in 2015 to $4 million in 2016. That cost is expected to rise again this year. With attacks coming from all angles, how can a CIO prepare? Let’s look at some of the most likely vectors for attack and what can be done to identify the threats.
Open source and cloud applications have proliferated down to even startup businesses. These come with a fair share of benefits and risks. A datacenter attack or outage can literally black out a company’s web applications and websites, and cyberattacks can compromise valuable financial and confidential information from the company’s vaults. In light of the speed of technological transformations being witnessed across enterprises, CIOs have their jobs cut out for them, trying to maintain security readiness and disaster preparedness. All’s not easy, however.
Cybersecurity: A CIO’s biggest nightmare
What is one persistent problem that’s preventing successful implementation countermeasures to cybersecurity threats? Believe it or not, it is often the lack of competency on the part of many CIOs. Historically, the role of the CIO was restricted during the 1980s to being focused on technical projects. This has broadened over time, but the updating of the requisite skill sets has not always kept up. What’s more, the penetration of technology into all businesses — even those considered to be nontechnical businesses — has placed further demands on CIOs to expand their expertise into previously unknown territories, especially in the realms of cybersecurity.
This has proven to be a liability in terms of enterprise security, as adequate measures have not always been taken. Sometimes, the company itself fails to assign the required resources to train staff toward achieving their security goals, not considering it important enough or too expensive. According to a CompTIA survey, HR professionals of only a third of U.S. organizations insisted on cybersecurity awareness training.
Recognition of cybersecurity threats and using the latest and best tools and technologies that help enterprises stay safe is the first step for the modern organization’s CIO. Here is a sneak peek at some mounting cybersecurity threats.
Vulnerability of IoT
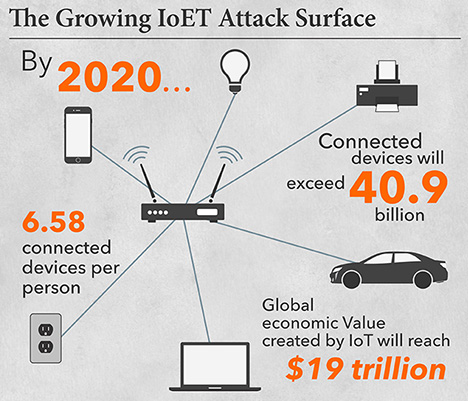
In the rush to expand the coverage and reach of IoT devices, manufacturers and innovators have put security on the back burner. This means that cybercriminals are increasingly looking toward IoT as targets for their nefarious acts. Internet-connected end points such as cameras, home appliances, lighting systems, and surveillance systems are exposed to the threats of distributed denial of service (DDoS) attacks. Gartner predicts that by the end of 2020, 25 percent of identified enterprise attacks will be centered on IoT. For any organizations investing heavily in IoT devices and technologies, a word of advice: Focus on security readiness of these devices, even if the tech industry is not.
Third-party vendor relations that go awry
Nothing makes an organization feel more powerless than to face the catastrophe of a data leak, network hack, or downtime because of a security lapse at a connected vendor’s site. The truth is that every organization with IT dependency (which means most organizations) employs and deploys a number of vendors and vendor tools. Vendor contracts and policies around risk management need to be tightened to ensure such events don’t disrupt your organization’s workflow. Bringing vendors up to speed with tech security best practices and diligent scrutiny of vendor operations are key responsibilities for CIOs. American fast food chain Wendy’s learned this the hard way, when a PoS (point of sale) malware attack affected operations at more than a 1,000 franchise locations.
Cybersecurity skill gap
 Shortage of skilled IT security workers has been a real problem for many years, but it has assumed massive proportions because of the rising concerns around cybersecurity. In a report titled Hacking the Skills Shortage, 775 IT decision makers were interviewed, and 82 percent of them agreed that there was a shortage of cybersecurity skills in the market. Additionally, 71 percent said that this resulted in measurable and direct damage to the enterprise. This shortage is spurring new roles, including Chief Information Security Officer as a Service (CISOaaS), an on-demand model that can help companies that don’t have the resources for a full-time chief information security officer.
Shortage of skilled IT security workers has been a real problem for many years, but it has assumed massive proportions because of the rising concerns around cybersecurity. In a report titled Hacking the Skills Shortage, 775 IT decision makers were interviewed, and 82 percent of them agreed that there was a shortage of cybersecurity skills in the market. Additionally, 71 percent said that this resulted in measurable and direct damage to the enterprise. This shortage is spurring new roles, including Chief Information Security Officer as a Service (CISOaaS), an on-demand model that can help companies that don’t have the resources for a full-time chief information security officer.
Email attacks continue to be a menace
Last year we witnessed a growth in sophisticated and effective Business Email Compromise (BEC) attacks involving stolen identities that were then used to inflict damages worth millions of dollars. Such attacks compromised leading global healthcare organizations, the World Anti-Doping Association, and an NBA team last year. The success rates of BEC attacks may be fractional, but when they succeed they inflict severe damages. This has fueled and prompted fraudsters into expanding their bases and attempting more BEC attacks. For enterprises, this demands awareness of how these attacks succeed, followed by adoption of means and ways to stay safe.
Concerns around mobile security
Mobile devices are ubiquitous, even at an enterprise level, which makes them a key target for cybersecurity attacks. Mobile Device Management has traditionally not been a part of IT budget allocation, but that is expected to change very soon. Also, enterprises will need to consider investment in proven effective mobile security vendors who can install mobile threat defense apps on all mobile devices used in the enterprise. Building strong practices around access management and privileges on mobile devices and Bring Your Own Device practices will be a critical aspect of enterprise mobile threat prevention in the times to come.
Cybersecurity has become for many organizations their No. 1 concern. The stakes are unimaginably high, and this demands the utmost attention from IT decision makers, security officers, and CIOs.



