IIS based attacks, like other exploits, try to find code problems with active web content. These attacks try to overload scripts or send them confusing input that looks like code.
Locking down IIS is important but it doesn’t replace other means of protecting your server such a Firewall, a properly updated Antivirus and patching through Microsoft’s Windows Update and Exchange web sites.
The IIS Lockdown tool developed from a basic tool that shut off most of IIS dynamic features to a useful tool offering an improved interface for both beginners and experts. It now offers Server roles that tailor solution for server applications. It has a profile for Exchange 5.5, Exchange 2000, SBS 4.5, SBS 2000 and a no IIS required profile that you can use to secure your Windows 2000 domain controllers.
If you placed your server into appropriate Organizational Units (for example “Exchange Servers” or “Domain Controllers” you can use scripting and unattended installations to secure multiple servers across your organization.
Installation
The IIS Lockdown tool is available at the following link:
The iislockd.exe file is actually a self extracting file you can extract with any decompression utility worth its salt. It contains:
- Documentation about IISLockdown
- Instructions for unattended installations including sample batch file
- IISLockdown tool including INI file you can manipulate
- URLScan tool you can run separately if you want
- URLScan INI files for server roles
Running the Wizard
As you can see in the following screenshot, the lockdown tool can be used to secure all kind of web application. It doesn’t specify Exchange 2003 but can safely be installed when you have Exchange 2003 installed on Windows 2000.
I will go through the Exchange 2000 template settings to explain what is removed.
IIS Components Removal
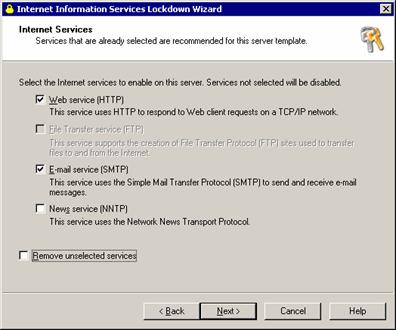
Exchange 2000/3 require the HTTP, SMTP and NNTP components to install. However, the NNTP component is no longer required for exchange operations if you’re not hosting newsgroups on Exchange, which is rarely done. The IIS Lockdown wizard can disable this service but the “Remove unselected services” should be unchecked because the NNTP service is required for service pack installations.
If you don’t disable NNTP you might be receiving from time to time mostly useless events in the Event Viewer.
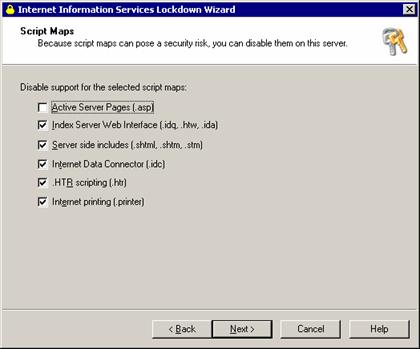
Exchange 2000/3 use Microsoft’s Active Serve Pages technology to publish information though other technologies are supported, but can be safely removed if you don’t host your website on the Exchange machine.
However, some antivirus packages might not be using ASP so you should consult your antivirus vendor.
IIS has some samples and virtual directories that are nice to learn ASP from but are not usefull otherwise and can be deleted. Also, anonymous users should be prevented from running applications or writing information.
WebDAV on the other hand is a technology built on top of ASPs and is used extensively with Exchange.
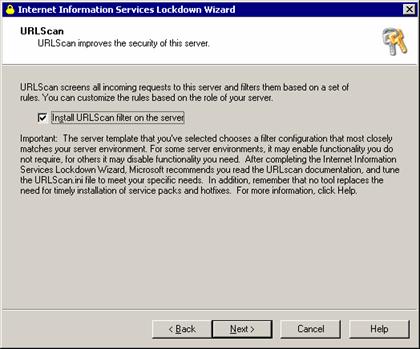
URLScan
The URL Scan utility is a basic form of Intrusion Detection System (IDS). There are more professional IDS systems around that can protect web servers from attacks but you probably don’t need those if you’re not hosting Exchange and are a popular target for attacks.
URLScan tool used to have been a separate download and has since then been integrated to IIS Lockdown. It has the capability most Firewalls now have to repel common IIS attacks. These attacks are identified by their unusual activity. You don’t need to install it if you have an internal Firewall protecting your servers from the network.
The URLScan tool examines every HTTP request before it is handed to IIS, which normally responds by returning the requested HTML file or running the requested ASP page. To do this the URLScan installation registers Urlscan.dll is an ISAPI filter (an internal IIS mechanism that can manipulate web requests). Before a request is allowed through to IIS, URLScan ISAPI filerchecks it for:
- Malformed URLs, such as binary data in the URL
- Attempts to run restricted file extensions such as EXE, HTA, IDA, etc.
- Restricted HTTP Request types. Only GET, POST, and HEAD are needed by most sites.
It can protect you from Nimda and Code red style attacks from the Internet. Always remember that from an Internet perspective an Exchange 2000/3 server is just another web server to attack.
After installation is complete, check to see that all the web pages are still accessible. In case of a problem, running the wizard again enables you to undo the process. If you need to know afterwards what the IIS Lockdown did to your system check out the Oblt-log.log text file saved in the folder that contains IISLockd.exe. This file contains information about every action the IIS Lockdown Tool implemented on the system.
Unattended Installation
To run the IIS Lockdown Wizard automatically you need to edit the iislock.ini file after extracting the file to a directory (see installation section).
To configure the [Info] section of the Iislockd.ini file to run the IIS Lockdown Wizard unattended
- Open Iislockd.ini in a text editor.
- Under the [Info] section, configure the UnattendedServerType setting as follows:
UnattendedServerType= exchange2k / for Exchange 2000
UnattendedServerType= exchange5.5 / for Exchange 5.5
- Change the Unattended setting to TRUE.
Unattended=TRUE
- To disable the NNTP service (since this is not the default) go to the [exchange2k] section and change
Enable_iis_nntp=FALSE
Conclusion
IIS Lockdown is a must utility for Exchange installations on Windows 2000. It should be used cautiously though, tailoring it to a specific server’s needs taking into account other roles it might have and installed applications.